Cisco confirms May attack by Yanluowang ransomware group
Cisco confirmed on Wednesday that it was attack by the Yanluowang ransomware group in May, but said the hackers were not able to steal sensitive data or impact the company's operations.
In a statement to The Record, Cisco said the incident occured on their corporate network in late May and that they “immediately took action to contain and eradicate the bad actors.”
“Cisco did not identify any impact to our business as a result of this incident, including Cisco products or services, sensitive customer data or sensitive employee information, intellectual property, or supply chain operations,” a Cisco spokesperson said.
The company’s security arm released a lengthy blog post about the incident, confirming that the Yanluowang group was behind the attack.
The ransomware group published some of the data it stole on Wednesday.
Yanluowang ransomware group claims to have breached Cisco.
— vx-underground (@vxunderground) August 10, 2022
Intel and images provided via @Gi7w0rm pic.twitter.com/HeW6k1VrR3
“On August 10 the bad actors published a list of files from this security incident to the dark web,” the Cisco spokesperson said. “We have also implemented additional measures to safeguard our systems and are sharing technical details to help protect the wider security community.”
In another statement posted online, Cisco claimed no ransomware was observed or deployed on its corporate IT infrastructure and the company said it “successfully blocked attempts to access Cisco’s network since discovering the incident.”
The company added that among a host of actions taken in response to the attack, it has reached out to law enforcement.
Cisco Security Incident Response (CSIRT) and Cisco Talos provided more details in a blog post, writing that the Yanluowang gang compromised a Cisco employee’s credentials “after an attacker gained control of a personal Google account where credentials saved in the victim’s browser were being synchronized.”
“The attacker conducted a series of sophisticated voice phishing attacks under the guise of various trusted organizations attempting to convince the victim to accept multi-factor authentication (MFA) push notifications initiated by the attacker,” the company’s security teams explained.
“The attacker ultimately succeeded in achieving an MFA push acceptance, granting them access to VPN in the context of the targeted user.”
The report adds that once the attacker obtained initial access, they enrolled a series of new devices for MFA and authenticated successfully to the Cisco VPN. The attacker then was able to escalate to administrative privileges, which allowed them to login to multiple systems. That action tipped off the Cisco Security Incident Response Team, but the group used several tools — ranging from remote access programs like LogMeIn and TeamViewer to offensive security tools such as Cobalt Strike, PowerSploit, Mimikatz, and Impacket — to maintain access.
While no internal systems were compromised, Cisco said the group tried a number of methods to minimize its footprint.
“We confirmed that the only successful data exfiltration that occurred during the attack included the contents of a Box folder that was associated with a compromised employee’s account,” Cisco’s security teams said. “The data obtained by the adversary in this case was not sensitive.”
While the Yanluowang group took credit for the attack, Cisco said it had moderate to high confidence that the initial attack was actually launched by an initial access broker with ties to other groups, including the UNC2447 cybercrime gang and the Lapsus$ threat actor group.
Cisco noted that after being kicked out of the network, the group emailed Cisco executives but did not make threats or extortion demands. They shared a screenshot showing the directory listing of the Box data that was previously exfiltrated.
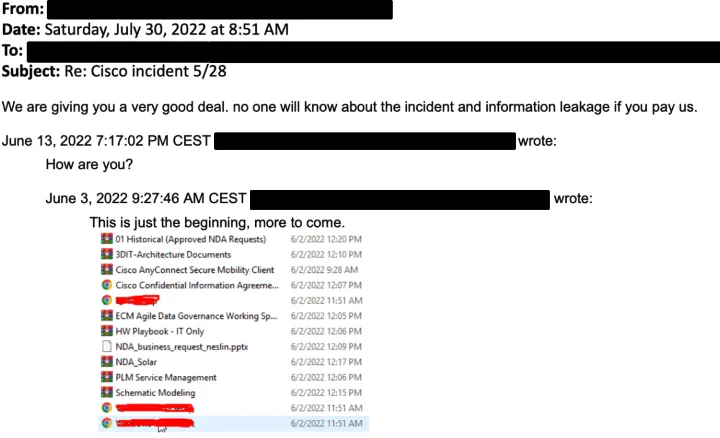
A week before publishing the stolen data, members of the Yanluowang gang contacted BleepingComputer to share some of the alleged 2.75 GB of data they stole. The news outlet went through the files and found non-disclosure agreements among other data.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



