Crypto-mining gangs are running amok on free cloud computing platforms
Over the course of the last few months, some crypto-mining gangs have switched their modus operandi from attacking and hijacking unpatched servers to abusing the free tiers of cloud computing platforms.
Gangs have been operating by registering accounts on selected platforms, signing up for a free tier, and running a cryptocurrency mining app on the provider's free tier infrastructure.
After trial periods or free credits reach their limits, the groups register a new account and start from the first step, keeping the provider's servers at their upper usage limit and slowing down their normal operations.
Abuse reported at multiple providers
The Record has been observing and looking into this phenomenon since we first learned of this tactic six weeks ago when it was being abused on GitHub.
Since then, developers have shared their own stories about similar abuse they've seen on other platforms, and companies have come forward to share similar experiences of abuse.
The list of services that have been abused this way includes the likes of GitHub, GitLab, Microsoft Azure, TravisCI, LayerCI, CircleCI, Render, CloudBees CodeShip, Sourcehut, and Okteto.
In most of these incidents, the affected companies provide continuous integration (CI) services, which is a type of service that takes source code updates from developers to automatically build, package, and test applications before an administrator approves to ship the supplied changes into production.
In practice, cloud-hosted CI is done by spinning up a new virtual machine that performs the building, packaging, and testing process, and then delivers the result to a project's admin.
Crypto-mining gangs have realized that they could abuse this process to add their own code and have that CI virtual machine perform cryptocurrency mining operations to deliver small profits to the attacker before the VM's limited lifespan expires and the virtual machine is shut down by the cloud provider.
This is how crypto-mining gangs have been abusing GitHub's Actions feature, which provides a CI feature for GitHub users, to abuse the site and mine cryptocurrency with GitHub's own servers.
But GitHub hasn't been the only CI provider that has seen this tactic. Similar abuse has been observed at Microsoft Azure, LayerCI, TravisCI, Sourcehut, CloudBees CodeShip, and CircleCI.
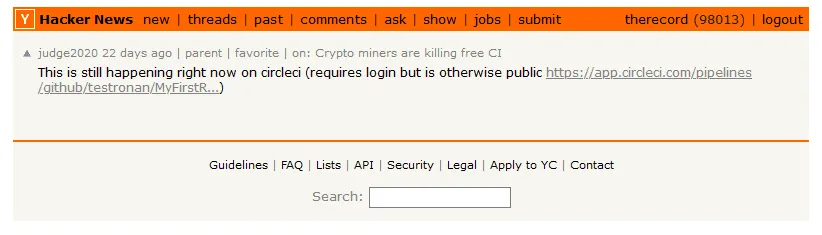
"Our team has been swamped with dealing with this kind of stuff," a CodeShip engineer told The Record in an online conversation.
"And it's not just the free accounts. Sometimes they pay the small fees for our accounts, which are way cheaper than renting on AWS directly, and mine cryptocurrency at maximum capacity."
Sourcehut, which despite being a pretty small and niche CI provider, has also reported similar abuse of its free tier.
"Malicious users have been deliberately submitting huge numbers of jobs under dozens of frequently registered accounts and deliberately circumventing our abuse detection to use as much of our resources as possible to mine cryptocurrencies," Sourcehut said in a blog post. "This exhausts our resources and leads to long build queues for normal users.
Microsoft, which also provides CI services through its Azure Pipelines feature, also faced similar abuse last year. However, the company didn't want to deal with all the headaches, most of which originated from the free grants it was giving away to the open-source community. Instead, starting February, the company revoked the ability for open-source projects to receive free grants to run CI pipelines and told free users to use GitHub Actions instead, where the GitHub staff is investing more in detecting abuse.
After a request for comment sent last week, GitLab, the second-largest coding platform today after GitHub, also came forward and published a blog post on Monday detailing similar abuse of its CI offering and ways to deal with it going forward.
"To discourage and reduce abuse, starting May 17, 2021, GitLab will require new free users to provide a valid credit or debit card number in order to use shared runners on GitLab.com," the company said, hoping this measure will prevent future abuse.
GitLab says it won't charge users of its free tier but will use the payment card to verify the user's identity through a one-time one-dollar transaction.
However, due to its larger size, GitLab can (still) afford to keep its free CI offering available for its users. Unfortunately, other smaller CI providers can't. At the time of writing, both Sourcehut and TravisCI said they plan to stop offering their free CI tiers as a result of the constant abuse in decisions they took to protect their paying customers, who were seeing a degradation of service.
Not just CI providers
But these attacks haven't been limited to CI providers. If it is a web service that provides free access to a high-computing system, crypto-mining gangs have most likely tried to abuse it by now.
Similar abuse has also been reported at website building service Render and at Kubernetes cluster hosting service Okteto, whose CEO, Ramiro Berrelleza, even gave a lightning talk at last year's eBPF conference on the topic.
Additionally, there are also many tutorials on some cryptocurrency forums that detail how someone could abuse the free trial period of Oracle Cloud or the cheap tiers of Alibaba Cloud to spin up a temporary cryptocurrency mining server for small one-time profits.
But while for service providers revoking free tier offerings might be a way to curtail the abuse they're seeing, this is not the optimal solution for lone developers using these offerings for their open-source projects.
An alternative solution, as proposed by Berrelleza, would be to deploy automated systems that detect and respond to this abuse. However, creating such systems requires resources that some companies might not be able to spare, nor will it guarantee that these systems work as intended.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.