CISA orders civilian agencies to patch Zimbra bug after mass exploitation
The Cybersecurity and Infrastructure Security Agency added two vulnerabilities found in products from digital collaboration platform Zimbra after a cybersecurity company reported mass exploitation of the bugs throughout July and in early August.
On Wednesday, Zimbra released an advisory urging its customers running older versions of the software to immediately install updates. CISA ordered all civilian agencies to install the patches before September 1.
Zimbra’s Barry De Graaff said the fixes address an authentication bypass in MailboxImportServlet – CVE-2022-37042 and CVE-2022-27925.
Cybersecurity firm Volexity published a report this week noting that it worked on multiple incidents where the victim organization experienced serious breaches to their Zimbra Collaboration Suite (ZCS) email servers through exploitation of CVE-2022-27925, a remote-code-execution vulnerability in ZCS.
Volexity explained that CVE-2022-27925 was patched in March and was very difficult to exploit because it required valid administrator credentials.
CVE-2022-27925 facilitated writing #webshells to disk and was patched months ago. However, it was deemed lower priority because it required admin creds to exploit. Enter CVE-2022-37042 ... which bypassed authentication making this a CRITICAL and trivial to exploit vulnerability.
— Steven Adair (@stevenadair) August 11, 2022
But through its investigations, the company’s researchers found exploitation with no evidence the attackers had the prerequisite authenticated administrative sessions needed to exploit it.
They reported the issue to Zimbra, which patched the vulnerability in July and assigned the issue a new name: CVE-2022-37042.
“Through multiple investigations, evidence was uncovered indicating that CVE-2022-27925 was being mass exploited with the authentication bypass as early the end of June 2022. Volexity believes this vulnerability was exploited in a manner consistent with what it saw with Microsoft Exchange 0-day vulnerabilities it discovered in early 2021,” the company said.
“Initially it was exploited by espionage-oriented threat actors, but was later picked up by other threat actors and used in mass-exploitation attempts.”
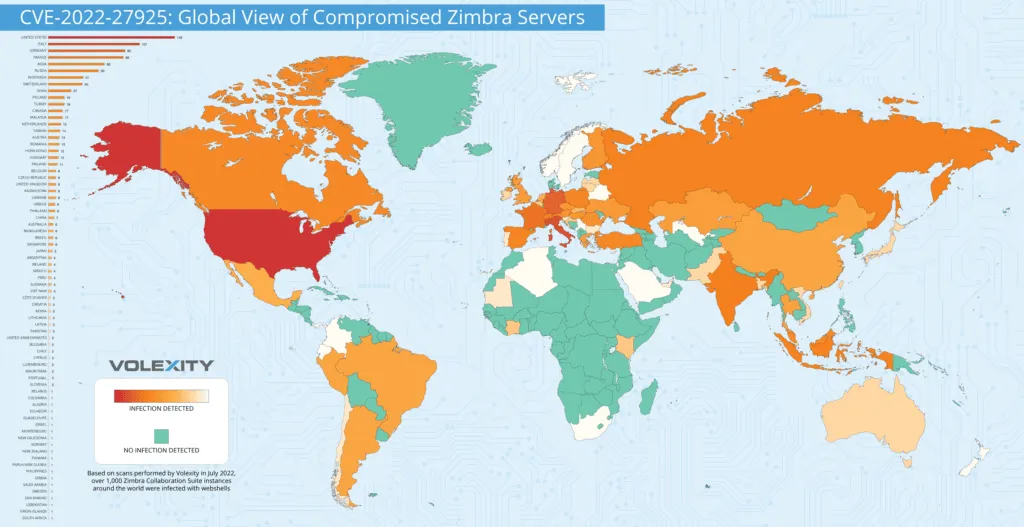
The company later scanned the internet, finding more than 1,000 ZCS instances around the world that were backdoored and compromised, but Volexity researchers noted that it is likely that the true number of compromised servers is higher.
Nearly 150 were found in the U.S. while over 100 are in Italy and 90 are in Denmark. Volexity said it notified local CERTs of compromised Zimbra instances in their constituency.
The company added that the bug may not be the only exploit for ZCS in use by hackers. CISA itself warned on August 4 that CVE-2022-27924, another ZCS bug, was being exploited and ordered civilian agencies to patch it by August 25.
CISA likely added the bug to its list due to “other active incidents involving breaches beginning with ZCS compromise,” according to Volexity.
“If your organization runs ZCS and did not apply patches 8.8.15P31 or 9.0.0P24 before the end of May 2022, you should consider your ZCS instance may be compromised (and thus all data on it, including email content, may be stolen) and perform a full analysis of the server,” Volexity explained.
“Based on limited testing by Volexity, it seems that patching ZCS instances to the newest version may remove webshells placed in some directories. However, if an attacker installed any second-stage or persistent malware (run via cron), then patching your ZCS instance is insufficient to remediate the compromise.”
Netenrich’s John Bambenek said his main concern with the bugs uncovered recently is centered on how many organizations use Zimbra.
Collaboration tools often have valuable trade secrets, however, the casual conversations that occur there often obscure the seriousness of the value that resides there, Bambenek said.
“In addition, many Zimbra users are smaller, therefore they likely lack security teams and even IT teams may be understaffed so they may not even know there is a problem, much less have the time and availability to address patching,” he explained.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



