Notorious cybercrime gang Conti 'shuts down,' but its influence and talent are still out there
Cybersecurity researchers have confirmed that the highly active Conti gang officially took much of its infrastructure offline Thursday — a move expected to have ripple effects throughout the cybercrime underground as members shift alliances and business models.
Analysts at AdvIntel, a threat intelligence company that has closely watched Conti and its affiliates, on Friday publicly posted a long breakdown of what happened to the gang: Key features are gone from the official Conti News website, where it published victim data; the site the gang used for negotiating with ransomware victims was shut down; and other important pieces of infrastructure — chatrooms, messengers, servers and so on — were "going through a massive reset."
The shutdown "highlights a simple truth that has been evident for the Conti leadership since early Spring 2022 — the group can no longer sufficiently support and obtain extortion," write analysts Yelisey Bogusalvskiy and Vitali Kremez. "The blog's key and only valid purpose are to leak new datasets, and this operation is now gone."
The flameout comes as Conti is still executing a high-profile attack on the government of Costa Rica, which has not paid a ransom demand of $20 million. As of Friday, Conti was still issuing comments about the incident, including an aside that "the USA is a cancer on the body of the earth."
The AdvIntel analysts said the Costa Rica attack has a performative aspect to it: It wasn't just an attempt to make one final score — it was a way to create a distraction as Conti leaders planned to kill off their brand.
"The attack on Costa Rica indeed brought Conti into the spotlight, and helped them to maintain the illusion of life for just a bit longer, while the real restructuring was taking place," Bogusalvskiy and Kremez wrote. That is, the end of Conti won't look like what happened to REvil, another Russian-speaking cybercrime operation that took a direct hit from the Kremlin before its invasion of Ukraine, but whose servers still appear to operating in their old locations.
Ransomware split-up
The exact nature of Conti's restructuring — like so many things associated with the group — is unclear and probably still evolving. But the shakeup comes as cybersecurity researchers and law enforcement agencies have an unprecedented view into Conti's methods and culture, via a trove of files leaked earlier this year. Conti showed itself to be just like any other successful business, with highly motivated employees and a clear hierarchy.
But it's also helpful to remember that Conti is a group of criminals, according to Recorded Future ransomware expert Allan Liska.
"The facts, as far as I can tell, are that Conti has shut down a lot of their connected infrastructure and their chat servers. All of that is true," Liska said. "Conti has also stated that they are breaking into smaller groups that will be completely independent from each other. But, just because they say that doesn’t mean it is true."
The AdvIntel researchers suggest several outcomes for Conti's talent pool. One place to land would be with groups that avoid traditional "locker" malware that encrypts files and instead steal an organization's data and make extortion demands. Another option would be taking their skills to other ransomware groups that experts have linked to Conti, such as the ALPHV/BlackCat operation.
Other members could choose to work independently while staying loyal to their old Conti connections, AdvIntel said, or infiltrate "an already-existing small brand" and take it over, while "keeping the small brand name."
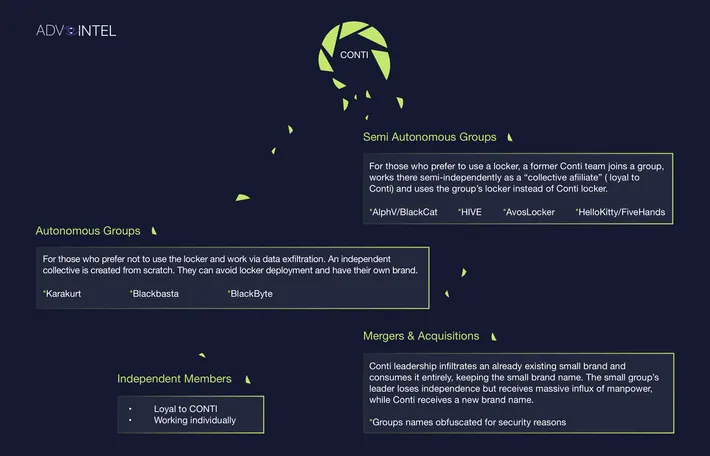
Breaking into smaller, more independent groups has advantages for operational security, Liska said, but other pressures will come with that kind of reorganization.
"So, this is something I personally have been worried about for a while, and it makes sense because it will be easier to stomp out leaks," Liska said about the diffusion of Conti talent. But that approach "also means less money for the leaders of Conti, and they don’t have a long of history of doing smart things that might cut into their profits."
At a minimum, Conti members know they have a home, one researcher noted.
"There is widespread permissiveness inside Russia for criminality," tweeted Sophos Principal Researcher Andrew Brandt, as long as "the victims are aligned with who the current Russian regime sees as its historic enemies."
Joe Warminsky
is the news editor for Recorded Future News. He has three decades of experience as an editor and writer in the Washington, D.C., area. He previously he helped lead CyberScoop for more than five years. Prior to that, he was a digital editor at WAMU 88.5, the NPR affiliate in Washington, and he spent more than a decade editing coverage of Congress for CQ Roll Call.



