Double extortion is becoming ransomware's new normal
For a big chunk of the last year, the evolving ransomware landscape was perhaps the most dominant cybersecurity news story—until it wasn’t.
Although high-profile incidents like the SolarWinds breach and Microsoft Exchange Server vulnerabilities have been commanding the headlines in recent months, the ransomware threat continues to grow. And developments like double extortion scams—where ransomware actors both lock up a victim’s data and devices for a fee and post some of it online to pressure them into paying—are becoming “the new normal,” said Recorded Future ransomware specialist Allan Liska.
“For the first part of this year, ransomware hasn’t gotten a lot of attention, because there’s been so much other badness,” Liska said. “But ransomware hasn’t slowed down.”
According to an analysis of data collected by Recorded Future, the number of victims posted to ransomware extortion sites quadrupled from November to December last year, and has remained at high levels in 2021. What started as a novelty at the beginning of 2020 has grown into an everyday occurrence that ensnares dozens of companies every week.
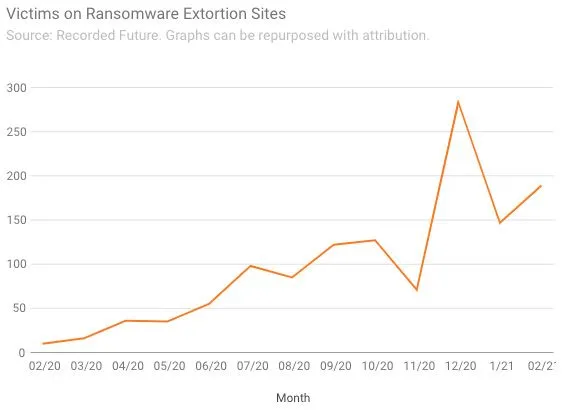
Some studies suggest that this double extortion trend has reached the point where it’s more common than not in ransomware attacks. A report by cybersecurity firm Coveware found that 70% of ransomware attacks in the fourth quarter of 2020 involved the threat to release stolen data, up from 50% in the third quarter.
The trend is pretty easy to explain—ransomware attacks by nature pressure victims into paying a demand, and adding a threat to release stolen data makes it more likely that some victims will pay. Organizations in heavily-regulated industries, such as finance and healthcare, might be especially wary of having sensitive customer data leaked online.
As a result, double extortion allows hackers to increase both the amount of ransoms they receive and the value of those demands. A report issued at the end of last year by the insurance firm Beazley found that ransom payments doubled year-on-year during the first six months of 2020. Coveware said the average ransom demand was $154,108 in the fourth quarter of 2020, down from a peak of $233,817 in the previous quarter.
Liska says he expects these trends to continue into 2021, but one development that could slow it down is the stance law enforcement takes. Although there have been relatively few ransomware-related arrests, law enforcement agencies in multiple countries have cracked down on several ransomware operations in recent months, and some groups seemed to slow down or cease activity.
“It may be the case where law enforcement becomes a deterrence. It wasn’t in 2020, but it appears to be more so now,” Liska said. “If law enforcement doesn’t continue the trend, the graph is going to continue to grow—there’s just too much money to be made in ransomware to not do it.”
Another possibility is that ransomware demands will rise so much that people will refuse to pay them altogether, “but it’s not going to be this year,” Liska said. He cautioned that the extortion site figures don’t capture the full picture: Part of the trend can be credited to better curation of extortion site data as security researchers became aware of certain pages. Additionally, the list doesn’t take into account victims of double extortion who decided to pay a ransom in exchange for not having their data leaked online.
— Bruce Liska contributed data collection and analysis on the number of victims posted to ransomware extortion sites.
Adam Janofsky
is the founding editor-in-chief of The Record from Recorded Future News. He previously was the cybersecurity and privacy reporter for Protocol, and prior to that covered cybersecurity, AI, and other emerging technology for The Wall Street Journal.



