Cyber-mercenary group Void Balaur has been hacking companies for years
Cyber-security firm Trend Micro has published today a 46-page report detailing the history and activity of a hacker-for-hire group that has been advertising its services in the cybercrime underworld and conducting on-demand intrusions since the mid-2010s.
Named Void Balaur, the group was involved in attacks that targeted victims for both financial and surveillance gains. Past attacks targeted IT companies, telecoms, and activists, journalists, and religious leaders alike.
Trend Micro said that because of the large number of target overlaps, it initially thought Void Balaur to be related or a subgroup of APT28 (Pawn Storm), a codename used to track cyberattacks carried out by agents of Russia's military intelligence agency, the GRU.
"In total, we have observed a dozen email addresses that were targeted by both Pawn Storm during the period of 2014 to 2015, and by Void Balaur from 2020 to 2021," Trend Micro said today.
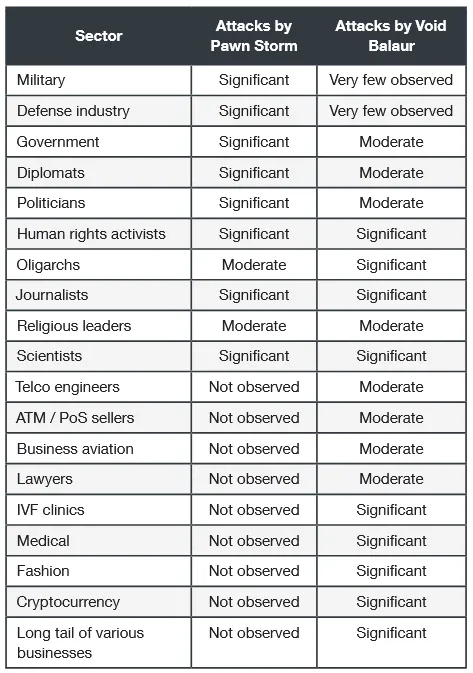
Group advertised services on hacking forums
However, at a closer look, researchers said that some of these attacks could be linked to the infrastructure of RocketHack.me, a website advertising on-demand hacking services.
The same site was referenced in numerous ads on Russian-speaking underground forums such as Probiv, Tenec, and Darkmoney, dating as far back as 2017.
"To our knowledge, Void Balaur has never advertised in underground forums that were not Russian language-oriented," Trend Micro researchers said.
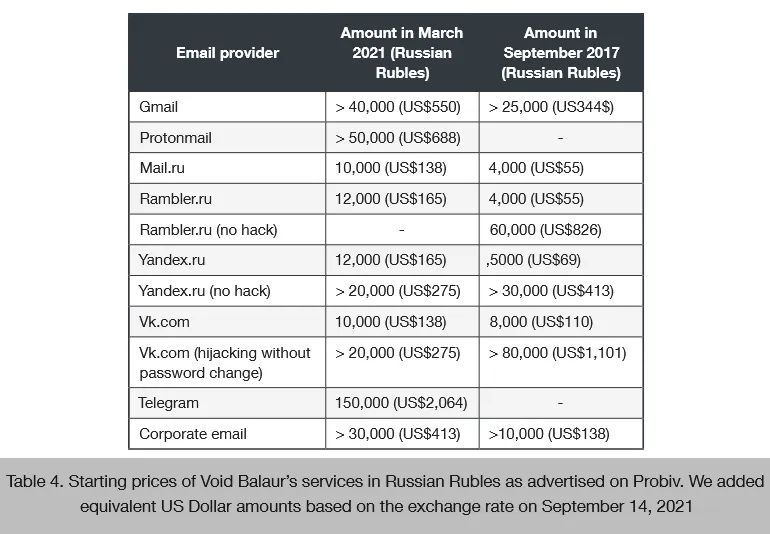
These ads initially referenced the group's ability to break into the victim's email and social media accounts, which seems to be consistent with the large number of phishing sites and run-of-the-mill infostealer malware Trend Micro found associated with the group's infrastructure.
