UK National Crime Agency reveals it ran fake DDoS-for-hire sites to collect users’ data
Britain’s National Crime Agency (NCA) revealed on Friday that it had set up a number of fake DDoS-for-hire sites to infiltrate the online criminal underground.
It said that users who registered for the sites were not given access to cybercrime tools but instead had their data collated by investigators.
DDoS (distributed denial-of-service) attacks are among the least sophisticated forms of criminal cyber mischief. The attacks — which overwhelm network resources with traffic to effectively take them offline — are incapable of stealing or modifying data on the victim server.
DDoS attacks have been launched by state-affiliated hackers, but for-hire services typically attract a different clientele, including gamers who use so-called “booters” to kick rivals from an online game — a criminal offense which the agency has run advertising campaigns to raise awareness of.
“Users based in the UK will be contacted by the National Crime Agency or police and warned about engaging in cyber crime. Information relating to those based overseas is being passed to international law enforcement,” the NCA said.
The operation is not one of the more sophisticated busts that British cyber cops have been involved in, but provides police with a mechanism to intervene in the cases of potential offenders when they are engaged in what the NCA described as “an attractive entry-level crime.”
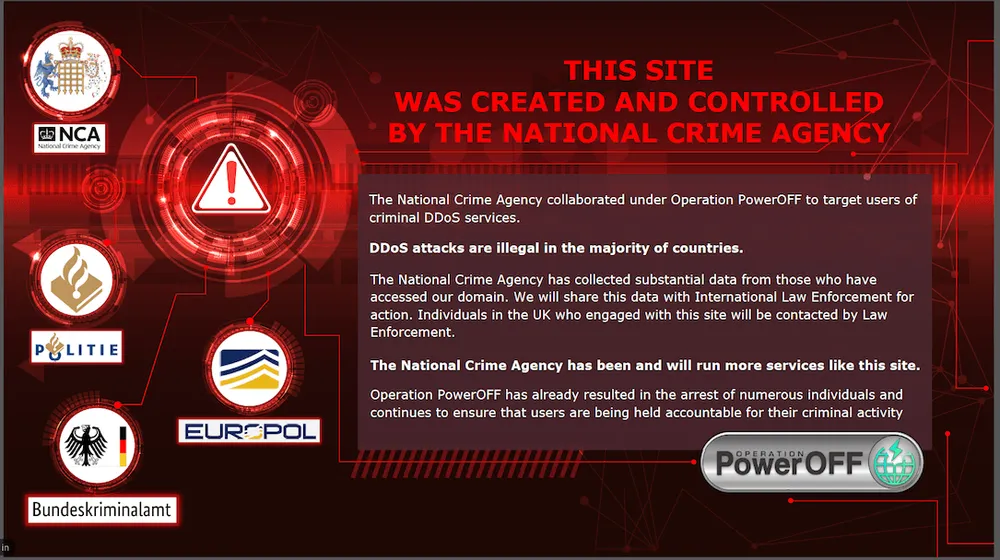
According to the NCA the fake sites have so far been accessed by around several thousand people. One of them was replaced Friday with a splash page warning that the NCA, alongside the Dutch Politie and the German Bundeskriminalamt, had created and controlled the site.
“Operation PowerOFF has already resulted in the arrest of numerous individuals and continues to ensure that users are being held accountable for their criminal activity,” the splash page states.
Alan Merrett, from the agency’s National Cyber Crime Unit, stated: “We will not reveal how many sites we have, or for how long they have been running. Going forward, people who wish to use these services can’t be sure who is actually behind them, so why take the risk?”
Friday’s announcement follows the NCA helping to take down 48 of the world’s most popular booster sites last December and arresting an 18-year-old man in Devon on suspicion of administering one of the sites.
At the time the U.S. Department of Justice said six defendants in the U.S. had been charged with overseeing the services, which included Booter.sx., Astrostress.com, and SecurityTeam.io.
“Traditional site takedowns and arrests are key components of law enforcement’s response to this threat. However, we have extended our operational capability with this activity, at the same time as undermining trust in the criminal market,” added Merrett.
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79