Cisco: Security devices are vulnerable to SNIcat data exfiltration technique
Networking equipment vendor Cisco said today that some of its security products fail to detect and stop traffic to malicious servers that abuse a technique called SNIcat to covertly steal data from inside corporate networks.
Affected devices include Cisco firewalls running FTD (Firepower Threat Defense) software, devices running the WSA (Web Security Appliance) modules, and all ISA3000 (Industrial Security Appliance) firewalls.
What is SNIcat?
First disclosed in August 2020, SNIcat is a data exfiltration technique discovered by Norwegian security firm mnemonic.
In particular, mnemonic researchers discovered that many popular network security devices were checking user traffic against their block-lists after the user's device negotiated a TLS handshake.
Starting from this premise, the mnemonic team developed a simple proof-of-concept Python script that would take sensitive information from a compromised computer and hide it inside the TLS Client Hello packet, which is exchanged at the beginning of a TLS handshake, and before the user's connection was checked for possible suspicious traffic.
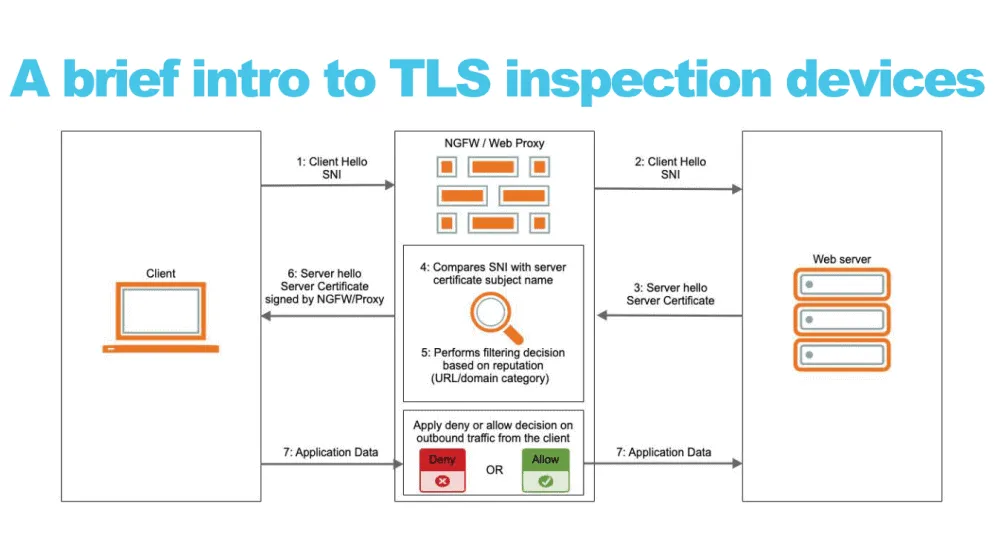
Last year, mnemonic said they had limited resources at their disposal and were only able to test a handful of devices for SNIcat exfiltration; however, they said that more vendors were also likely to be blind to this technique.
Today, Cisco became the fourth major network security vendor—after F5 Networks, Fortinet, and Palo Alto Networks—to formally admit that its devices can be bypassed using the SNIcat technique.
Check Point said its devices were not vulnerable.
Cisco is currently investigating several other device models and is expected to release patches and detection rules. See the company's official advisory for future updates.
Additional details on the SNIcat technique are also available in the video below, showing the mnemonic team presenting its findings at the Black Hat Europe 2020 security conference.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



