Chinese hackers targeted at least 17 countries across Asia, Europe and North America
Hackers affiliated with China’s Ministry of State Security targeted a range of government, telecommunications and research organizations across at least 17 countries since 2021, according to a new report.
Researchers from Recorded Future’s Insikt Group have spent months tracking RedHotel — a state-sponsored hacking group using a range of malware in espionage campaigns against countries across Southeast Asia and other regions. The Record is an editorially-independent unit of Recorded Future.
The group is tracked by Microsoft as Charcoal Typhoon and BRONZE UNIVERSITY by SecureWorks.
Jon Condra, director of strategic and persistent threats at Recorded Future and one of the authors of the report, said RedHotel “is one of the most active [and] prolific Chinese state-sponsored groups that we track and they target organizations globally across a wide range of industry verticals.”
“They compromised a U.S. state legislature in 2022 and more widely have conducted intelligence gathering in tandem with economic espionage (e.g. targeting of technology R&D and historically COVID-19 research),” he said. “We are assessing they are likely based in Chengdu and operate in a similar manner to other groups known to be affiliated with China’s Ministry of State Security.”
While the group poses a specific threat to governments within the Southeast Asia region, RedHotel has been seen targeting other sectors including academia, aerospace, media, telecommunications, and research and development.
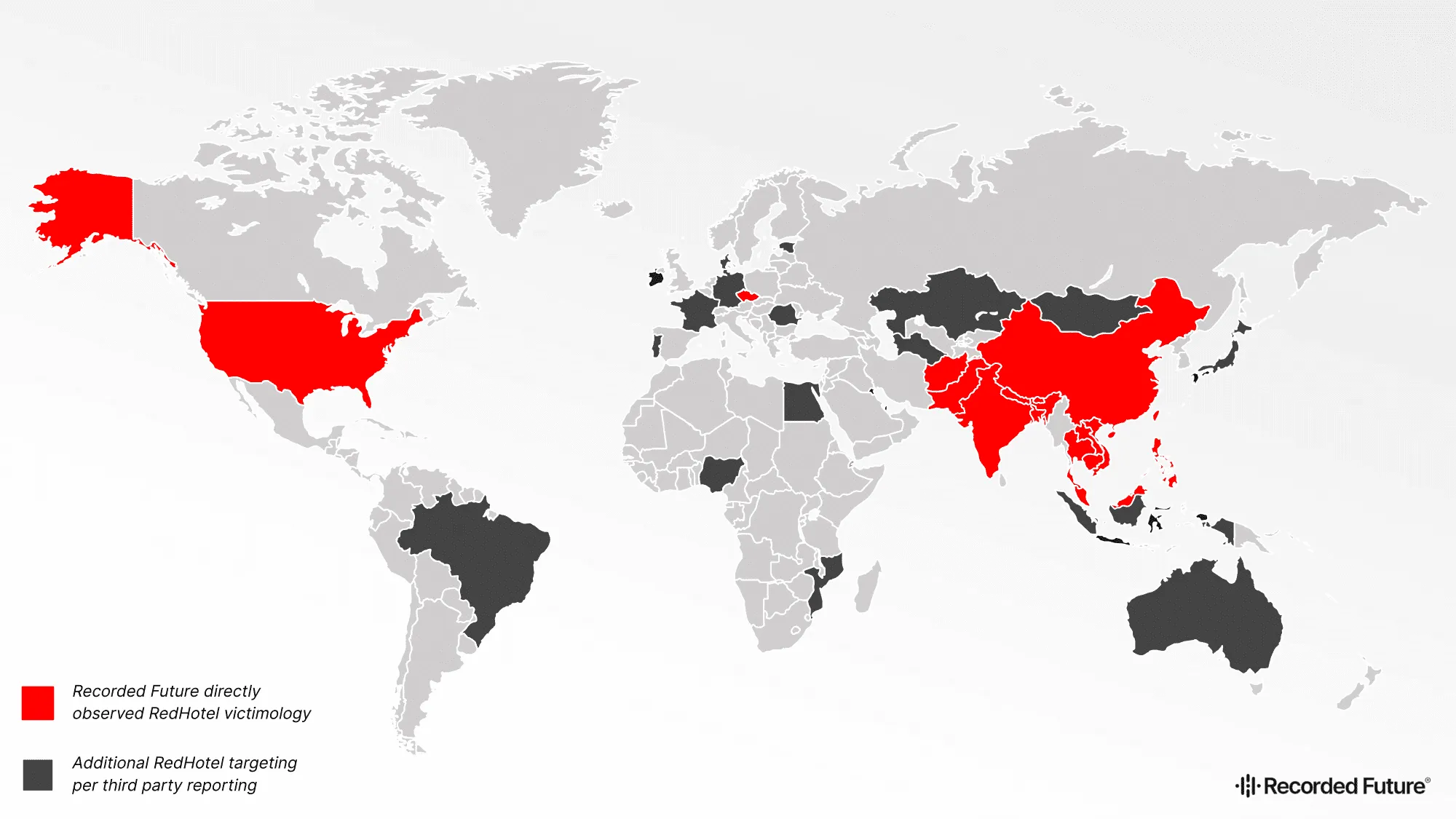
Image: Recorded Future
The group is using a sophisticated network of malware strains and other tools alongside other Chinese advanced persistent threat (APT) groups like APT41. The report notes that Chengdu has become a hub for Chinese APT activity, and several contractors allegedly have ties to local universities.