"For some Russian email providers, copies of mailboxes are offered without any user interaction. We have no reason to doubt that this is a real business offering, because we have not seen negative feedback on Void Balaur in underground forums," the research team said.
"We don't know how customer data like emails are stolen without user interaction, but there are some scenarios where this would be possible," researchers said, pointing out to scenarios where Void Balaur used malicious insiders, a compromise of the entire email provider, or compromised the personal accounts of accounts employees or law enforcement officials that may have legal access to email inboxes.
A major shift occurred in 2019 when the group also began advertising the sale of very private and sensitive data of individuals from
Russia, including details from passports, driver licenses, private telephone records, and much more (see tables below).
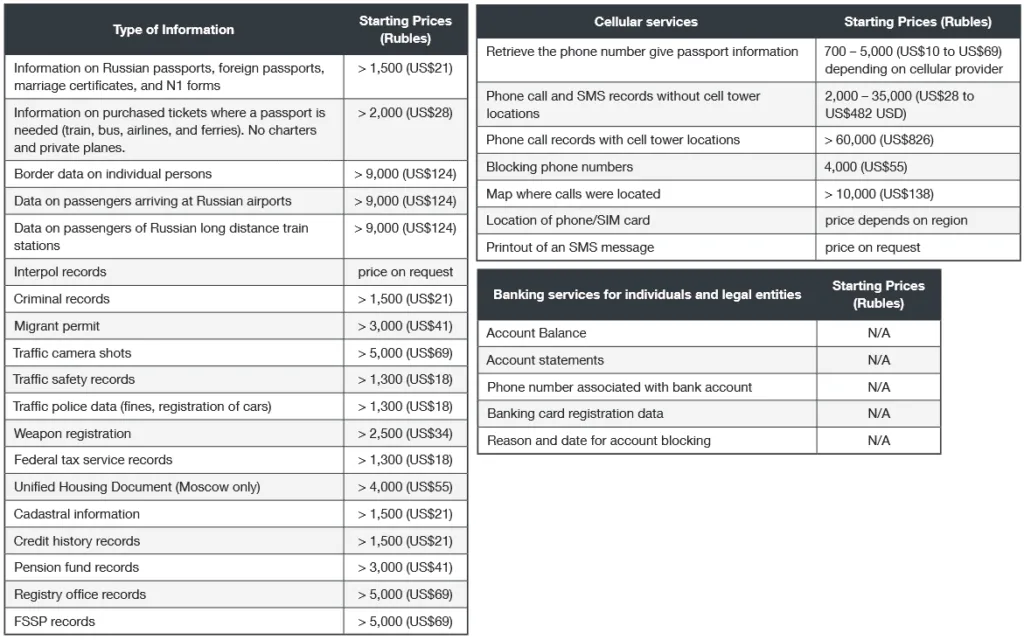
Trend Micro researchers couldn't exactly say how the group had access to this much data but pointed out its usefulness in Russia's underworld, where it could be abused to hide more serious crimes.
The telecom data that Void Balaur is peddling includes phone call records with cell tower locations that could reveal who a person has been calling, the duration of the calls, and the approximate location where the calls were made. Knowledge of these details could serve several purposes, including committing serious crimes. Furthermore, blocking phone numbers, a service that Void Balaur also offers, can help facilitate serious crimes — for example, by ensuring that someone is unreachable by phone while the crime is taking place. The price for getting phone call records with or without cell tower information varies a lot between different Russian providers, up to about a factor of ten. Apparently, getting phone records from some telecom companies are much easier than from others.
