Conti ransomware group adopts Log4Shell exploit
The Conti gang has become the first professional ransomware operation to adopt and incorporate the Log4Shell vulnerability in their daily operations.
Scans and attacks began as early as Monday, December 13, security firm Advanced Intelligence said in a report shared today with The Record.
The group specifically targeted VMWare vCenter servers, which are known to be vulnerable to Log4Shell attacks, where they used the exploit to gain access to the server and move laterally across enterprise networks.
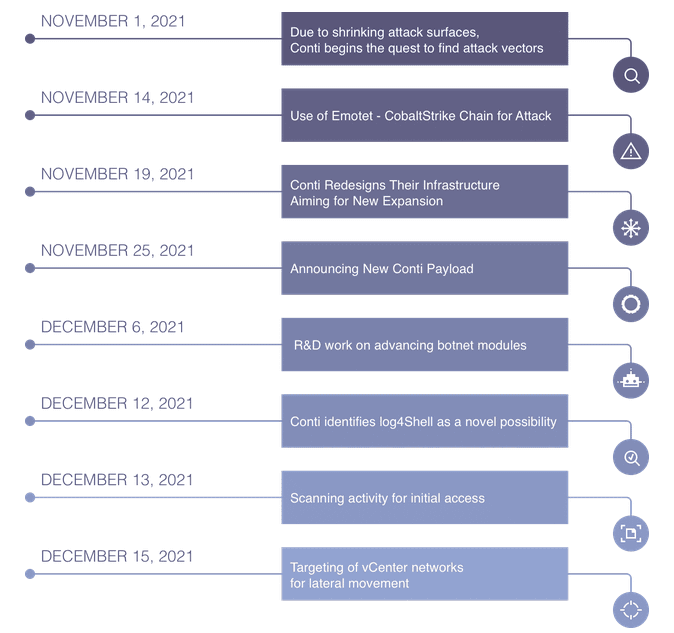
Conti now becomes the second ransomware strain delivered by exploiting the Log4Shell exploit after Khonsari.
It is, however, the actual threat, as Khonsari was identified to be more of a wiper deployed to Minecraft players via unofficial servers.
On the other hand, Conti is a professional ransomware gang that has been engaged in ransomware attacks for more than two years and is estimated to have made hundreds of millions of US dollars from attacking, encrypting, and ransoming corporate networks.
Conti's adoption of Log4Shell, a vulnerability in a nearly ubiquitous Java library, comes after state-sponsored cyber-espionage groups also began abusing this easy-to-exploit vulnerability earlier this week.
But while nation-state groups are normally interested in stealth and data collection, Conti's Log4Shell adoption effectively spells disaster for companies across the world, as the gang's attacks can cause massive disruptions to business operations and massive financial losses.
If there ever is a last moment when companies need to patch security flaws, it is usually when vulnerabilities get abused by ransomware gangs, meaning we're on the final stretch before Log4Shell gets abused for destructive attacks, beyond the mundane DDoS and cryptomining botnets we've seen so far over the past few weeks.
While companies using vCenter servers are the ones that should be looking into patching or deploying mitigations, the Log4j library is also used in a boatload of other enterprise software products, so Conti still has many options at its disposal to vary its attacks, meaning that patching this across the board, not just vCenter, is the way to go.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



