Chinese provincial security teams used spyware to collect texts, audio recordings
Multiple province-level security bureaus in China are using a powerful spyware tool to steal extensive data on targets — including texts, audio recordings and location data.
Named EagleMsgSpy, the tool has been used by public security bureaus across China since at least 2017, according to researchers at cybersecurity firm Lookout.
The researchers said development of the tool has continued throughout 2024, with the company behind it adding new capabilities and obfuscation features.
"What stood out most about this specific discovery is that the malware collects such an extensive amount of sensitive data — including encrypted messages across a variety of apps such as Telegram and WhatsApp, as well as the fact that there seems to be widespread connections to public security bureaus,” Kristina Balaam, senior security intelligence researcher at Lookout, told Recorded Future News.
“But what we found most alarming is that this seems to be just one example of broader contracted surveillanceware being leveraged by law-enforcement based on the number of additional calls for proposals we saw asking for similar products."
Lookout has been tracking EagleMsgSpy for years, first identifying it publicly in January 2023. The surveillanceware consists of an installer and an application that runs on Android mobile devices.
The powerful tool was built by Wuhan Chinasoft Token Information Technology and allows users to collect third-party chat messages, screenshots and screen recordings, audio recordings, call logs, device contacts, SMS messages, location data and network activity.
It collects messages from messaging apps popular in China, like QQ, Viber, WhatsApp, WeChat and Telegram. The data stolen is collected in a staging area before being compressed and sent to an external server.
In a lengthy report, Lookout researchers said they gained access to several versions of the tool and internal documents that indicate there may be a version for Apple devices.
The researchers noted that the tool may require physical access to the device in order to install it because the app is not available in Google Play or other app stores. The instruction manuals obtained said the surveillance tool was either installed through a USB plugged into the device or through a QR code.
The files holding the malware and its associated programs are given bland names to not raise suspicions. More recent versions of the malware have taken greater effort to hide the tool on phones.
Customers are offered an administrative panel with geographical maps tied to the device’s location as well as top-10 lists for the people contacted through the device.
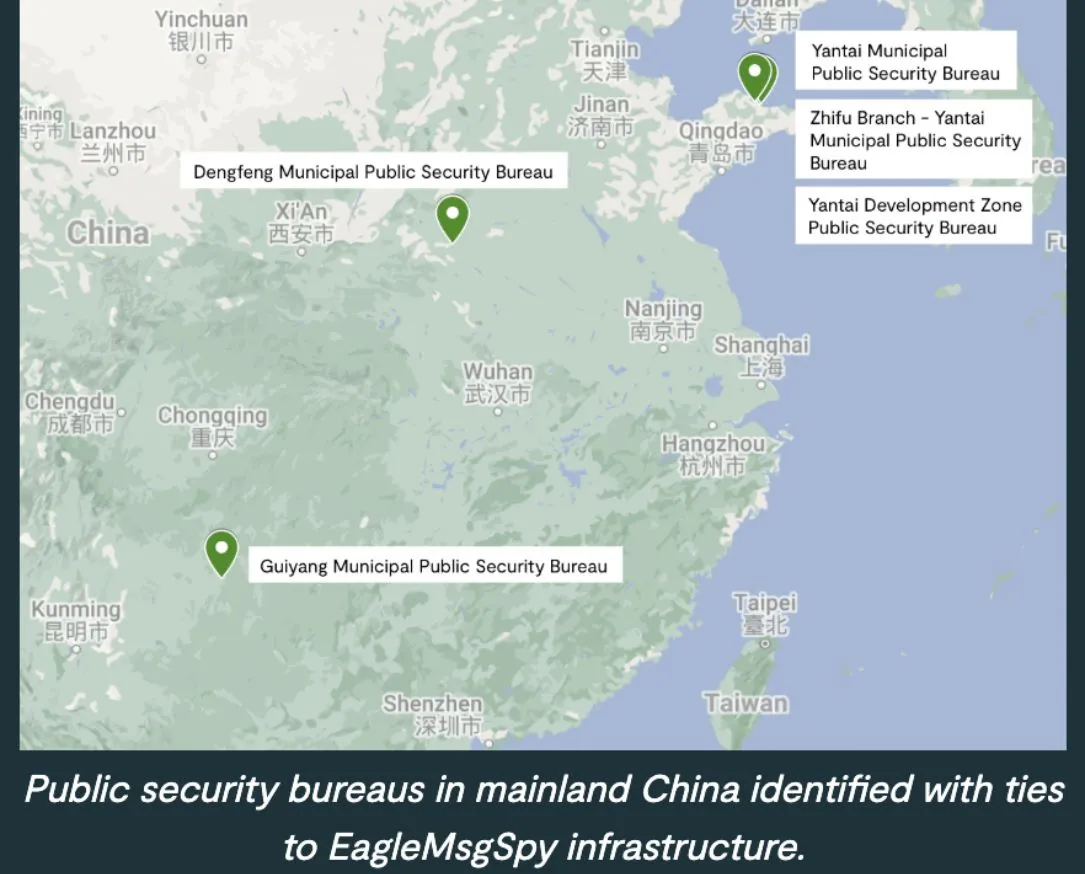
Image: Lookout
“The administrator is also able to trigger real-time photo collection from a device, real-time screenshot collection, block incoming and outgoing calls and SMS messages to specific phone numbers, and initiate real-time audio recording from the device,” the researchers said.
The infrastructure associated with the surveillance tool pointed to it being used by multiple public security bureaus, which in China are government offices that effectively act as local police stations.
The researchers said other documents showed EagleMsgSpy was one of several mobile surveillance tools that Chinese law enforcement used and some of the infrastructure associated with the malware were used with PluginPhantom — a tool previously deployed by Chinese hacking groups — and another surveillance tool called CarbonSteal that was used in campaigns targeting minorities in China, including Uyghurs and Tibetans.
The report notes that there are potential connections between the developers of the malware and Topsec – one of the biggest network security companies in China, according to experts.
On Tuesday, a former subsidiary of Topsec was sanctioned and indicted by U.S. officials for its role in compromising thousands of firewalls around the world.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



