Ransomware attacks on industrial infrastructure doubled in 2022: Dragos
The number of ransomware attacks on industrial infrastructure grew significantly in 2022, according to researchers from cybersecurity firm Dragos.
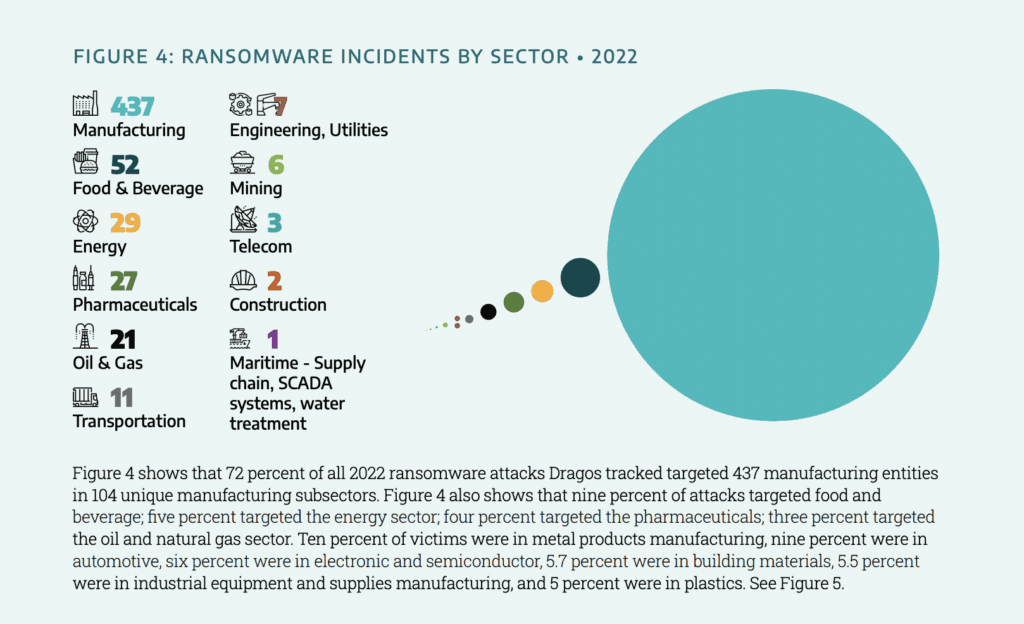
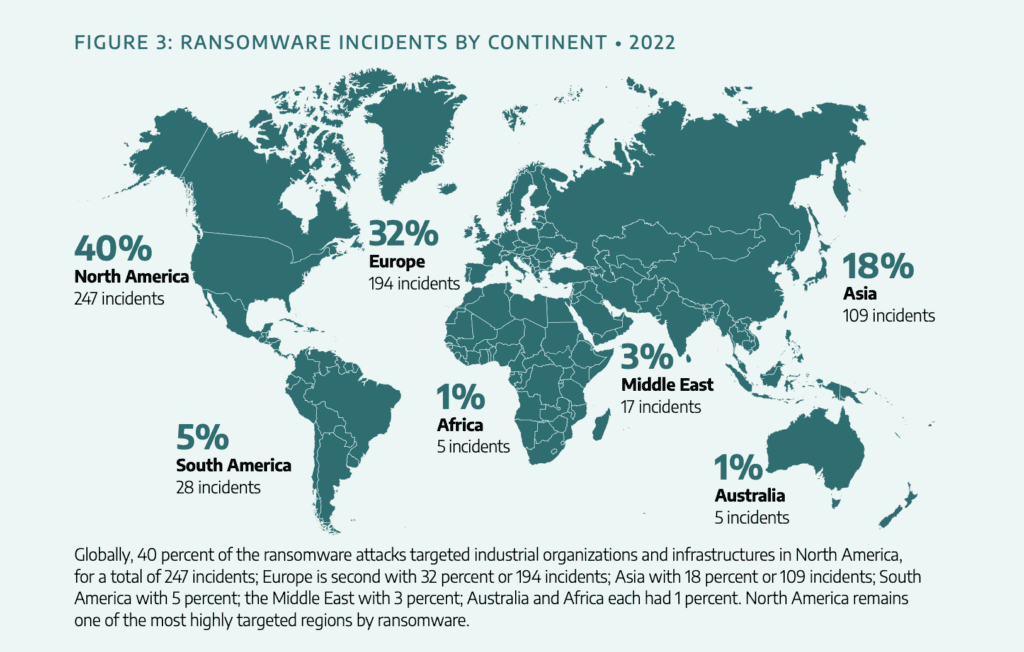
The company tracked more than 600 ransomware attacks last year – up 87% on the year before – with 72% of them targeting the manufacturing sector.
