Chinese cyber spies targeted Israel posing as Iranian hackers
A Chinese cyber-espionage group has targeted Israeli organizations in a campaign that began in January 2019, and during which the group often used false flags in attempts to disguise as an Iranian threat actor.
Detailed in a report published today by security firm Mandiant, the attacks targeted Israeli government institutions, IT companies, and telecommunication providers.
The attackers, which Mandiant said it was tracking under a codename of UNC215, typically breached organizations by targeting Microsoft SharePoint servers unpatched for the CVE-2019-0604 vulnerability.
Once UNC215 gained access to one of these servers, they deployed the WHEATSCAN tool to scan the victim's internal network and then installed the FOCUSFJORD web shell and HYPERBRO backdoor on key servers as a way to ensure persistence on the hacked organizations' networks.
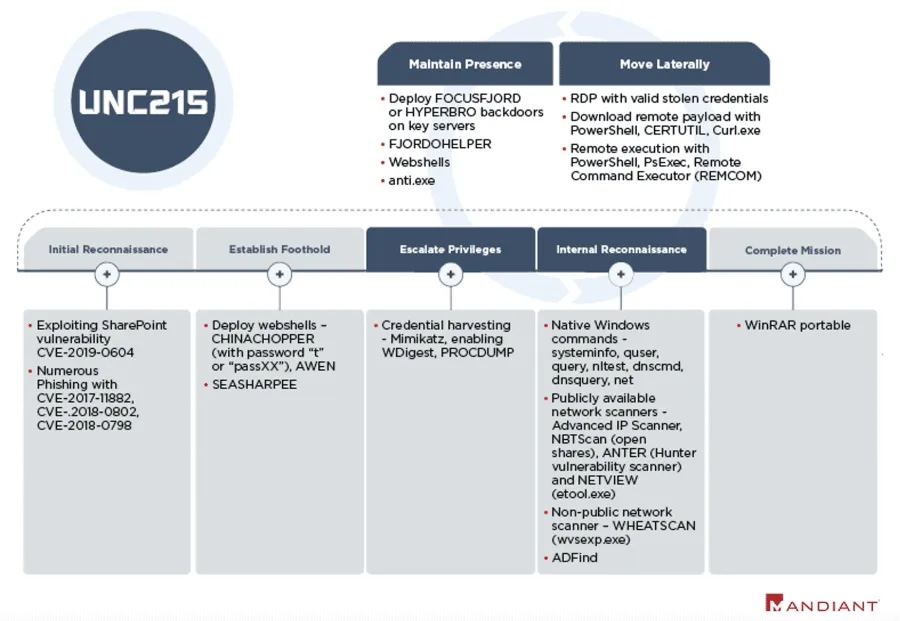
Mandiant said the group took great care and several steps to hide their intrusions and minimize forensic evidence on a victim's network, such as removing malware artifacts once they were not needed and using legitimate software to perform malicious operations.
UNC215 planted Iranian false flags
Furthermore, the group also used false flags inside their malware source code in an attempt to hide their real identities.
Mandiant said UNC215 often used file paths mentioning Iran (i.e., C:\Users\Iran) or error messages written in Arabic (i.e., 'ضائع' – which translates to: lost or missing)
In addition, on at least three occasions, UNC215 also used an Iranian hacking tool that was leaked on Telegram in 2019 (i.e., the SEASHARPEE web shell).
However, Mandiant researchers said that despite these indicators, the UNC215 group has been conducting cyber-espionage operations of interest to the Chinese state since at least 2014.
Moreover, the attacks against Israeli targets are part of a larger espionage campaign during which UNC215 targeted a broader set of victims across the Middle East, Europe, Asia, and North America, with targets typically in the government, technology, telecommunications, defense, finance, entertainment, and health care sectors.
But while the Mandiant research team attributed these hacks to the UNC2015 group, the company said it's currently investigating the possibility that UNC2015 might be associated with a larger Chinese cyber-espionage group known as APT27 or Emissary Panda, a group which security firm Cybereason also recently spotted attacking telcos across Southeast Asia.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



