DOJ shuts down ‘Warzone’ malware vendor and charges two in connection
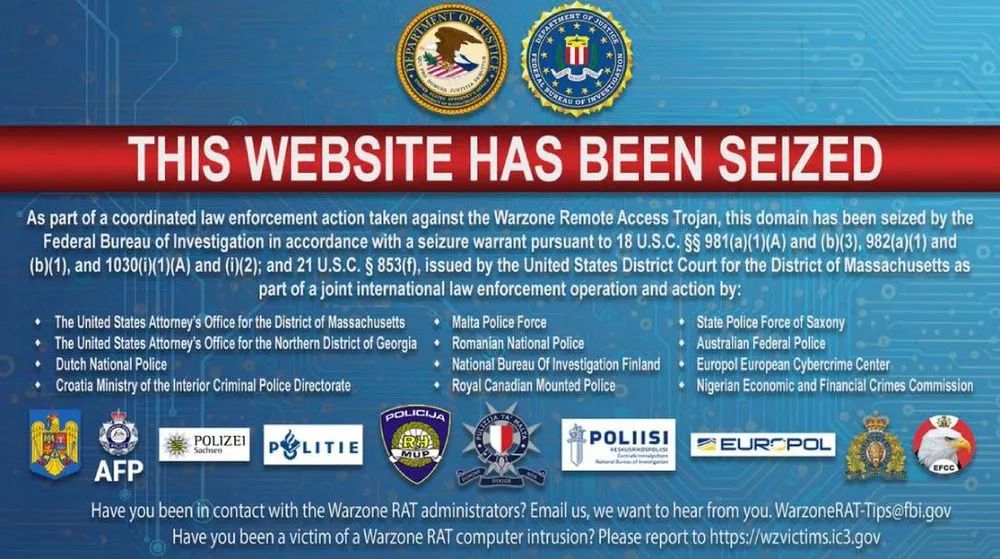
The U.S. Justice Department said it shut down a website and several other domains that sold the Warzone RAT malware — a tool cybercriminals used to access victims' devices, take screenshots, record keystrokes, steal data and watch victims through device cameras.
The DOJ also unsealed indictments charging people in Malta and Nigeria for their role in selling the malware and providing support to those who used it.
The website “warzone.ws” was seized alongside three other domains that sold the malware. Those charged include 27-year-ol Daniel Meli from Zabbar, Malta and 31-year-old Prince Onyeoziri Odinakachi from Nigeria.
Meli was arrested on Wednesday by the Malta Police Force and has already appeared before a judge. Meli was charged with four crimes and is accused of offering a variety of malware products and services for cybercriminals since 2012.
In addition to Warzone, Meli also sold the Pegasus malware — even providing technical support for customers. A Georgia court is seeking Meli’s extradition.
“Daniel Meli will no longer escape accountability for his actions selling malware,” said U.S. Attorney Ryan Buchanan for the Northern District of Georgia.
“This alleged cybercriminal facilitated the takeover and infection of computers worldwide. Our office was proud to partner with our federal and international counterparts to find Meli and bring him to justice.”
Odinakachi — who was indicted in a Massachusetts court on January 30 — was arrested on February 7 and has appeared before a court in Nigeria. He is accused of hacking several computers himself while also providing customer support for multiple people who purchased Warzone between June 2019 and March 2023.
Meli is facing up to 25 years in prison and a fine of at least $500,000 while Odinakachi is facing 15 years and a similar fine.
The operation to disrupt the infrastructure around Warzone was led by FBI agents in Boston and Atlanta as well as officials from Europol, Australia, the Netherlands, Croatia, Finland, Germany, Japan, Nigeria, Romania and Canada.
The FBI said that it covertly purchased the malware to analyze it and law enforcement agencies in several countries provided assistance in shutting down servers that hosted the Warzone infrastructure.
They urged potential victims of the malware to report any intrusions to the FBI.
“Those who sell malware and support cybercriminals using it should know that they cannot hide behind their keyboards or international borders,” said Acting U.S. Attorney Joshua Levy for the District of Massachusetts.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.