Cybercrime group relentlessly targets aviation and transportation sectors for years
A little-known cybercrime group has been relentlessly targeting companies across several industry sectors, including aviation, defense, and transportation, since at least 2017, security firm Proofpoint said in a report published today.
Tracked using the codename of TA2541, the group has been one of the most persistent threats in recent years, even if their attacks have been largely unsophisticated and have relied on infecting and deploying commodity malware on targets’ networks.
Building on similar reports from Cisco Talos, Mandiant, Microsoft, Morphisec, and independent researchers, Proofpoint said TA2541 attacks typically follow the same pattern where they rely on large waves of spear-phishing emails to approach their targets.
These emails, almost always written in English, entice victims to download files typically hosted on cloud storage providers, knowing that links to these services are almost never blocked inside larger companies.
Once downloaded and executed, these files typically install a type of malware known as a remote access trojan (RAT) that grants TA2541 operators access to the infected computer.
Proofpoint said that across the years, it has seen the group use a wide assortment of RATs, but they’ve almost always relied on RATs that can be purchased from underground cybercrime forums.
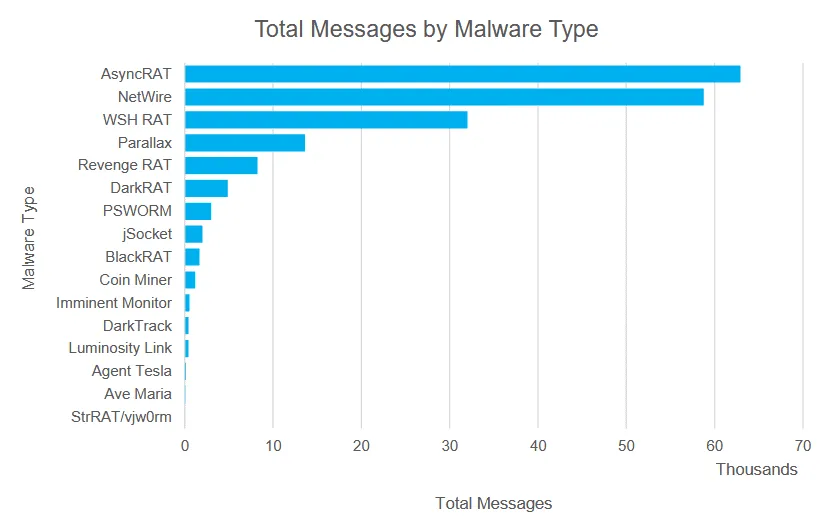
The security firm said that since 2017 it had seen TA2541 targeting companies from the aviation, transportation, manufacturing, and defense industries, from North America, Europe, and the Middle East.
Its spam campaigns have varied from hundreds to several thousands of messages per campaign.
“There appears to be a wide distribution across recipients, indicating TA2541 does not target people with specific roles and functions,” researchers said.
Furthermore, Proofpoint said that it also couldn’t tell what the exact purpose and goals of these attacks were, and it is currently unclear if the group is engaging in any form of espionage, theft, or monetization.
Adam Janofsky
is the founding editor-in-chief of The Record from Recorded Future News. He previously was the cybersecurity and privacy reporter for Protocol, and prior to that covered cybersecurity, AI, and other emerging technology for The Wall Street Journal.



