‘Dark Pink’ APT attacks governments, militaries, more in Thailand, Brunei, Belgium, Vietnam and Indonesia
The Dark Pink hacker group has been tied to five new attacks on governments, militaries and organizations based in Belgium, Thailand, Brunei, Vietnam and Indonesia.
Researchers from Group-IB have been tracking the group for months and said it has been active since mid-2021, compromising at least 13 organizations across Europe and the Asia-Pacific region.
The advanced persistent threat (APT) group, which appears to focus on exfiltrating data, has not been tied to any country or previously known hacking group.
The most recent attacks took place in January and April and involved government ministries in Brunei and Indonesia, but the researchers also discovered older attacks on an educational organization in Belgium dating back to February 2022.
In addition to the Belgium attack and the two most recent incidents, Group-IB uncovered two others involving a military body in Thailand in October 2022 and a nonprofit in Vietnam in late December 2022.
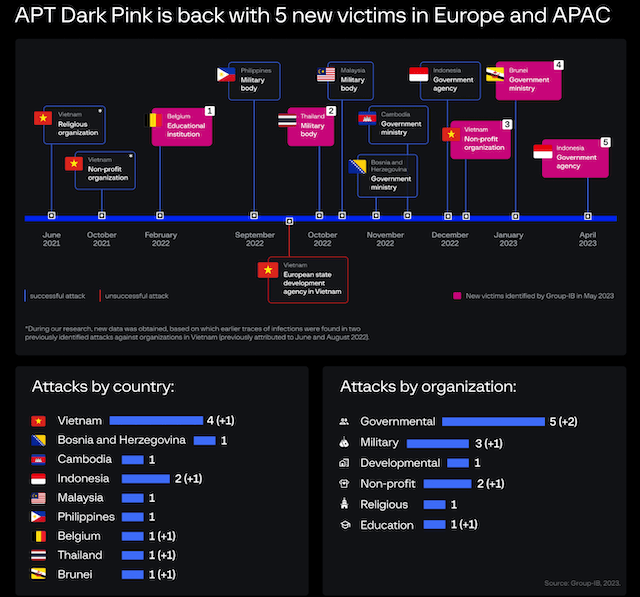
“Although most attacks occurred in the Asia-Pacific region, two organizations based in Europe were also on the victim list, which means that the threat actor’s geography could be broader than initially thought,” the researchers said.
“The fact that two attacks were executed in 2023 indicates that Dark Pink remains active and poses an ongoing risk to organizations. Evidence shows that the cybercriminals behind these attacks keep updating their existing tools in order to remain undetected.”
In reports from earlier this year, Group-IB and other security companies identified attacks on “high-profile targets” in Cambodia, Indonesia, Malaysia, Philippines, Vietnam and Bosnia and Herzegovina.
Clues on GitHub
Eight of the 13 attacks in the latest report targeted governments or militaries and typically involved spoofed documents related to trade issues as a lure. The APT group has sought to exfiltrate data and gain wider access to government networks during its attacks.
The group deploys a wide array of customized tools to maintain access to systems and stay undetected while stealing victim data.
Group-IB gained access to an account on the code-hosting platform GitHub used by the group and analyzed its tools and tactics, discovering how the hackers exfiltrate data and evade detection on infected machines.
As an example, Group-IB analyzed a malicious file named “[Update] Counterdraft on the MoU on Rice Trade.zip.iso” that was used to infect a victim. The file includes a “.docx” extension to trick victims into thinking it is safe to open. From there, tools are downloaded onto a victim device allowing for it to be controlled remotely and for sensitive data to be stolen.
The researchers noted that they only found one GitHub account used during all the attacks, which “suggests that Dark Pink may have remained undetected for a long time.”
“Malware initialized by the threat actors can issue commands for an infected machine to download modules from the GitHub account. While analyzing this threat, we discovered a new Dark Pink account on GitHub (hXXps://github[.]com/peterlyly),” they said.
“The first commit is dated Jan. 9th, 2023. This is the day when the first notion about this group was available in the public domain.”
The GitHub account held several tools used during attacks including custom malware and more.
Group-IB said Dark Pink used a variety of methods and tools to steal data, explaining that information from data stealers was typically sent to a chat on Telegram in a zip archive. They have previously seen the group send exfiltrated data through email or cloud services like Dropbox.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.