China’s Salt Typhoon hackers targeting Cisco devices used by telcos, universities
China’s Salt Typhoon campaign to breach telecommunications companies has continued through the new year despite efforts by governments to stop the hackers, researchers said Thursday.
Recorded Future’s Insikt Group identified a campaign in December and January that involved attempts to compromise more than 1,000 Cisco network devices globally, many of which are associated with telecommunications providers. The Record is an editorially independent unit of Recorded Future.
Among the targeted organizations was a South African telecom, as well as a U.S.-based affiliate of a UK telecommunications company.
“The group likely compiled a list of target devices based on their association with telecommunications providers' networks,” the researchers said.
Insikt Group observed seven total compromised Cisco network devices communicating with Salt Typhoon infrastructure — including those connected to telecommunications companies in the U.S. and South Africa, as well as others in Italy and Thailand.
Researchers also saw the group carry out reconnaissance activity in December on IP addresses owned by the Myanmar-based provider Mytel.
More than half of the Cisco devices targeted by Salt Typhoon were in the U.S., South America, and India. The remaining devices spanned more than 100 other countries.
They also observed the hackers targeting devices connected to universities in Argentina, Bangladesh, Indonesia, Malaysia, Mexico, the Netherlands, Thailand, the U.S. and Vietnam.
The researchers theorized that the hackers attacked universities to access research in areas related to telecommunications, engineering and technology.
U.S. officials have for months raised alarms about Salt Typhoon, which they say has breached at least nine U.S. telecommunications giants including Verizon, T-Mobile, AT&T and Lumen.
As in other Chinese government hacking campaigns, Salt Typhoon has made a point of targeting unpatched network devices like those from Cisco to gain initial access to critical systems.
The hackers allegedly used their deep access to telecom networks to obtain call information from several high-profile political figures, including Donald Trump, the Republican presidential nominee at the time, and his running mate JD Vance, as well as senior Democratic Party leaders and members of then-Vice President Kamala Harris’ staff.
Points of entry
The hackers targeted unpatched Cisco devices vulnerable to the bugs CVE-2023-20198 and CVE-2023-20273. The first bug was the method of entry while the second allowed for escalated privileges in a victim’s system. The hackers have been reconfiguring the exploited devices and creating a link to them that allows for persistent access.
Insikt Group saw the hackers scanning for exploitable devices on six distinct occasions throughout December and January, including on December 4, 10, 17 and 24. In January, the hackers scanned for unpatched devices on the 13th and 23rd.
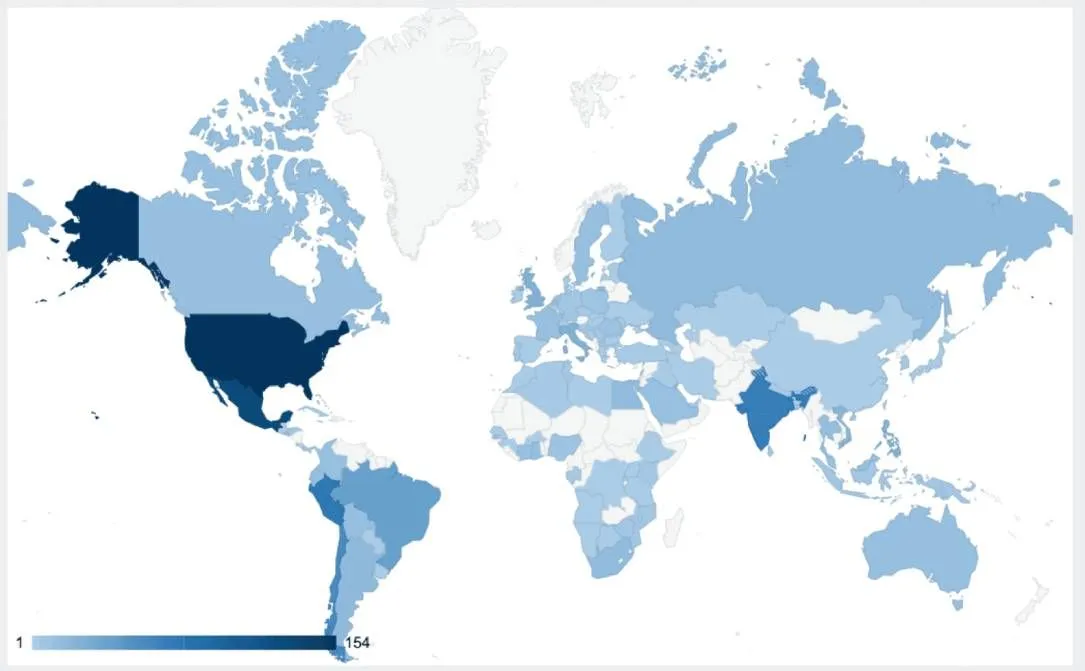
The geographical spread of Cisco devices targeted by Salt Typhoon. Credit: Recorded Future
The researchers urged any administrators using these specific Cisco network devices to check for potential exploitation on those dates. Using its own scanning tools, Insikt Group found more than 12,000 Cisco network devices exposed to the internet — leading them to believe the Salt Typhoon activity was targeted given that only a portion of the devices were attacked.
The FBI and Department of Homeland Security did not respond to requests for comment about the activity. The Justice Department said it had nothing further to add.
In January, the Treasury Department announced sanctions against a Chinese contractor allegedly involved in the Salt Typhoon campaign.
The Treasury Department said Salt Typhoon has compromised “numerous” U.S. companies in the communication sector since 2019 but the most recent campaign against multiple major U.S. telecommunication and internet service provider companies marks “a dramatic escalation in the Chinese cyber operations against U.S. critical infrastructure targets.”
In its report on Thursday, Insikt Group said Chinese threat activity has shifted heavily toward exploiting Cisco devices for initial access over the past five years.
“[Salt Typhoon] exploitation of telecommunications infrastructure goes beyond technical vulnerabilities and represents a strategic intelligence threat,” they said. “Persistent access to critical communications networks enables state-backed threat actors to monitor confidential conversations, manipulate data flows, and disrupt services during geopolitical conflicts.”
READ MORE: Munich Cyber Security Conference 2025 Live Updates
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



