Chinese cyberspies targeted the Afghan National Security Council
A Chinese cyber-espionage group has been seen impersonating the office of the Afghan president in attempts to infect members of the Afghanistan National Security Council with malware.
The attacks, which took the form of a cleverly crafted spear-phishing operation, have been spotted and documented in a report published today by cybersecurity firm Check Point.
The company said that based on the malware used in the attacks, they were able to link the espionage attempt to a Chinese advanced persistent threat (APT) group named IndigoZebra, first spotted in 2017 and known to have been operating since at least 2014.
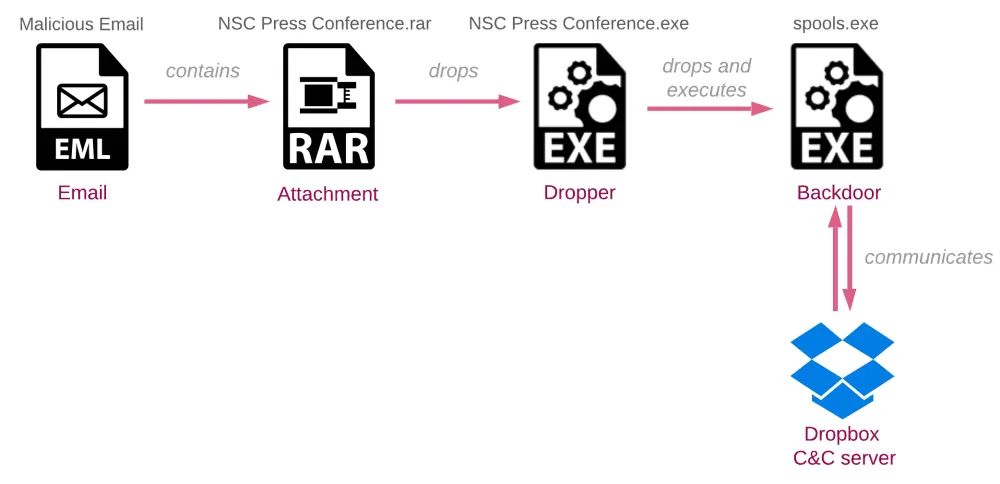
For example, Check Point researchers discovered that the malware deployed in these attacks, codenamed BoxCaon, appeared to be a variant of the xCaon backdoor that IndigoZebra deployed in previous campaigns.
Researchers named this version BoxCaon because the malware was configured to take commands and exfiltrate data via an attacker-controlled Dropbox account, a technology the group chose in order to blend its attacks with regular Dropbox traffic and remain undetected as long as possible.
In addition, Check Point said it also found evidence that the group had targeted other governments in Central Asia, including those of Kyrgyzstan and Uzbekistan, two countries neighboring Afghanistan.
"What is remarkable here is how the threat actors utilized the tactic of ministry-to-ministry deception," Lotem Finkelstein, Head of Threat Intelligence at Check Point Software, told The Record this week.
"This tactic is vicious and effective in making anyone do anything for you; and in this case, the malicious activity was seen at the highest levels of sovereignty."
"It's possible that other countries have also been targeted by this hacker group, though we don't know how many or which countries. Hence, we're sharing a list of other possible domains used in the attack at this time, in hope that their names can be leveraged by other cyber researchers for contribution to our own findings," Finkelstein added.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



