DDoS Attacks Decline, but Big Incidents Still Resonate
Are the days of DDoS attacks over?
Reports last week that the New Zealand Stock Exchange suffered a multi-day disruption due to a DDoS incident brought renewed attention to that attack method. However, several indicators suggest that DDoS attacks, or distributed denial-of-service attacks, aren’t as big a problem as they used to be.
References to DDoS attacks at the beginning of 2020 were almost half of what they were during the same period in 2018, according to data collected by Recorded Future from sources including news reports and hacker forums. Additionally, a June study from NBIP, a Netherlands-based digital infrastructure non-profit, found that the number of DDoS attacks registered by the organization decreased by about 2% in 2019 compared to the previous year, despite the number of participants in the organization growing by 10%.
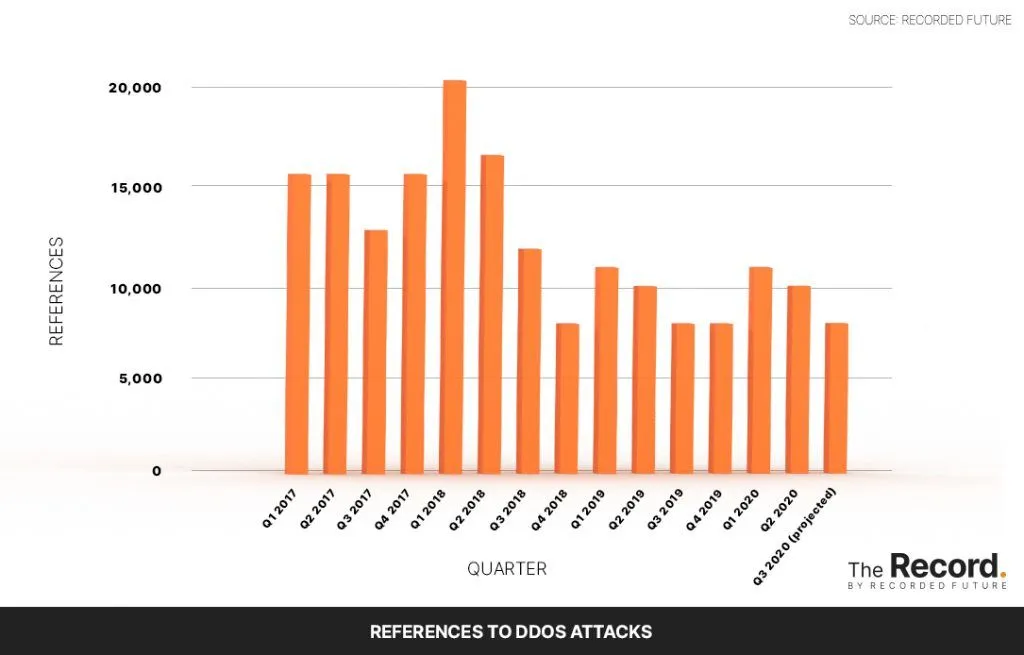
“It is certain that the substantial growth that was visible from 2017 to 2018 has not continued in 2019,” according to the report.
DDoS attacks work by flooding a targeted server with junk traffic, making it inaccessible to legitimate users. In recent years, DDoS operators have leveraged botnets in their attacks, stringing together large amounts of infected computers and devices to overwhelm victims.
References to DDoS attacks peaked in late 2016 when domain name system (DNS) provider Dyn was targeted by such an attack, according to Recorded Future data. In that incident, a botnet composed of internet-connected devices infected with Mirai malware was used to overwhelm Dyn and disrupt a wide range of internet services, such as Netflix and Reddit.
One reason DDoS attacks have been declining since then is that organizations have gotten better at resisting them. A variety of platforms offer DDoS mitigation services, which generally work by detecting and blocking malicious traffic based on indicators like a device’s IP address. These services can also temporarily increase a victim’s bandwidth, allowing them to handle the increase in traffic until malicious devices are blocked.
Although DDoS attacks have dropped in recent years, they could still reemerge as attackers develop new techniques. Last June, for example, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency warned of DNS amplification attacks, which use misconfigured DNS servers to overwhelm victims with junk traffic. In 2018, developer platform GitHub was targeted with an amplification attack that reached 1.35 terabits per second of traffic, according to Wired, making it the biggest DDoS attack on record.
Adam Janofsky
is the founding editor-in-chief of The Record from Recorded Future News. He previously was the cybersecurity and privacy reporter for Protocol, and prior to that covered cybersecurity, AI, and other emerging technology for The Wall Street Journal.