“So they're definitely going after manufacturing. A heck of a lot more than electrical and gas,” Rob Lee, CEO of Dragos, told reporters last week.
Dragos found that there was a 35% bump in ransomware groups specifically targeting operational technology (OT) or industrial control systems (ICS) last year.
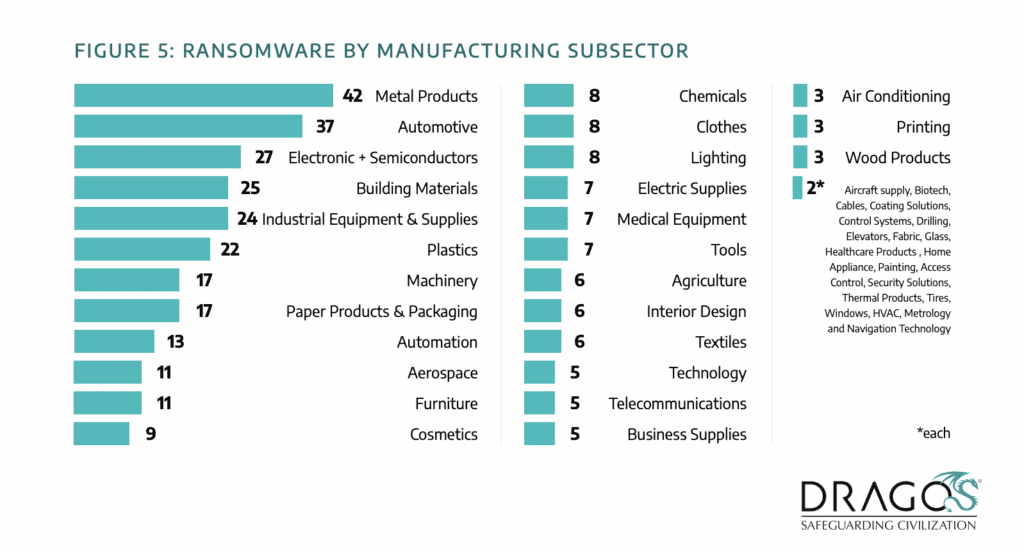
In total, 437 manufacturing entities were hit with ransomware, including 42 attacks on metal products companies, 37 on automotive businesses and more than 20 on plastics, industrial equipment, building materials and electronics or semiconductors companies.
The rest of the list includes dozens of attacks on paper products, automation, aerospace, furniture, cosmetics, chemicals, clothing, medical equipment and more.
Major incidents listed by Dragos include ransomware attacks on Subex, Kojima, AGCO, Foxconn, South Staffordshire Water, DESFA and several attacks on mining and metals companies like Copper Mountain Mining.
LockBit domination
Dragos listed a variety of reasons for the stark increase in ransomware attacks. On one hand, the number of ransomware groups and sophistication of tools are increasing rapidly. After the downfall of the Conti ransomware group, several others have stepped up to take their place.
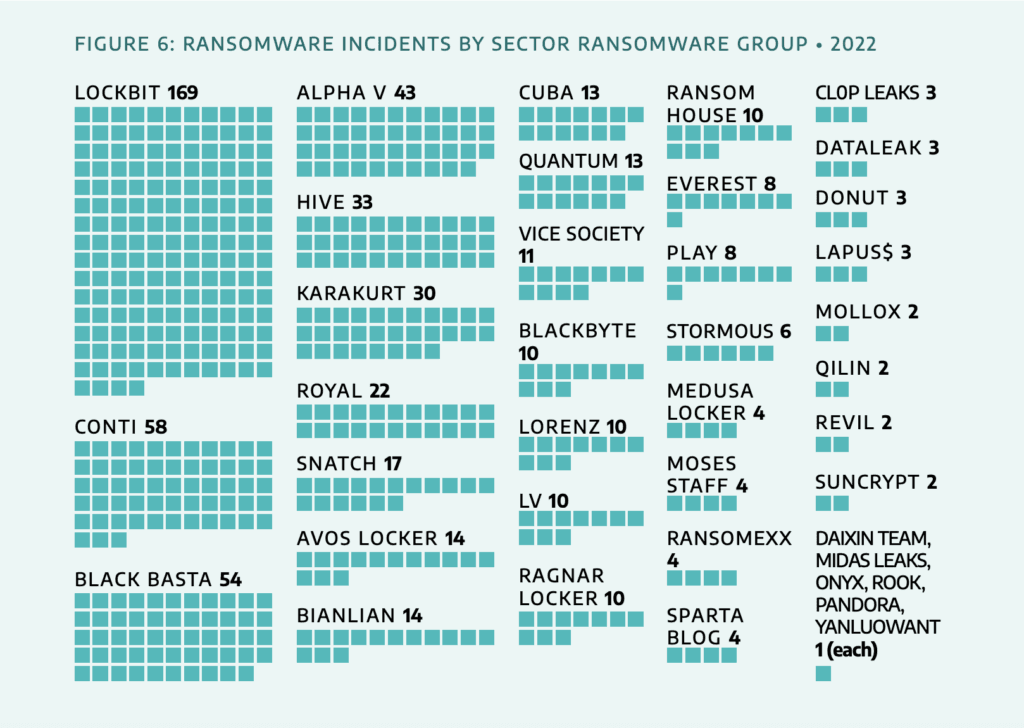
The notorious LockBit ransomware gang led the way last year with 169 ransomware attacks, followed by Conti – before they closed shop – Black Basta, Alpha V and Hive. Dragos found that of the 57 groups they track, 39 were active in 2022 – a 30 percent increase year over year.
