CobaltSpam tool can flood Cobalt Strike malware servers
A security researcher has published this week a tool to flood Cobalt Strike servers — often used by malware gangs — with fake beacons in order to corrupt their internal databases of infected systems.
Named CobaltSpam, the tool was developed by security researcher Mario Henkel.
Henkel told The Record today that he created the tool on top of CobaltStrikeParser, a project from security firm SentinelOne that can be used to read information from Cobalt Strike server configurations.
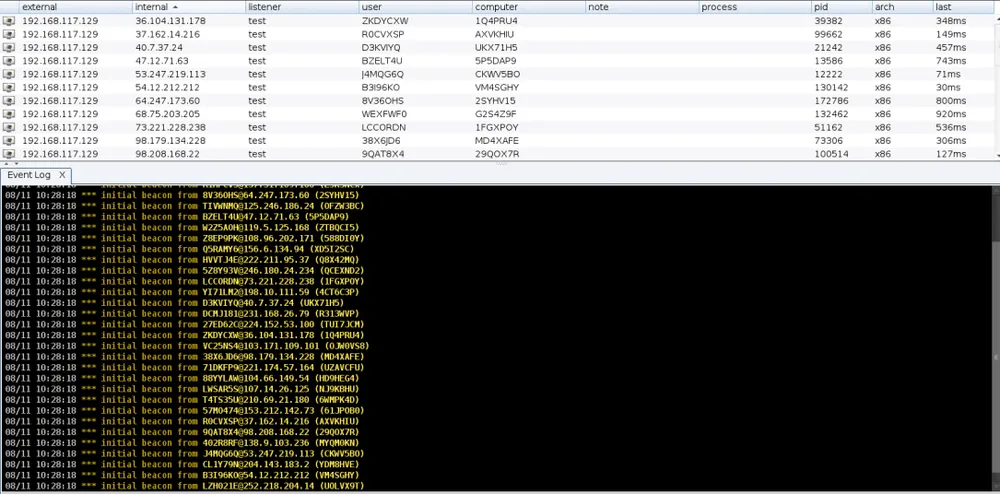
The researcher said he created a loop in the original code to ping a Cobalt Strike server and register new beacons, a term used in the Cobalt Strike documentation to describe a system infected with a Cobalt Strike backdoor.
While Cobalt Strike was developed as a tool for security experts to emulate threat actors in penetration tests, the tool became so good that in recent years it was broadly adopted by many malware operations, according to research from Intel 471, Proofpoint, and a Recorded Future report that found that Cobalt Strike and fellow penetration testing tool Metasploit accounted for more than a quarter of all the malware command and control (C&C) servers deployed in 2020.
The idea behind CobaltSpam is to provide defenders with a way to fight back. Once they identify a Cobalt Strike server, they can flood it with fake data in order to prevent the attacker from distinguishing between the real and fake infections.
Since Cobalt Strike is usually deployed in the initial stages of an infection, flooding a server might prevent attackers from reaching their goals and launching final payloads, such as ransomware, infostealers, or cryptominers.
CobaltSpam can generate thousands of fake entries per hour
Henkel told The Record that CobaltSpam works pretty fast and can generate between one or two fake beacons per second. With most Cobalt Strike malware campaigns typically infecting tens to hundreds of victims, servers can be flooded with tens of thousands of fake entries overnight.
This is also the second tool of this kind that Henkel has developed. The researcher previously released AzoSpam in 2019, a tool that can flood the backend of AZORult, a popular infostealer malware strain, with thousands of fake entries.
The tool, which worked only with AZORult 3.3, was successfully deployed several times to corrupt data collected from victims, with AZORult operators often choosing to wipe entire databases rather than spend their time sifting through the fake and real data, Henkel said.
CobaltSpam doesn't use HotCobalt bug
News of CobaltSpam's releases also comes after earlier this week, security firm SentinelOne published details about HotCobalt, a bug in the Cobalt Strike framework that could be used to remotely crash Cobalt Strike servers.
The bug was fixed by Core Security, the company behind the Cobalt Strike framework, but several security researchers argued it could still be used to crash malware servers today since most of them run on top of older cracked versions of the Cobalt Strike software and aren't usually kept up to date.
Asked by The Record, Henkel said that CobaltSpam doesn't use this bug but instead "speaks" to Cobalt Strike servers using their native interface, meaning it could be used against any server versions.
The release of the HotCobalt bug and the CobaltSpam tool also came on the same week when a security researcher published an open letter addressed to Core Security on behalf of the infosec community, asking the company to take steps and make it harder for malware gangs to abuse its software.
An open letter to @CoreSecurity regarding #CobaltStrike:https://t.co/Vj9mIK7Usw pic.twitter.com/aAoW4sf4s0
— James (@James_inthe_box) August 7, 2021
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.