Cyber agencies warn of new TrueBot malware variants targeting US and Canadian firms
Cybersecurity agencies in the U.S. and Canada warned Thursday that threat actors are using new TrueBot malware variants to steal data from victims.
In an advisory co-written by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the FBI, the Multi-State Information Sharing and Analysis Center (MS-ISAC), and the Canadian Centre for Cyber Security (CCCS), the organizations said that as recently as May 31 they observed a surge in financially motivated TrueBot activity.
According to the agencies, TrueBot is a botnet that has been used by groups such as the Clop ransomware gang to exfiltrate data from infected devices. The malware was developed at least as far back as 2017 by a Russian-speaking hacking group known as Silence that was involved in high-profile attacks on financial institutions.
The malware traditionally spread through malicious phishing email attachments, but the agencies said threat actors have shifted their tactics and use new variants that rely on the exploitation of a remote code execution (RCE) vulnerability affecting the Netwrix Auditor application. More than 13,000 organizations across over 100 countries use the Texas-based company's software to help with IT auditing, security and compliance, according to Netwrix’s website.
“Based on confirmation from open-source reporting and analytical findings of Truebot variants, the authoring organizations assess cyber threat actors are leveraging both phishing campaigns with malicious redirect hyperlinks and CVE-2022-31199 [the Netwrix vulnerability] to deliver new Truebot malware variants,” the agencies said.
Cybersecurity researchers started warning about increased TrueBot activity shortly after the Netwrix Auditor vulnerability was disclosed in mid-2022. Researchers at Cisco Talos wrote in December that they “noticed a small number of cases” where TrueBot was executed after hackers exploited the Netwrix vulnerability, but they said it was “unlikely that the attackers managed to compromise a high number of systems this way.”
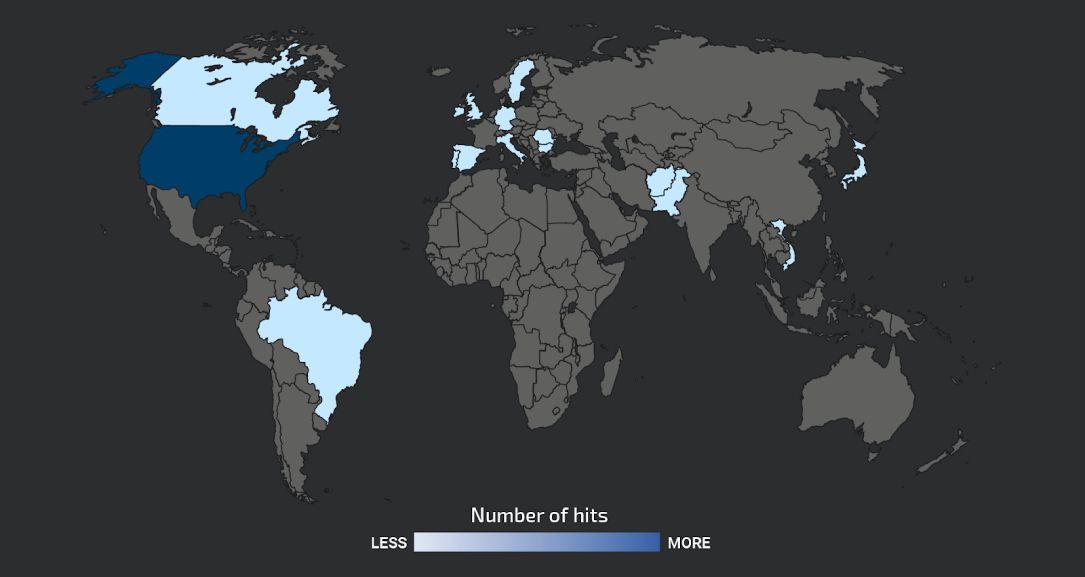 A new TrueBot botnet with over 500 infections by December 2022 was focused around the U.S. and Canada. Image: Cisco Talos
A new TrueBot botnet with over 500 infections by December 2022 was focused around the U.S. and Canada. Image: Cisco Talos
Talos researchers said they "started seeing a bigger uptick" in victims a couple months later, as hackers started using Raspberry Robin malware to deliver TrueBot to organizations mainly in Mexico, Brazil and Pakistan.
The advisory published Thursday did not name specific victims or say how many organizations have been targeted. The agencies published details about how to detect the malware and mitigate its effects, including applying patches for the Netwrix Auditor vulnerability and mandating multifactor authentication for all staff and services.
Adam Janofsky
is the founding editor-in-chief of The Record from Recorded Future News. He previously was the cybersecurity and privacy reporter for Protocol, and prior to that covered cybersecurity, AI, and other emerging technology for The Wall Street Journal.



