Cisco routers come under attack, including a destructive hacktivist campaign
Cisco ASA routers and FTD firewalls are currently seeing exploitation attempts from threat actors and bug bounty hunters alike after proof of concept code was posted online last week.
Furthermore, older Cisco systems have also seen renewed attacks in May this year after a hacktivist abused a 2018 bug to overwrite device configurations with a pro-gun manifesto that eventually crashed devices.
The Cisco ASA/FTD attacks
The most recent attacks are, however, those carried out against ASA and FTD devices. These attacks began last week after security firm Positive Technologies posted a simple proof-of-concept (PoC) exploit code on Twitter for CVE-2020-3580, a vulnerability the company discovered and helped patch in October last year.
PoC for XSS in Cisco ASA (CVE-2020-3580)
— PT SWARM (@ptswarm) June 24, 2021
POST /+CSCOE+/saml/sp/acs?tgname=a HTTP/1.1
Host: ciscoASA.local
Content-Type: application/x-www-form-urlencoded
Content-Length: 44
SAMLResponse="><svg/onload=alert('PTSwarm')> pic.twitter.com/c53MKSK9bg
Within an hour after the exploit code was posted online, Mikhail Klyuchnikov, a security researcher for Positive Technologies, said the PoC had already been used by bug hunters to find entry points into corporate networks, which some of them had reported to companies in the hopes of receiving a monetary reward (a bug bounty).
The hunt for low hanging CVE-2020-3580 by @ptswarm has begun.
— Mikhail Klyuchnikov (@m1ke_n1) June 24, 2021
A lot of submissions/duplicates are waiting for @Bugcrowd and @Hacker0x01 #bugbounty
However, white hats weren't the only ones that exploited this bug.
In a blog post on Friday, security firm Tenable said it received at least one report that the bug was also being actively exploited by threat actors.
The CVE-2020-3580 vulnerability, however, is not as dangerous as other past Cisco security flaws. This is because the bug requires tricking a user with an account on the device's admin interface to click a malicious link, a social engineering scenario that is not always easy to incorporate in mass attacks.
However, if exploited, the CVE-2020-3580 bug allows the attacker to execute malicious code on the ASA and FTD management panel with admin privileges via one of four different cross-site scripting (XSS) vulnerabilities present in unpatched devices.
Destructive hacktivist campaign
In addition to these campaigns last week, some older Cisco devices also saw a series of destructive attacks in May.
Spotted by Lumen's Black Lotus Labs, the campaign targeted devices that had the Smart Install protocol enabled and accessible over the internet.
Using the old CVE-2018-0171 vulnerability, a mysterious hacktivist gained access to Cisco systems and rewrote their config file with text from a pro-gun manifesto, effectively crashing the devices' routing engines.
Per the Black Lotus Lab team, this campaign hit around 100 of 18,000 Cisco devices still vulnerable to the old 2018 bug, with most victims based in the US.
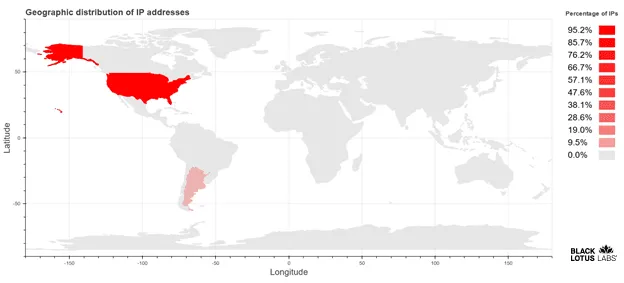
This also marks the second time this specific 2018 bug was exploited by hacktivists after a first group also used it to deface Cisco routers in Iran and Russia with an ASCII American flag and a message warning the two countries not to mess with the US elections.
This attack, which took place in the spring of 2018, hit more than 200,000 Cisco routers, including routers outside Iran and Russia.
All in all, both campaigns show why it's important to patch all bugs as soon as possible, even if proof-of-concept code was not immediately released after a bug was patched, as some old vulnerabilities might come back to haunt companies years later when that PoC code becomes broadly available to attackers.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



