Chinese military unit accused of cyber-espionage bought multiple Western antivirus products
A Chinese military unit that was accused last month by Japanese authorities of carrying out a years-long cyber-espionage campaign was seen buying batches of different Western-made antivirus products.
According to multiple procurement documents found by Recorded Future's Insikt Group, Unit 61419 of the Chinese People's Liberation Army (PLA) bought small batches of different antivirus products in early 2019.
The purchases, carried out through local intermediaries, were for antivirus products from companies such as Kaspersky, Bitdefender, Trend Micro, ESET, Dr.Web, Sophos, Symantec, McAfee, and Avira.
The purchases were for small batches varying from 10 to 20 workstation licenses.
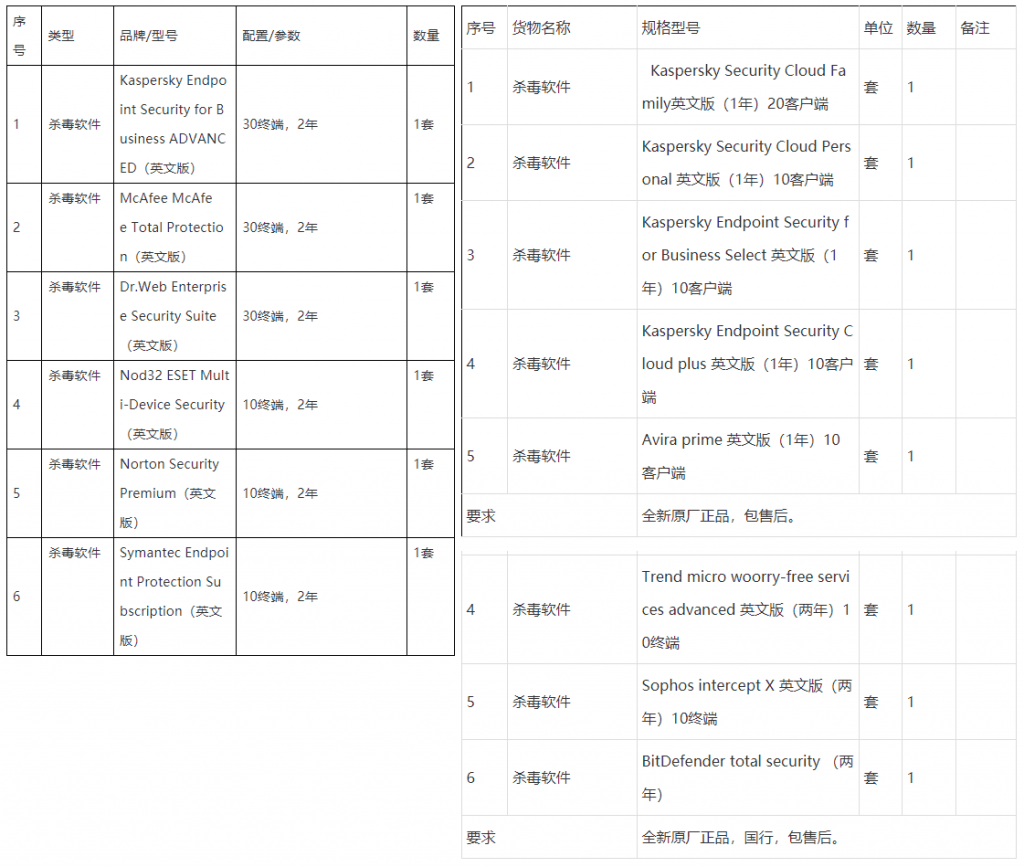
According to Insikt Group analysts, Unit 61419 unit bought the English versions of the software rather than the localized versions.
"This makes it highly unlikely that the purchases are being used for regular antivirus monitoring on a system, as the English language version would be difficult to use for the average system operator in China," researchers said.
Tick APT seen abusing at least one antivirus zero-day
The Insikt Group's discovery comes after Japanese media reported, citing law enforcement sources, that PLA Unit 61419 is behind a cyber-espionage group known as Tick, a group that was spotted abusing a Trend Micro antivirus zero-day in attacks against Japanese company Mitsubishi Electric throughout 2019.
While initially, Insikt Group researchers cited caution to attributing the Tick activity to Unit 61419, primarily due to China's military restructuring that began in 2015, the procurement orders suggest that the initial attribution to PLA unit 61419 might not be that far off its mark.
"These procurement orders are of tactical and strategic intelligence value to cyber defense teams," Charity Wright, Cyber Threat Intelligence Expert on China at Recorded Future, told The Record today.
"We are showing the pattern of Chinese APT behavior (software supply chain attacks) paired with these orders for foreign, English-version AV products because the likelihood of them using these purchases for malign purposes is high."
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