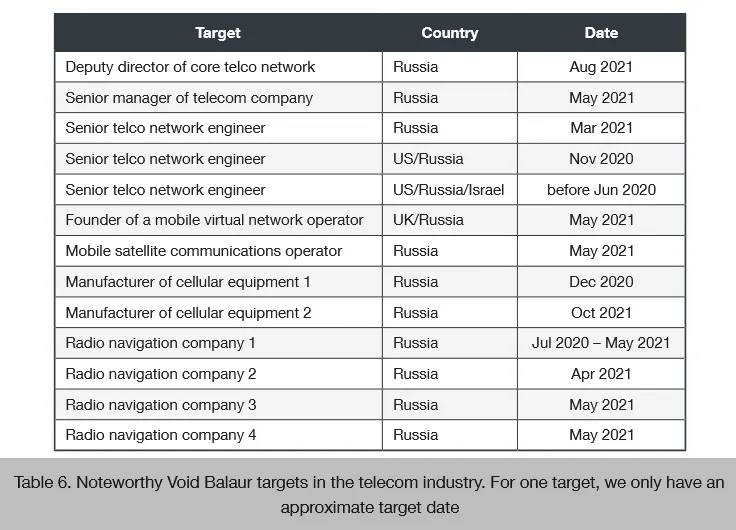
Trend Micro also said it found more than 3,500 email addresses that the group had targeted over the past few years as part of their attacks.
Many targeted telecom companies in Russia and the US, but the group also targeted lone individuals, such as activists and journalists.
In fact, Trend Micro said that a series of attacks against journalists and human rights activists in Uzbekistan in 2016 and 2017, described in this eQualitie report, was the work of Void Balaur.
"Amnesty International and eQualitie clearly indicate that the attacks in Uzbekistan had a serious impact on the lives of some individuals. This is a telling example of a cybermercenary providing services for a possibly larger campaign that is causing significant harm to human lives," the Trend Micro team said.
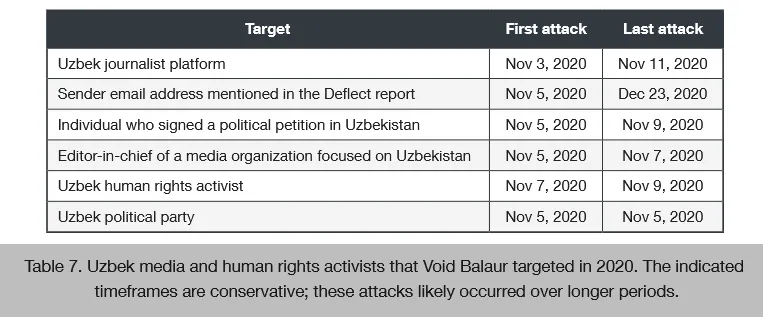
While researchers couldn't say who paid Void Balaur to target the Uzbek civil society targets, they did point out that the attacks took place even before the group posted its first ad on underground forums.
"The campaigns against Uzbek targets started as early as 2016 and were still ongoing as of 2020, according to our data (and probably even extended to 2021). This shows that Void Balaur is being hired for long-term campaigns, something we have seen for other targets as well," Trend Micro added.
More political targeting
But the attacks in Uzbekistan were just the beginning. Since then, Void Balaur's attacks against political targets have increased and diversified.
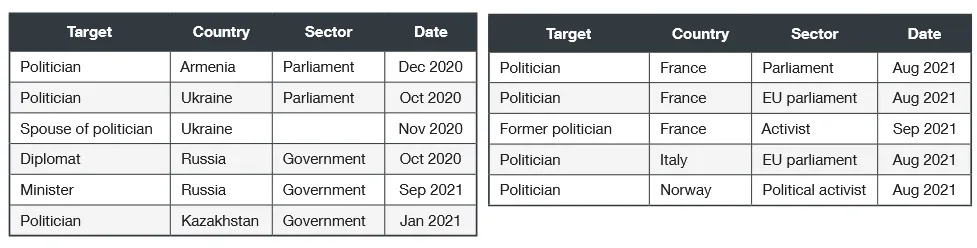
In 2020, the group was also seen targeting presidential candidates for the 2020 Belarus elections.
In August 2021, the group also targeted politicians and government officials in Ukraine, Slovakia, Russia, Kazakhstan, Armenia, Norway, France, and Italy.
In a more braze attack, in September 2021, the group also tried to gain access to the email inboxes of a "former head of an intelligence agency, five active government ministers (including the minister of defense) and two members of the national parliament of an Eastern European country."
"Some of these attacks were part of a larger campaign and not necessarily restricted to attacks over the internet alone. Some of the victims felt so threatened that they left their home countries and went into exile," Trend Micro said.
