DDoS botnets, cryptominers target Azure systems after OMIGOD exploit goes public
Threat actors are attacking Azure Linux-based servers using a recently disclosed security flaw named OMIGOD in order to hijack vulnerable systems into DDoS or crypto-mining botnets.
The attacks, which began on Thursday night, September 16, are fueled by a public proof-of-concept exploit that was published on the same day on code hosting website GitHub.
The attacks started slow, according to Andrew Morris, founder and CEO of threat intelligence company GreyNoise.
Roughly 10 malicious servers were scanning the internet for vulnerable servers Thursday night, but the number had grown to more than 100 by the next morning.
Attacks target Azure Linux systems vulnerable to OMIGOD
The attackers are looking for Linux servers running on Microsoft's Azure cloud infrastructure. These systems are vulnerable to a security flaw called OMIGOD.
Discovered over the summer by cloud security firm Wiz, the vulnerability resides in an app called Open Management Infrastructure (OMI), which Microsoft has been silently installing by default on most Azure Linux virtual machines.
The app, which works as a Linux alternative to Microsoft's Windows Management Infrastructure (WMI), a service that collects data from local environments and synchronizes it with a central management server, is vulnerable to an issue tracked as CVE-2021-38647.
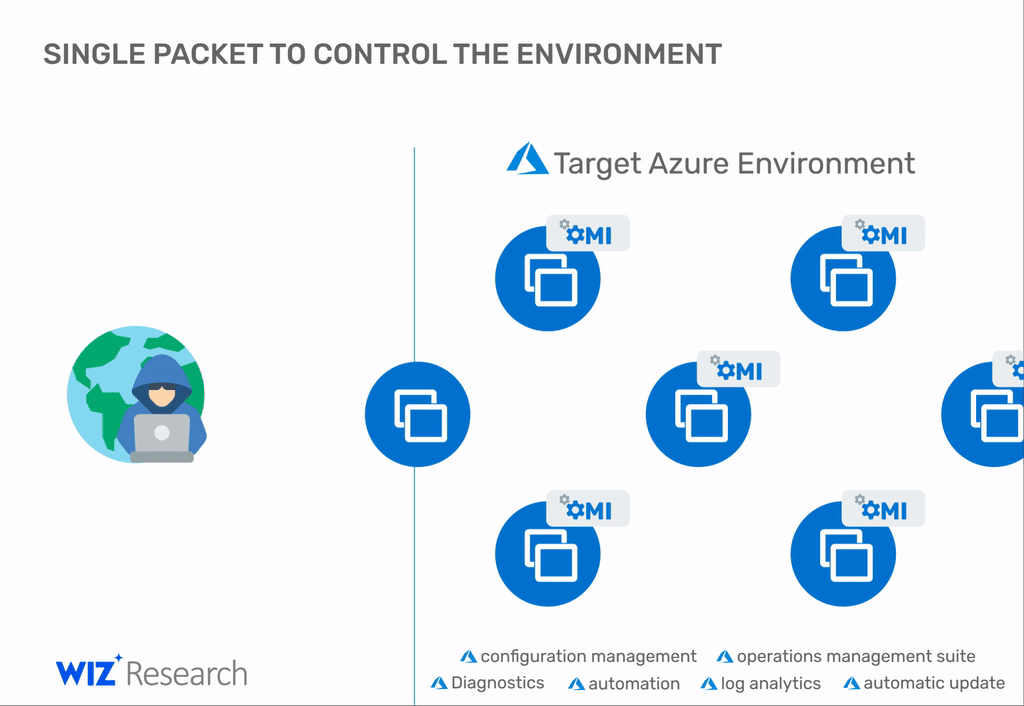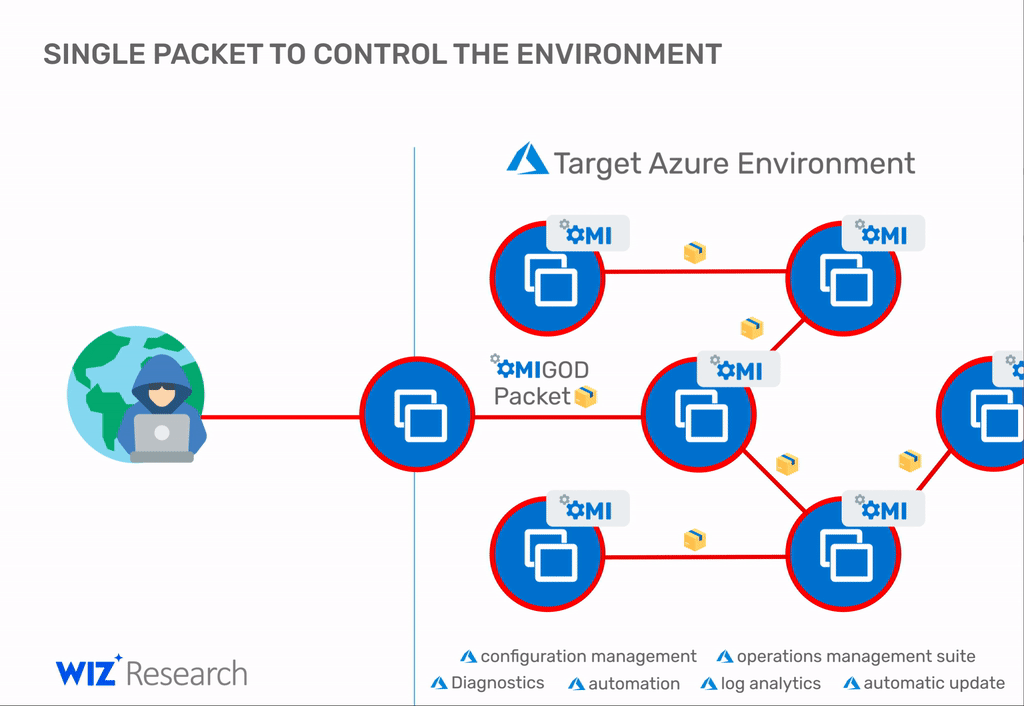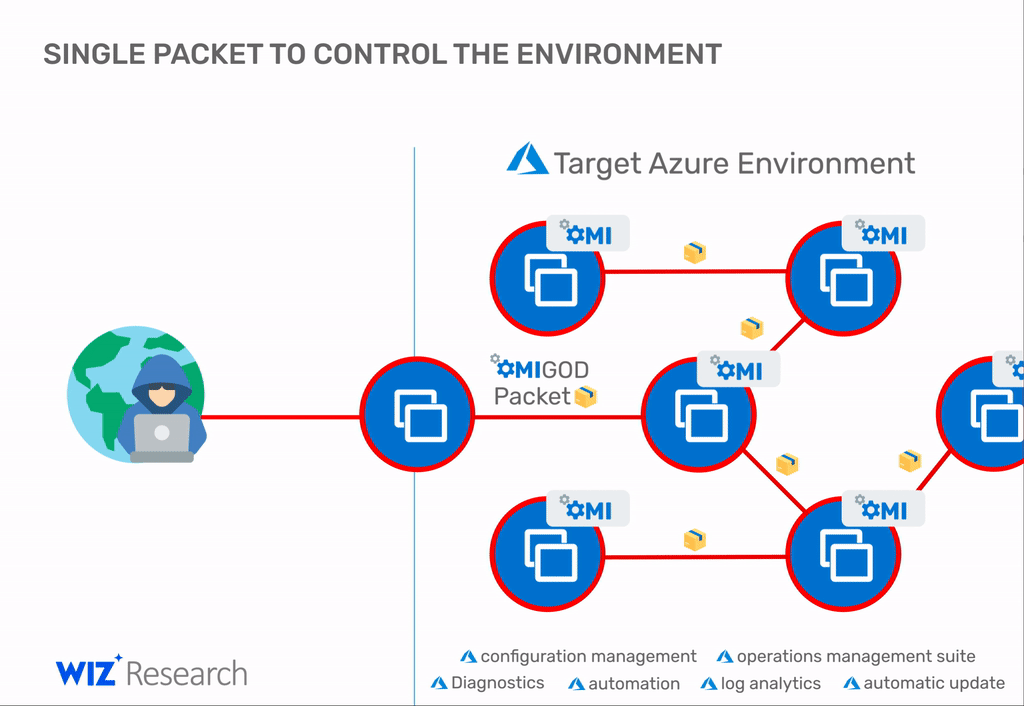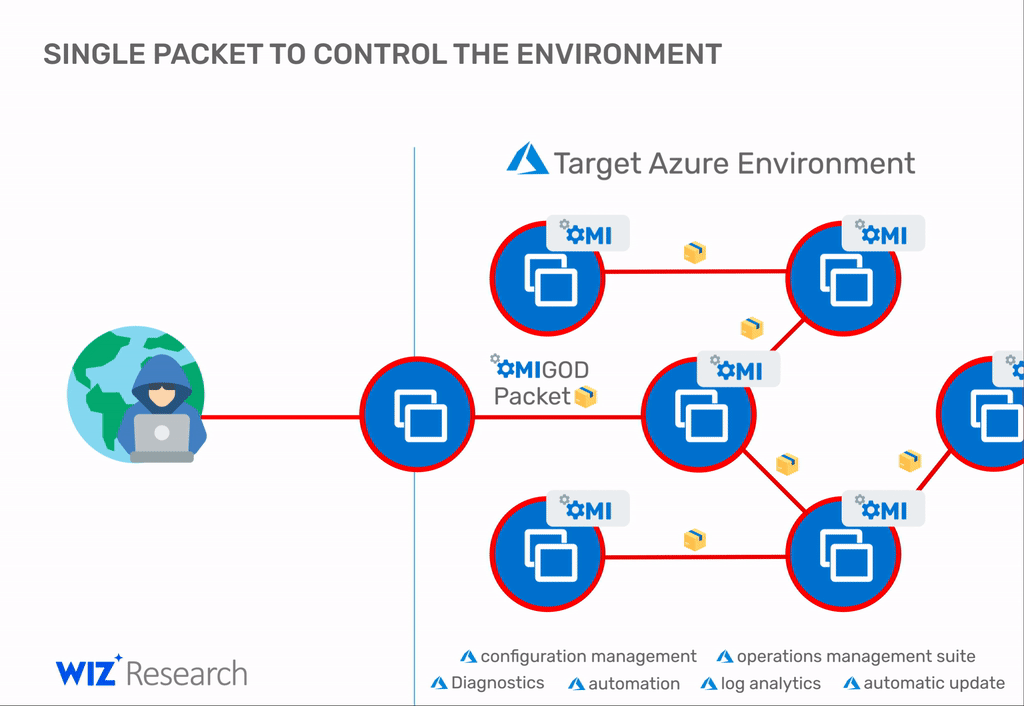
This bug allows threat actors to take over Azure Linux servers by sending a malformed packet to the OMI client.
