CISA adds seven bugs to Known Exploited Vulnerabilities Catalog
The Cybersecurity and Infrastructure Security Agency (CISA) added seven vulnerabilities to its catalog of Known Exploited Vulnerabilities.
The vulnerabilities added include an arbitrary file upload vulnerability in Trend Micro Apex Central; an insufficient access control issue in Dell's dbutil driver; an improper authorization vulnerability in QNAP NAS instances running HBS 3; an authentication bypass vulnerability in the User Portal and Webadmin of Sophos Firewall; a vulnerability in Microsoft Windows User Profile Service and two authentication bypass vulnerabilities involving Dasan's Gigabit Passive Optical Network (GPON) Routers.
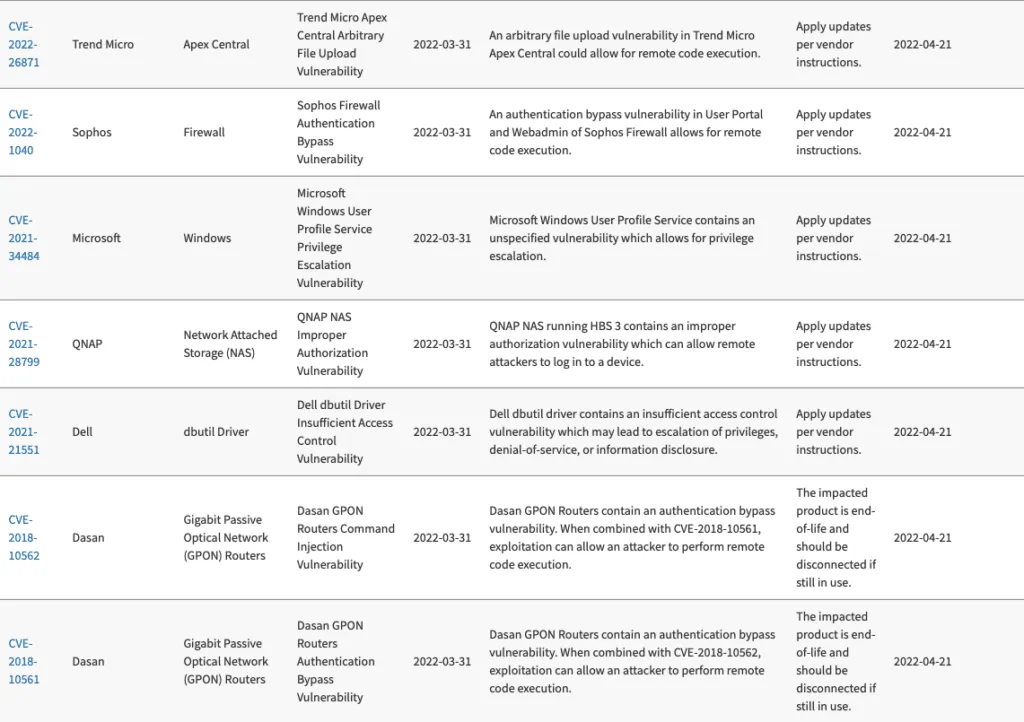
All of the vulnerabilities have remediation dates of April 21, and CISA said the seven additions were “based on evidence of active exploitation.”
“These types of vulnerabilities are a frequent attack vector for malicious cyber actors and pose significant risk to the federal enterprise,” CISA explained.
Sophos released a security advisory about CVE-2022-1040, noting that it was reported through their bug bounty program and has been fixed.
“Sophos has observed this vulnerability being used to target a small set of specific organizations primarily in the South Asia region,” the notice added, highlighting that it has a 9.8 CVSS score.
Trend Micro also released its own notice on CVE-2022-26871, noting that it has a CVSS score of 8.6.
“Trend Micro has observed an active attempt of exploitation against this vulnerability in-the-wild (ITW) in a very limited number of instances, and we have been in contact with these customers already. All customers are strongly encouraged to update to the latest version as soon as possible,” the company said.
The QNAP vulnerability relates to an issue that was identified and patched in April 2021. Last year, Palo Alto said ransomware gangs like eCh0raix were targeting the vulnerability.
Bud Broomhead, CEO at security firm Viakoo, said two of the seven vulnerabilities can’t be patched due to the product being obsoleted and the manufacturer not being able to provide a patch, referencing the two vulnerabilities affecting Dasan's routers.
Dasan told VPNmentor in March that, using its sales records, it believes about 240,000 units are impacted by the vulnerabilities. But they said “given the relative maturity of the products in their lifecycle, we think the impact is limited to even fewer devices.”
“Unlike most of the known exploited vulnerabilities in the CISA catalog, two of these vulnerabilities (Trend Micro CVE-2022-26871 and Sophos CVE-2022-1040) were just discovered in the last few days,” Broomhead explained.
“This means the timing of developing a patch, distributing it, and deploying it is much shorter than with others. Organizations should be extra vigilant with these patches as the normal testing process may have been rushed given how these are brand new, being exploited, and high severity.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



