CISA says federal agencies attacked in refund scam through remote management software
At least two federal civilian agencies were exploited by cybercriminals as part of a refund scam campaign perpetrated through the use of remote monitoring and management (RMM) software.
The Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency, and Multi-State Information Sharing and Analysis Center (MS-ISAC) said on Wednesday they discovered the campaign in October. One federal office was exploited in June and another was attacked in September.
“Specifically, cyber criminal actors sent phishing emails that led to the download of legitimate RMM software — ScreenConnect (now ConnectWise Control) and AnyDesk — which the actors used in a refund scam to steal money from victim bank accounts,” CISA said. RMM software is typically used by IT departments as a way to get remote access to a computer.
“They first connected to the recipient’s system and enticed the recipient to log into their bank account while remaining connected to the system. The actors then used their access through the RMM software to modify the recipient’s bank account summary. The falsely modified bank account summary showed the recipient was mistakenly refunded an excess amount of money. The actors then instructed the recipient to ‘refund' this excess amount to the scam operator."
CISA and the NSA warned that while this specific campaign was financially motivated, there are concerns that this tactic could be used for other nefarious purposes.
The agencies theorized that threat actors could sell access to an exploited victim to government-backed hacking groups – noting that both cybercriminals and nation-states use RMM software as a backdoor to maintain their access to a system.
RMM software allows hackers to establish local user access without the need for higher administrative privileges, “effectively bypassing common software controls and risk management assumptions,” according to the agencies.
Both incidents involved help desk-themed phishing emails sent to employees’ personal and work email addresses.
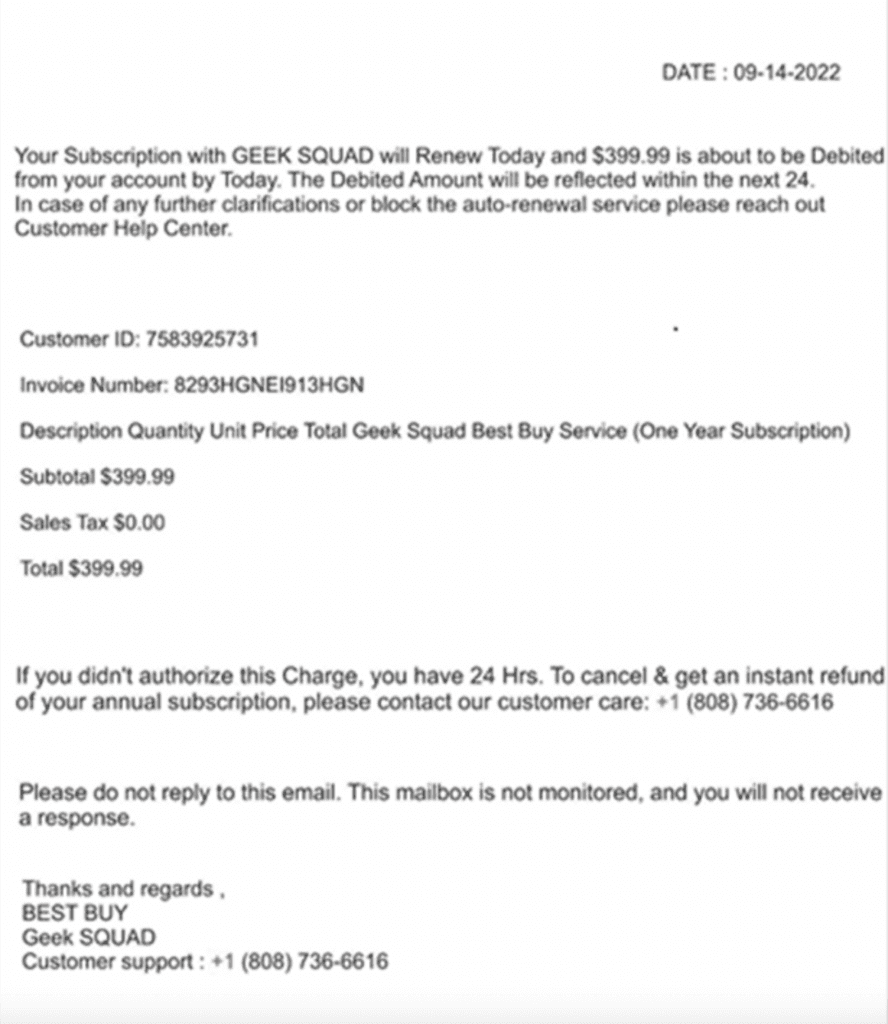
In the June incident, a phishing email with a phone number was sent to a government employee address. The employee called the number and was sent to myhelpcare[.]online.
The September incident, meanwhile, contained a link to a malicious domain.
From there, the hackers downloaded AnyDesk and ScreenConnect as “self-contained, portable executables” that were then configured to connect to the actor’s RMM server. CISA noted that the hackers did not install the downloaded RMM software onto the victim devices, instead using portable executables that can launch within a user’s device without installation.
“Because portable executables do not require administrator privileges, they can allow execution of unapproved software even if a risk management control may be in place to audit or block the same software’s installation on the network,” CISA explained.
“Threat actors can leverage a portable executable with local user rights to attack other vulnerable machines within the local intranet or establish long term persistent access as a local user service.”
CISA said it found several different domain names used in the first stage of the scam, including service[.]live, gscare[.]live, nhelpcare[.]info, deskcareme[.]live, nhelpcare[.]cc). Many of these domains attempt to impersonate well-known companies and brands like Norton, GeekSupport, Geek Squad, Amazon, Microsoft, McAfee, and PayPal.
Once the hackers can connect to a victim’s system, they ask the person to log into their bank account. The cybercriminals changed bank account summaries to make it look like the victim had been refunded too much money and asks the victim to “return” funds to the scam operator.
While this campaign involved ConnectWise Control (formerly ScreenConnect), and AnyDesk, any RMM software could be used, according to CISA. RMM software typically does not trigger antivirus or antimalware defenses, making it an ideal tool for cybercriminals.
Both companies have been used in previous cyberattacks. In February 2019, the Gandcrab ransomware gang abused a vulnerability in a Kaseya plugin for the ConnectWise Manage software to deploy ransomware on the networks of managed service providers’ customer networks.
Microsoft said in November that it saw the Royal ransomware group deliver malware through phishing emails that posed as legitimate installers for AnyDesk.
Leaked files from the Conti ransomware group showed they also used AnyDesk as one way to maintain persistence and remote access to a victim’s network.
#Conti ransomware affiliates using AnyDesk, Atera, Splashtop, Remote Utilities and ScreenConnect to maintain network access. During initial stage of IR I recommend blocking ALL remote access tools via Application Control policies, allow only the ones required & monitor their use.
— PeterM (@AltShiftPrtScn) August 5, 2021
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