The group’s main goals are intelligence gathering and economic espionage, according to the researchers, who noted that several other companies have analyzed their attacks since 2019.
In addition to the targeting of a U.S. state legislature, the group previously went after COVID-19 research and technology organizations.
The malware used in attacks include variants commonly used by Chinese hackers, like ShadowPad and Winnti, as well as more “bespoke” malware families like Spyder and FunnySwitch.
“As a ShadowPad and Winnti user — both of which are custom malware families privately shared across a wide range of Chinese state-sponsored actors — RedHotel has occasionally blended in with the noise and created challenges in clustering and attribution,” the researchers said.
“However, the group’s high operational tempo, distinct infrastructure [tactics, techniques and protocols], and wider use of both custom and offensive security tooling has led us to graduate the previously temporary group designator TAG-22 to RedHotel based on both our ongoing technical tracking of the group and our assessment that RedHotel very likely operates in support of Chinese government intelligence-gathering efforts.”
The researchers said they have observed victims of the group in Afghanistan, Bangladesh, Cambodia, Czechia, Bhutan, Hong Kong, India, Laos, Malaysia, Nepal, Palestine, Pakistan, the Philippines, Thailand, Taiwan, the U.S., and Vietnam.
Most of the victims in each country were targets within local governments, including prime ministers’ offices, finance ministries, legislative bodies, and interior ministries.
The group is also accused of targeting research institutes in Taiwan, pro-democracy groups in Hong Kong, religious minority groups, and online gambling companies.
The report notes that a 2022 annual report from researchers at PWC said RedHotel is “the most prominent and prolific China-based threat actor in 2022.”
RedHotel has a two-pronged strategy, often using attacks to gain initial access before establishing long-term persistence in a victim’s system. From 2019 to 2023, the group used attack tools that masqueraded as the Microsoft Windows Compatibility Troubleshooter service.
Insikt Group researchers said that throughout 2022 and 2023, they tracked more than 100 IP addresses connected to RedHotel. The group has been seen using domains “for months or even years after public reporting.”
The group also uses previously compromised infrastructure in subsequent attacks. As an example, the researchers discovered an attack on a Taiwanese company that used compromised infrastructure belonging to the Vietnamese Institute on State Organizational Sciences.
They saw another attack using infrastructure tied to the Vietnamese Ministry of Education and Training, something the group is still using as of June 2023.
China’s prolific hacking operations have caused global headlines in recent weeks with several stories intimating an escalation in activities by hacking groups within the country’s military.
U.S. officials told The New York Times of potentially destructive Chinese malware discovered on critical infrastructure connected to U.S. military bases and on Monday, the Washington Post reported of widespread access obtained by China within the highest levels of the Japanese government.
“Since at least 2019, RedHotel has exemplified this relentless scope and scale of wider PRC state-sponsored cyber-espionage activity through maintaining a high operational tempo and targeting public and private sector organizations globally,” the researchers said, noting that the use of Vietnamese government infrastructure “showed RedHotel’s willingness to innovate and add additional tooling beyond its well-established toolset.”
“Based on historical precedent, we expect RedHotel to continue this activity unperturbed, with the group regularly displaying a high operational risk appetite in the face of public industry reporting.”
Correction: An earlier version of this story mischaracterized China's Ministry of State Security. It is a civilian intelligence agency.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



