DocuSign scam targeted more than 10,000 inboxes: report
Scammers used a malicious DocuSign document in a campaign that tried to steal credentials belonging to more than 10,000 people across several organizations.
Researchers at cybersecurity company Armorblox said the brand impersonation campaign targeted Microsoft Office 365 email accounts and managed to bypass other security tools.
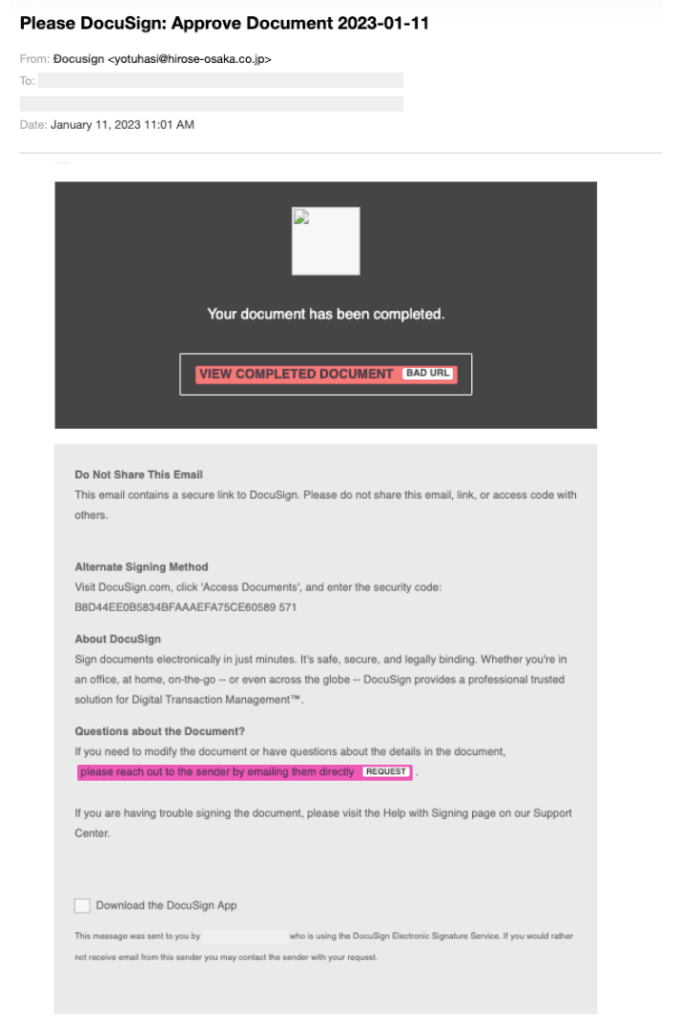
The subject of the emails was “Please DocuSign: Approve Document 2023-01-11” in an attempt to make victims think the email was urgent and needed to be opened as soon as possible.
While the email address and domain name had no association with DocuSign, the scammers were relying on the fact that it can be hard to see these names – particularly on mobile devices where many people typically read their emails.
The researchers noted that DocuSign attacks are particularly successful for scammers because people are used to getting these kinds of emails before and after signing documents through the platform.
“The language used within the body of the email continues to impersonate the well-known brand DocuSign,” the researchers said.
“Through the inclusion of statements around alternate shipping methods, a blurb about the company DocuSign, and even a disclaimer to not share this email with anybody else, unsuspecting victims who fell for the attackers’ manipulating tactics and opened the email would have been presented with additional language and information aimed to establish trust in the victims and encourage he or she to click on the main link that reads: VIEW COMPLETED DOCUMENT.”
The goal of the email was to get users to click on the button, which would take them to a fake landing page that impersonated cybersecurity firm Proofpoint. The page had Proofpoint branding and a PDF icon urging the person to clock on the document in order to view it.
The landing page had several hallmarks of legitimacy, including a fake checkmark resembling verification from cybersecurity company Symantec and even the inclusion of the person’s email address. The goal was to get people to enter their credentials for Proofpoint.

Armorblox did not say if any of the emails were successful, but the campaign builds on a longstanding trend of hackers using platforms like DocuSign to manipulate people into handing over valuable credentials.
A report from cybersecurity firm Check Point last week found that DocuSign was one of the most used brands in phishing attacks in Q4 alongside Microsoft, Zoom, LinkedIn and Amazon.
“There's a good chance that most recipients have had professional or personal interaction with those services. Although PDF and HTML attachments were very common, the top phishing vector was still a rogue URL link in an email,” said KnowBe4’s Roger Grimes.
“Users need to always hover over any links embedded in any email and examine it for legitimacy before clicking on it. Fake HR, human resource, requests were also a top clicked simulated phishing topic, accounting for nearly a third of all clicked phishing tests.”
Researchers also revealed another email campaign last week that starts with what appears to be a document from DocuSign. The hackers used the email to hide a malicious URL inside an empty image, allowing them to bypass traditional scanning services.
Proofpoint uncovered a DocuSign-branded email campaign that sought to spread a new malware loader called Bumblebee used by multiple crimeware threat actors. That campaign similarly involved a "REVIEW THE DOCUMENT" hyperlink in the body of the email.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