Attacks for economical and financial gain
Besides politicians, researchers said Void Balaur also targeted private companies.
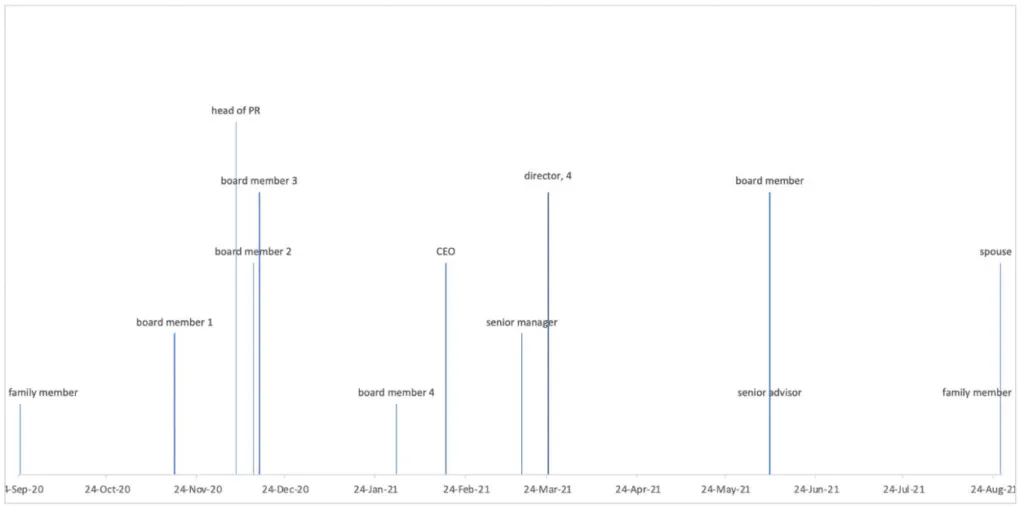
For example, the group targeted board members, executives, and directors of one of the largest conglomerates in Russia. The group went as far as to target even family members of the company's owner, a famous Russian billionaire.
The attacks lasted for almost a year, between September 2020 and August 2021.
Other targets of Void Balaur attacks included companies that typically have access to a vast amount of sensitive data, which researchers believe is what powered the group's ability to offer that data for sale on underground forums in the first place. Past targets include:
- Mobile and core telco companies
- Cellular equipment vendors
- Radio and satellite communication companies
- ATM machine vendors
- Point-of-sale (POS) system vendors
- Fintech companies and banks
- Business aviation companies
- Medical insurance organizations in at least three regions of Russia
- In Vitro Fertilization (IVF) clinics in Russia
- Biotechnology companies that offer genetic testing services
In addition, Trend Micro said that since 2018, Void Balaur has also operated several phishing sites that appear to have targeted cryptocurrency users. It is unclear if they operated these sites for themselves or for one of their clients.
Furthermore, additional details gathered from the timestamps of past attacks also shows that the group runs a professional operation with a strict work schedule.
It appears that Void Balaur usually starts the working day around 6 a.m. GMT and works until around 7 p.m. We saw hardly any activity from 10 p.m. to 4 a.m. GMT. While Void Balaur is less active during weekends, the actor often works seven days a week and does not take long vacations such as during Christmas or in the summer.
These timestamps, along with the group's long history of advertising on Russian-speaking forums, are a rather clear sign that the group operates from the territories of the old Soviet republics.
While the original Trend Micro report does not go into this, several questions and theories remain to be answered and explored.
- Do Void Balaur members have any ties with APT28?
- Is the group a contractor for some of APT28's past operations? (something that APT28 has done before, namely in the Yahoo hack)
- Is the group made up of any current or former APT28 members?
- Why didn't Russian authorities crack down on the group's past attacks against Russian targets? Does the group benefit from some sort of protection?
While past cyber-mercenary groups have been linked to public companies that operate a valid cyber weapons export business, Void Balaur represents a unique example on this landscape, with the group choosing to advertise its services on hacking forums rather than trade shows.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



