Cloudflare says new hCaptcha bypass doesn't impact its implementation
Web infrastructure and website security provider Cloudflare told The Record last week that a recent academic paper detailing a method to bypass the hCaptcha image-based challenge system does not impact its implementation.
The research paper, published last month by two academics from the University of Louisiana at Lafayette, targets hCaptcha, a CAPTCHA service that replaced Google's reCAPTCHA in Cloudflare's website protection systems last year.
In a paper titled "A Low-Cost Attack against the hCaptcha System," researchers said they devised an attack that uses browser automation tools, image recognition, image classifiers, and machine learning algorithms to download hCaptcha puzzles, identify the content of an image, classify the image, and then solve the CAPTCHA's challenge.
Academics said their attack worked with a 95.93% accuracy rate and took around 18.76 seconds on average to crack an hCaptcha challenge.
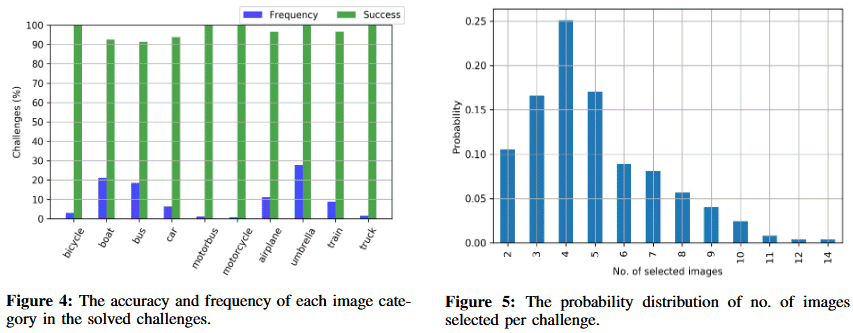
But while machine learning-based attacks on image-based CAPTCHA solutions have been discovered before, the major breakthrough in this paper is that the research team achieved this with minimal computational resources — with the attack rig consisting of a simple Docker container running Ubuntu OS, configured with a 3-core CPU and only 2GB of memory.
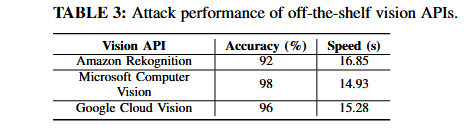
Further, the research team says the attack could work even faster if they'd replace their in-house image classifier with state-of-the-art online vision API services such as Google Cloud Vision, Amazon Rekognition, and Microsoft Azure Cognitive Vision, which could shave another one or two seconds on average.
The research team says these attacks, if implemented in the real world, could allow threat actors to bypass hCaptcha image-based puzzles on live websites and carry out automated attacks against a site's infrastructure, such as forum spam, web scraping, and more.
The attack, which researchers plan to present at the 2021 edition of the Workshop on Offensive Technologies (WOOT) next month, has worried some website owners, who are using it as part of their Cloudflare website security packages.
However, in a phone call in a phone call last week, on Friday, Nick Sullivan, Head of Research at Cloudflare, told The Record that "hCaptcha is one of various methods that Cloudflare uses to detect and potentially block automated traffic," and that there are additional systems in place to detect automated attacks.
Furthermore, reached out for comment last week, an hCaptcha spokesperson also said the organization was aware of the researcher's work and that they already implemented the techniques suggested in the paper's mitigation section.
However, hCaptcha also admitted that its free version would also not prevent all automated attacks due to several design decisions. The company's full answer is below:
We already employ the techniques in their "suggested mitigation" section, but our system is designed not to leak detections in real-time. By contrast, with reCAPTCHA you can simply sign up and get a bot score, which makes it trivial to break.
hCaptcha spokesperson
This limits options for the free version they tested, as by design it will not completely prevent all detected automation from passing when correct answers are submitted.
Instead, one of the tools it relies on is frequently changing the classes and types of challenges. However, it also has "anti-drain" protections to avoid leaking these.
Thus, our response to them after looking through the paper was that in fact the anti-drain protections were working as designed, based on the other details reported.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.