CISA adds Apple zero-day, Cisco and Gigabyte bugs to exploited vulnerabilities list
The Cybersecurity and Infrastructure Security Agency (CISA) added several vulnerabilities to its list of bugs currently being exploited by hackers, ordering all federal civilian agencies to patch the bugs before November 15.
On Tuesday, CISA added a zero-day vulnerability affecting all iPhone 8 and later models as well as several iPad models.
“An application may be able to execute arbitrary code with kernel privileges,” Apple explained in an advisory on Monday. “Apple is aware of a report that this issue may have been actively exploited.”
It is the ninth zero-day affecting Apple devices that has been exploited this year and Apple addressed the bug in its latest iOS update.
Michael Covington of the Apple-focused cybersecurity company Jamf explained that the bug allowed rogue applications to write data to a location it should not have been allowed to access, resulting in data corruption or unauthorized code execution.
“The latest security fixes from Apple are a good reminder that even the most recent software releases can contain bugs,” he said. “Details on the vulnerabilities are still emerging, but we know that eight of the issues fixed were being actively exploited.”
Ryan Cribelar, vulnerability research engineer at Nucleus Security, said the issue was part of a larger trend of vulnerabilities related to the kernel – effectively the foundation of a computer's operating system.
Cribelar explained that for Apple and others, the kernel is becoming a more popular home for threat actors to explore unfound exploitation – something that has had global implications in recent months with the controversy surrounding spyware makers employed by governments.
“I think part of it stems from an increase in Linux-based malware, but also the continuing pressure on the spyware industry. Targeting high-value individuals that would fall victim to spyware stems highly from zero-days a lot like this one,” he said.
Vulcan Cyber’s Mike Parkin echoed that assessment, adding that anything that could potentially allow remote code execution with kernel privileges is problematic.
Gigabyte and Cisco
CISA also added six other vulnerabilities to its list yesterday — four from hardware company Gigabyte and two affecting Cisco products.
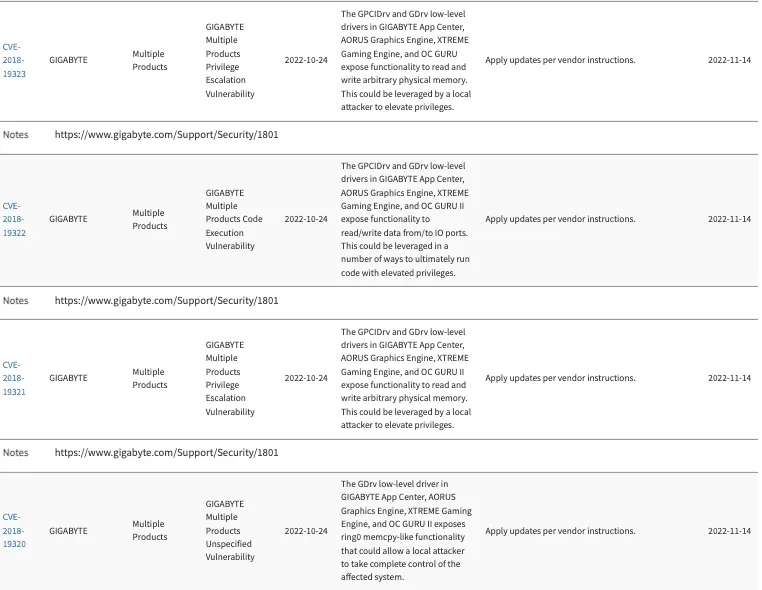
People who use Gigabyte products typically build their own custom PCs for playing video games at home, Cribelar told The Record, adding that these are suitable for mining cryptocurrency and “are a great target for a rogue nation looking to use cryptocurrency as a way to evade sanctions.”
According to Cribelar, a proof of concept exploit for the Gigabyte vulnerabilities has been available since 2019.
“In the case of the GIGABYTE vulnerabilities, the addition could mean anything from nation-state actors pulling off a sophisticated attack against a high-value target's home network,” he said. “Or it could simply be that gaming PCs are rampant with hardware for crypto mining capabilities, and are a high-yielding target."
The other vulnerabilities added to CISA’s list concern issues affecting Cisco’s AnyConnect Secure Mobility Client for Windows. A proof of concept exploit for both of the vulnerabilities – CVE-2020-3433 and CVE-2020-3153 – has been available on GitHub since September 2020.
A patch has been available since August 5, 2020, but yesterday Cisco updated their advisory on the issue, noting that its Product Security Incident Response Team “became aware of additional attempted exploitation” in October 2022.
Cribelar theorized that the issue is part of a larger trend of exploiting transition to working from home, noting that there has been a “fluctuation of disclosure of vulnerabilities in vital technologies like VPN.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.

