CISA adds Oracle, SugarCRM bugs to exploited vulnerabilities list
The Cybersecurity and Infrastructure Security Agency (CISA) said two vulnerabilities from Oracle and SugarCRM are actively being exploited and ordered federal civilian agencies to patch them before February 23.
On Thursday, CISA added CVE-2022-21587 – affecting Oracle's E-Business suite – and CVE-2023-22952 – which affects multiple products from SugarCRM – to its Known Exploited Vulnerabilities Catalog. As with all additions to the list, CISA explained that the vulnerabilities are “frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise.”
Oracle patched CVE-2022-21587 in October and several experts said the E-Business suite has a broad user base, making it critical for patches to be installed as soon as possible.
The bug has a 9.8 CVSS score out of a possible 10 and was highlighted by the government of Singapore as a particularly dangerous bug because it is “easily exploitable.”
The SugarCRM vulnerability carries a CVSS score of 8.8 but caused more talk among security experts because an exploit for the bug was released on December 30. Researchers at Censys said on January 11 that their system found 3,059 instances of SugarCRM on the internet and 354 unique IP addresses containing the exploit’s installed webshell.
A security expert said on Mastodon that they saw cryptomining malware being used in association with the exploit.
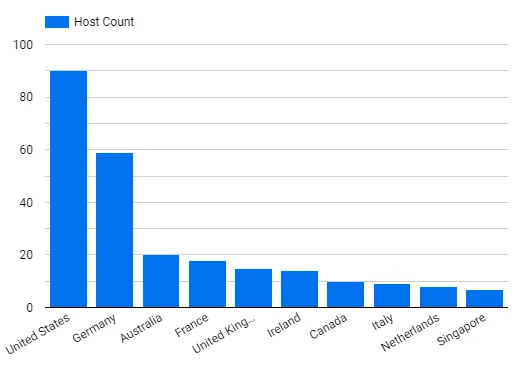
SugarCRM released a report on January 13 claiming that “no intrusion has been detected in any instances of Sugar Sell, Enterprise, Professional, Serve, and Ultimate software solutions running in the SugarCloud.”
“The vulnerability did not impact our Sugar Market software solution,” the company said two weeks ago.
Andrew Barratt, vice president at Coalfire, told The Record that SugarCRM is a hugely popular customer relations management product often used by small and medium enterprises as well as middle market organizations.
“The vulnerability announced allows for remote code execution which creates substantial amounts of risk,” he said.
“CRM tools typically have large amounts of both personal data and commercially sensitive information. Often these are a treasure trove of deals and opportunities. There is downstream risk though if a CRM is compromised whilst the data might be considered to belong to the user. That data is probably relevant to many of their customers creating an amplification of the issue.”
Netenrich’s John Bambenek noted that the two vulnerabilities represented two very different market segments, illustrating the wide array of targets nation-states and cybercriminals now have access to.
“SugarCRM is going after the small business market and those who don’t have the resourcing to pay for and fully realize the value of SalesForce,” he said. “Oracle is on the other end of that spectrum with many enterprise users. This highlights that all market segments attract APT and nation-state risks that should enforce the need to make sure updates are applied as quickly as they come out.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



