Cybercrime groups find a new target: religious institutions
Two well-established hacking groups claimed attacks on religious organizations over the weekend, a foray into a new arena for gangs that typically focus their attention on corporations and government agencies.
The notorious LockBit ransomware group added South Carolina-based Relentless Church to its list of victims on Saturday, claiming to have stolen employee data ranging from passports to financial documents. The evangelical megachurch, which has more than 15,000 members and attracts over 100,000 viewers online during streamed services, did not respond to requests for comment.
The next day, data extortion group Karakurt claimed it attacked Our Sunday Visitor, a Catholic publishing company that produces newsletters, religious books, pamphlets and more. The organization started in 1912 and has expanded from its start as a parish news bulletin into the publisher of a wide variety of content for Catholics.
Karakurt hackers claimed to have stolen 130 gigabytes of data, including accounting documents, HR information, employee data, financial contracts, invoices, marketing information and more.
Jim Weigert, Our Sunday Visitor’s chief marketing officer, confirmed that the company recently “discovered suspicious activity” within their network.
“Upon discovering this, we immediately took steps to secure our systems and launch a comprehensive investigation,” he said, adding that third-party experts were called and law enforcement was notified. “Our servers remained fully operational throughout this process,” he said.
Weigert declined to answer any questions about whether a ransom was issued, saying only that the organization is “committed to protecting the data trusted in our care” and will “continue to update our protocols to always remain in line with industry best practices for data security.”
Several experts said it was unusual for hackers to go after religious institutions, noting cases where groups have banned affiliates for targeting organizations considered to be off limits.
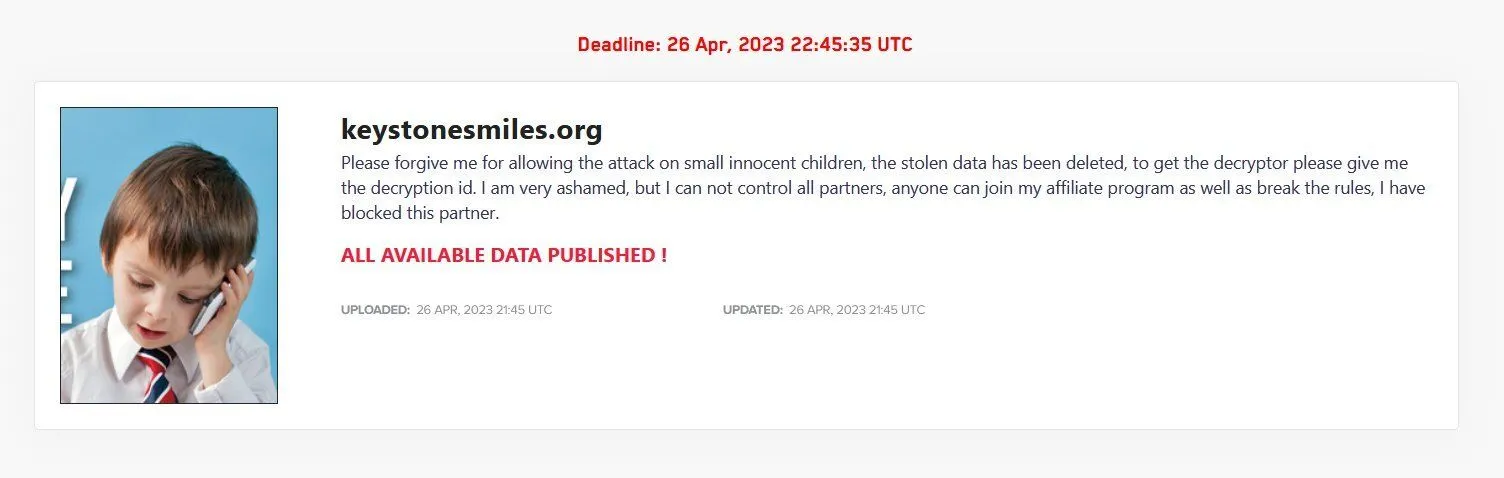
These rules are often ignored or applied arbitrarily — particularly when it comes to attacks on hospitals. Just last week, however, the LockBit ransomware group banned an affiliate for attacking Keystone SMILES Community Learning Center, a nonprofit preschool organization.
The group apologized for the attack on its leak site and claimed to have deleted the data that was stolen. A free decryptor was offered to the organization but they did not respond to requests for comment about whether it was used.
Emsisoft ransomware expert Brett Callow said he does not think most ransomware groups or hackers have explicit rules against attacking religious organizations but noted that “even if they did, their rules are only for PR purposes and routinely ignored.”
“LockBit recently tried to squeeze a paltry $10,000 from a hospital in a low income country but, in cases when it becomes obvious they’ll not be paid, will hand over a decryptor for free so they appear to be good guys — or, at least, not terrible guys who put lives at risk by knowingly attacking hospitals,” he said.
“That’d make it hard for companies to pay them. It’s not a good look to be seen to be funding almost-terrorists.”
Recorded Future ransomware expert Allan Liska said most groups do not go after organizations like churches for financial reasons, not moral ones.
“There isn’t much money in going after an individual church, unless maybe it is a megachurch,” he said.
But Liska did note that in the past, one group did go after churches: Pysa, which is known for attacking the Salvation Army in 2021.
“Between February and November of 2021 Pysa listed 5 churches on their extortion site. Of course, there might have been more but they were just never made public,” Liska explained. “I don’t think I’ve seen a run like that on churches since then.”
Karakurt ties to Conti
Karakurt has made a name for itself as an extortion group, eschewing the need for ransomware and relying solely on the theft of data. In August 2022, the group attacked the International Centre for Migration Policy Development — an NGO that runs migration services and research in more than 90 countries.
The FBI, Cybersecurity and Infrastructure Security Agency (CISA) and the Treasury Department warned last year that the group was extorting victims for ransoms of $25,000 to $13 million in bitcoin.
Several security companies — including Infinitum IT and Advanced Intelligence — have released reports showing concrete ties between the infrastructure used by Karakurt and the now defunct ransomware gang Conti.
Following the release of troves of documents and chats related to Conti, security companies found numerous links between the two groups. Advanced Intelligence said Karakurt is a side business of the group behind Conti, allowing them to monetize the data stolen during attacks in cases where organizations are able to block the ransomware encryption process.
Blockchain analysis firm Chainalysis has also previously identified several cryptocurrency wallets controlled by Karakurt that sent funds to Conti.
Callow noted that in addition to Pysa, Conti also has a history of targeting churches, noting the group’s attack on a Texas church in 2021.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