“There were multiple reasons for the increase in ransomware activity impacting industrial organizations, including political tensions, the introduction of Lockbit Builder, and the continued growth of ransomware-as-a-service (RaaS)," researchers wrote. They also attributed the spike in part to political events, including the conflict in Ukraine and the diplomatic rift between Iran and Albania.
“Other indications of political partisanship (which may have impacted industrial organizations) include Conti’s declared alignment with the Russian Federation before it disbanded in May of 2022,” they wrote.
Conti targeted the automotive sector while multiple variants of LockBit were used to attack a range of industries including electric, manufacturing, construction, transportation, technology, consumer services, retail, and logistics.
Dragos found a handful of new ransomware groups that emerged in third quarter of last year, including SPARTA BLOG, BIANLIAN, Donuts, ONYX, and YANLUOWANG.
Part of why LockBit was so dominant is because it is the leading RaaS group, providing its software to operators launching the actual attacks in exchange for a portion of the ransoms.
Accounting for 28% of all attacks last year, LockBit offers operators exfiltration tools, anti-detection mechanisms and the ability to disable Windows Defender software.
The purported hacking of LockBit servers last year, involving the leak of the LockBit 3.0 builder, is likely to lead to further industrial attacks.
“Dragos assesses with moderate confidence that LockBit 3.0 will continue to target industrial organizations and will pose a threat to industrial operations into 2023, whether through the LockBit gang itself, or others creating their own version of LockBit ransomware," they wrote.
Poor segmentation and mistake-filled advisories
Alongside the evolution of several ransomware groups was a steep increase in the number of vulnerabilities and technical issues found by security companies like Dragos.
Lee said Dragos incident responders found poor network segmentation and several other problems that plagued many industrial companies.
Eighty percent of Dragos customers had limited visibility into their ICS environments while more than half had issues with network segmentation, undisclosed or uncontrolled external connections to their OT environment or lacked separate IT and OT user management.
Lee specifically highlighted one fact that bugged him about much of the reporting around ransomware attacks on industrial companies – the idea that IT and OT networks were separate. In many public statements about ransomware attacks, companies typically say a ransomware attack only affected their IT systems and not the OT or ICS systems.
According to Lee, for many organizations this difference is purely semantic, considering how intertwined many company systems are.
“There are many manufacturing environments we've been to where they said, ‘Oh it's the IT systems that are hit’ and then we look and it's engineer workstations and interfaces and things like that. Why would you call this IT? Just because it's a Windows operating system doesn't make it IT. It has specialized applications and a role in industrial operations. That makes it OT,” he said, adding there were cases Dragos was involved in where companies have incorrectly made these claims.
“So I would just push for people to question some of those companies a bit more, especially if you ever hear about operations coming down. That's generally not just because an IT network is down,” he added.
Dragos also noted a significant increase in the amount of mistakes made in advisories.
More than 30% of the advisories tracked by Dragos had mistakes of some sort within them, while less than half had mitigations – a surprising discovery given that ICS systems often cannot be patched without significant operational disruption, whereas a mitigation can be more targeted and less invasive.
Dragos also found that 83% of the vulnerabilities were buried deep within ICS networks and about half "could cause both a loss of view and a loss of control.”
“To patch in the OT world often requires system and plant shut-downs. ICS/OT relies on alternative mitigation to both reduce risk and maintain production," Dragos explained. The fact that more than three out of four vulnerabilities "lack that mitigation makes maintaining operations very challenging."
As for this year, Dragos said it is likely that ransomware will continue to disrupt industrial operations, both through mismanaged OT environments that allow ransomware to spread or through precautionary shutdowns of those environments to prevent ransomware from reaching those systems.
There has already been a major ransomware attack on an energy supplier this year, with Canada's Qulliq Energy Corporation dealing with a crippling incident in January that brought down its payment systems.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