"This is a textbook RCE vulnerability that you would expect to see in the 90's – it's highly unusual to have one crop up in 2021 that can expose millions of endpoints," said Wiz security researcher Nir Ohfeld, who discovered the issue.
"With a single packet, an attacker can become root on a remote machine by simply removing the authentication header."
"It's that simple," the researcher said in a report published on Tuesday.
Microsoft's boo-boo
Microsoft addressed the bug by releasing version 1.6.8.1 for the OMI client on GitHub.
However, Microsoft did not automatically install this update for OMI clients deployed across its infrastructure, effectively leaving tens of thousands of Azure Linux servers open to attacks.
Furthermore, the company took another three days to replace the OMI client version inside its Azure Linux VM images. This means that companies that rushed to re-image their servers deployed new VMs that were still vulnerable to attacks.
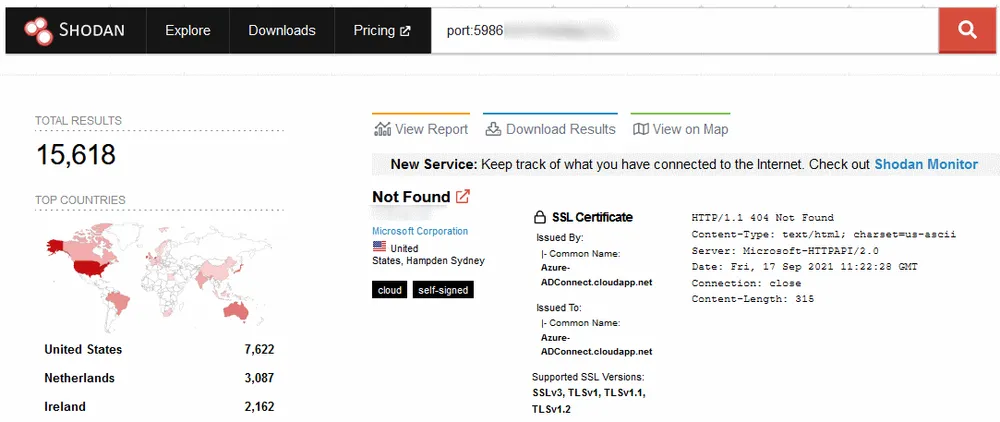
While many of these servers are inside corporate networks and behind firewalls, there are still plenty more that are connected online. A Shodan query currently surfaces more than 15,600 Azure Linux internet-connected servers.
Exploitation was expected
Attacks exploiting this vulnerability have been expected ever since Wiz published its report on Tuesday.
"I think that the most interesting thing here is that the RCE is really easy to exploit," Alon Schindel, threat research lead for Wiz, told The Record in a conversation earlier this week. "We've already seen some people on Twitter that were able to do so."
But the attacks took off hours after a security firm published a proof-of-concept exploit on GitHub. This same exploit was spotted in attacks by security firm Bad Packets earlier today.
Mass scanning activity detected from 45.146.164.110 checking for Azure Linux OMI endpoints vulnerable to remote code execution (CVE-2021-38647).
— Bad Packets by Okta (@bad_packets) September 17, 2021
Vendor advisory: https://t.co/PO4A8mK5PI
Proof of concept: https://t.co/ioxDgZ9AlM#threatintel pic.twitter.com/TKHFVTOmpb
According to reports from security researchers such as Kevin Beaumont and German Fernandez, after attackers use the OMIGOD exploit, they immediately deploy malware that ensnares the hacked server into cryptomining or DDoS botnets.
But Schindel told The Record today that these attacks are only superficial and that threat actors could easily pivot to many other internal servers are the OMI client is installed.
"You're basically getting new targets for free. After you successfully exploited a machine, you can try to move laterally with OMIGOD or with other techniques and assess the value of your target," Schindel said.
"Alternatively, if you already had access to a network, OMIGOD can be used for lateral movement inside a network but we can't scan such internal exploitation attempts."
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.