DirtyMoe malware has infected more than 100,000 Windows systems
A Windows malware botnet believed to be operated out of China has exploded this year, growing from 10,000 infected systems in 2020 to more than 100,000 in the first half of 2021, cyber-security firm Avast reported last week.
Known under different names, such as DirtyMoe, PurpleFox, Perkiler, and NuggetPhantom, the malware has been around since late 2017.
Its primary purpose has been (and still is) to infect Windows systems and secretly mine cryptocurrency behind the user's back, although a feature to launch DDoS attacks was also spotted back in 2018.
For most of its lifetime, the botnet was a small-time operation.
Its creators primarily relied on email spam to lure users to malicious sites hosting an exploit kit named PurpleFox [1, 2, 3, 4].
This web-based attack tool abused browser vulnerabilities, usually in Internet Explorer, to install a rootkit component on unpatched Windows systems that granted the malware full control over the infected host, which it used for crypto-mining.
Dropping #NuggetPhantomhttps://t.co/SvYdq1WW1T
— nao_sec (@nao_sec) April 4, 2021
This rootkit, known under different names such as DirtyMoe, PurpleFox, Perkiler, and NuggetPhantom, was known to the cyber-security industry but was only seen as an interesting marginal threat.
According to numbers shared by Avast, the DirtyMoe botnet usually averaged between a few hundred to a few thousand infected systems on a yearly basis for most of its life from 2017 to 2020.
Things radically changed towards the end of 2021 when the DirtyMoe gang pushed an update to its operation and added a worm module that could allow the malware to spread via the internet to other Windows systems.
This module scanned the internet and performed password brute-force attacks against remote Windows computers that had left their SMB port open online.
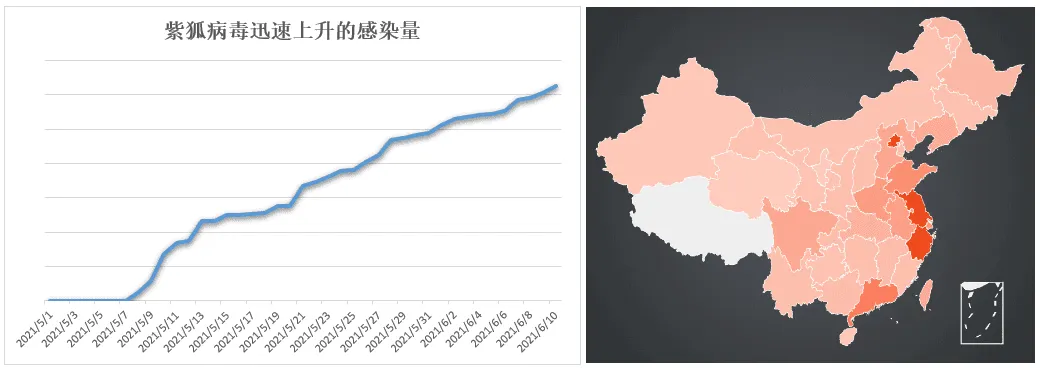
The SMB spreading module allowed the malware to explode in terms of infections, in what Avast described as a logarithmic scale, reaching more than 100,000 systems infected this year alone.
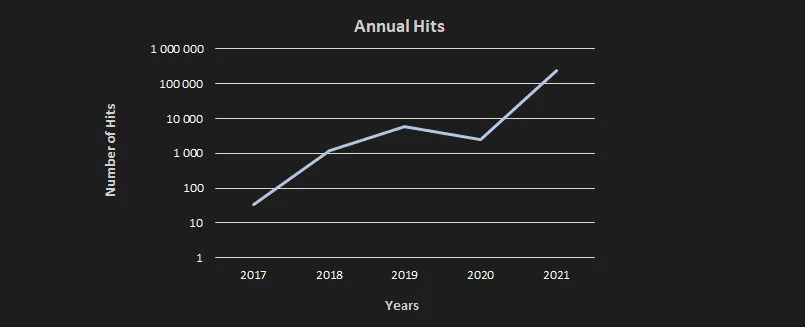
However, this number is only based on Avast's visibility—namely, computers where its antivirus is installed. The true size of the DirtyMoe botnet is believed to be much much higher.
Evidence to this stands a report from Chinese security firm Tencent, which, at the start of the month, noted a spike in DirtyMoe/PurpleFox infections in China over the course of 2021, echoing the similar explosion in infection numbers reported by Avast in Europe, Asia, and the Americas.
With this threat continuing to expand, Avast has compiled a report on the malware's evolution and operations, along with indicators of compromise (IOCs) that defenders could use to scan their networks for DirtyMoe/PurpleFox infections.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.