Days before a report, Chinese hackers removed malware from infected networks
Last month, security firm FireEye detected a Chinese hacking campaign that exploited a zero-day vulnerability in Pulse Secure VPN appliances to breach defense contractors and government organizations in the US and across Europe.
The hacking campaign allowed the threat actors — two groups which FireEye tracks as UNC2630 and UNC2717 — to install web shells on Pulse Secure devices, which the attackers used to pivot to internal networks from where they stole internal network credentials, email communications, and sensitive documents.
But in a follow-up report published today, FireEye said it found something strange — namely that at least one of the groups involved in the attacks began removing its malware from infected networks three days before its researchers exposed the attacks.
"Between April 17th and 20th, 2021, Mandiant incident responders observed UNC2630 access dozens of compromised devices and remove webshells like ATRIUM and SLIGHTPULSE," researchers said on Thursday.
The threat actor's actions are highly suspicious and raise questions if they knew of FireEye's probing.
The timing could have been a coincidence, but UNC2630 could have very well learned that FireEye was investigating some of the hacked networks and the hackers consciously decided to pull back and remove evidence of the hackers to protect the rest of their operations.
In an email, FireEye researchers dodged questions and declined to elaborate on the topic.
Four new malware strains discovered
But the FireEye follow-up report also surfaced new details about the hacking campaign that the company initially detailed last month.
First and foremost, FireEye said it discovered four additional malware strains, on top of the 12 it already detailed in its initial report.
Malware Family
Description
Actor
BLOODMINE
BLOODMINE is a utility for parsing Pulse Secure Connect log files. It extracts information related to logins, Message IDs and Web Requests and copies the relevant data to another file.
UNC2630
BLOODBANK
BLOODBANK is a credential theft utility that parses two files containing password hashes or plaintext passwords and expects an output file to be given at the command prompt.
UNC2630
CLEANPULSE
CLEANPULSE is a memory patching utility that may be used to prevent certain log events from occurring. It was found in close proximity to an ATRIUM webshell.
UNC2630
RAPIDPULSE
RAPIDPULSE is a webshell capable of arbitrary file read. As is common with other webshells, RAPIDPULSE exists as a modification to a legitimate Pulse Secure file. RAPIDPULSE can serve as an encrypted file downloader for the attacker.
UNC2630
Second, the company said it worked with Pulse Secure to identify the hacked appliances and their owners. This allowed the security firm to learn more about the targets.
Based on the new data, FireEye said that most of the victims were organizations based in the US, with the rest being in Europe.
Furthermore, while initially the company said the attacks targeted defense contractors and government organizations, the new data showed that attackers also went after companies in other industry verticals, such as telecommunications, finances, and transportation.
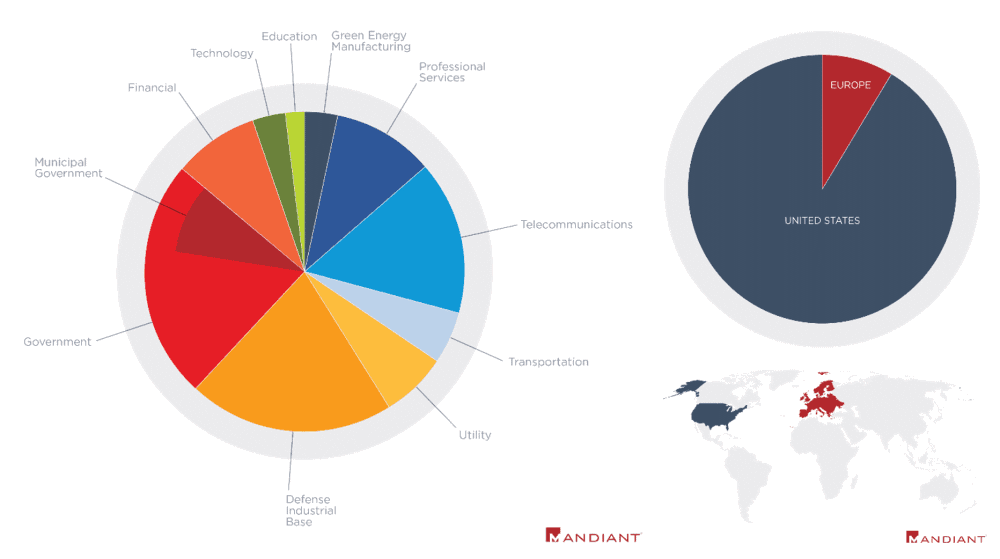
Image: FireEye
Additionally, FireEye said that while initially it believed that UNC2630 might have a nexus to the Chinese state, the company has now revived its attribution and has linked both groups to the Chinese government's cyber-espionage efforts.
"We now assess that espionage activity by UNC2630 and UNC2717 supports key Chinese government priorities," the company said.
"Many compromised organizations operate in verticals and industries aligned with Beijing's strategic objectives outlined in China's recent 14th Five Year Plan."
FireEye said that based on a joint analysis together with fellow security firm BAE Systems, the hacking campaign had the hallmarks of a classic cyber-espionage operation, with FireEye noting that the two groups spent a great deal of time editing or removing forensic evidence from hacked networks in order to hide their intrusions and that the groups also did not appear to engage in intellectual property theft.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



