Deadbolt ransomware hits more than 3,600 QNAP NAS devices
More than 3,600 network-attached storage (NAS) devices from Taiwanese company QNAP have been infected and had their data encrypted by a new strain of ransomware named Deadbolt.
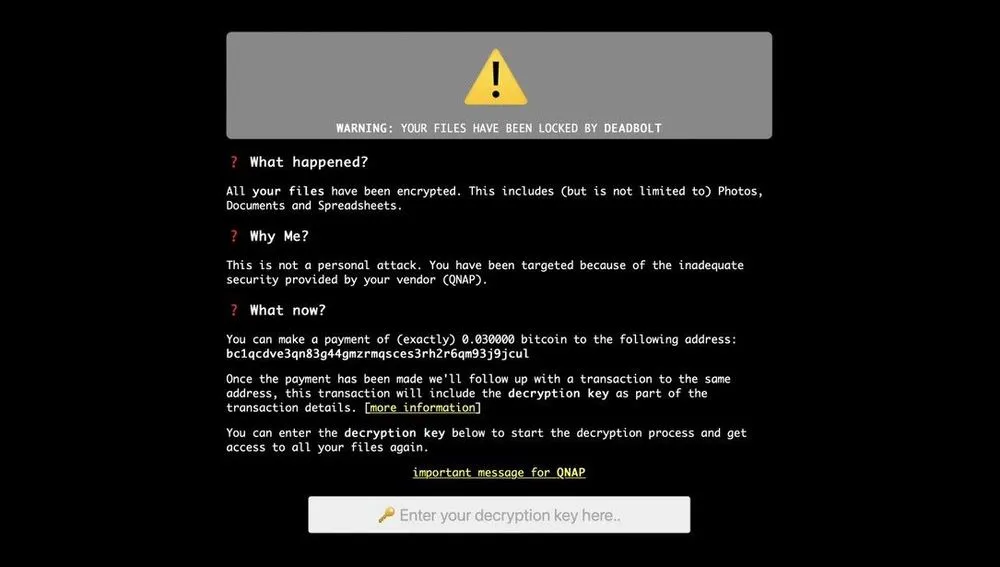
Devices attacked by the Deadbolt gang are easy to recognize because the login screen is typically replaced with a ransom note, and local files are encrypted and renamed with a .deadbolt extension.
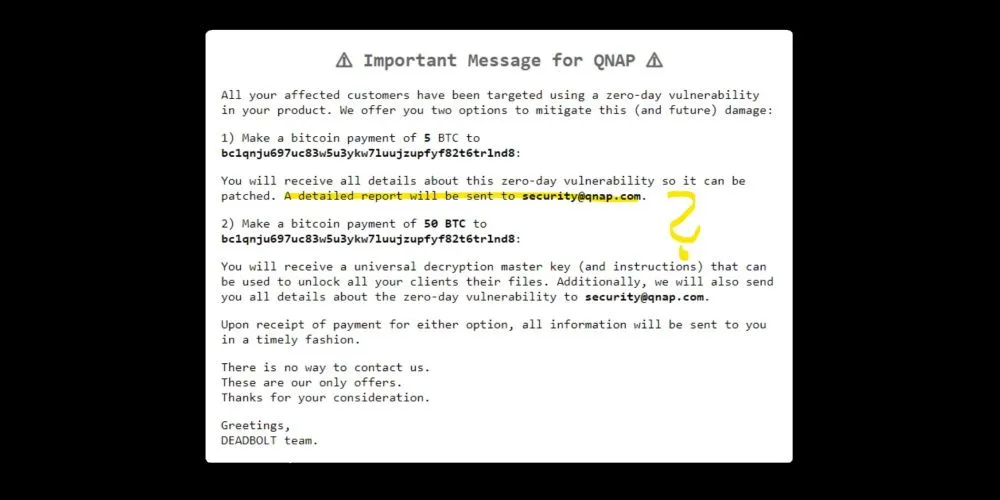
The threat actor behind the attacks is extorting not only the owners of the NAS devices but also the QNAP company itself.
According to a copy of the ransom note, device owners are told to pay 0.03 Bitcoin ($1,100) to receive a decryption key to unlock their files, while in an second note, the hackers demand 5 Bitcoin ($1.86 million) from QNAP to reveal details about the supposed zero-day vulnerability they have been using to attack its users, and another 50 Bitcoin ($18.6 million) to release a master decryption key that unlock all of the victims' files.
According to a Censys query for the name of the Deadbolt ransom note file name, at least 3,600 QNAP NAS devices have been hit so far by the attackers.
According to Félix Aimé, a security researcher for French security firm Sekoia, the vast majority of impacted devices are located in Europe and the US.
For its part, QNAP was quick to formally acknowledge the attacks in a blog post on Wednesday, hours after hundreds of users started flocking to its support forum to report finding their files encrypted.
In the first days following the attack, the company has been telling users to disconnect devices from the internet and, if not possible, at least disable features such as port forwarding and UPnP on their routers, to prevent attackers from connecting to the NAS systems.
QNAP pushes out a silent firmware update
While it is unclear if QNAP has been in contact with the attackers or if it had paid any ransom demand, the company has silently force-installed several firmware updates for some of its customers earlier today, according to one of its support agents' comments on Reddit; however, it is unclear if these updates will block Deadbolt attacks.
"I know there are arguments both ways as to whether or not we should do this. It is a hard decision to make. But it is because of Deadbolt and our desire to stop this attack as soon as possible that we did this," the QNAP support agent said today.
In the meantime, Deadbolt attacks are still continuing to take place, according to new reports made on the QNAP forums just hours before this article's publication.
Prior to these attacks, QNAP NAS devices have also been targeted with other ransomware strains, such as Qlocker and ech0raix.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.