China-linked APT group targets Russian nuclear sub designer with an undocumented backdoor
A threat actor believed to be operating on behalf of Chinese state-sponsored interests was recently observed targeting a Russian defense contractor involved in designing nuclear submarines for the Russian Navy, according to new research published today by Cybereason.
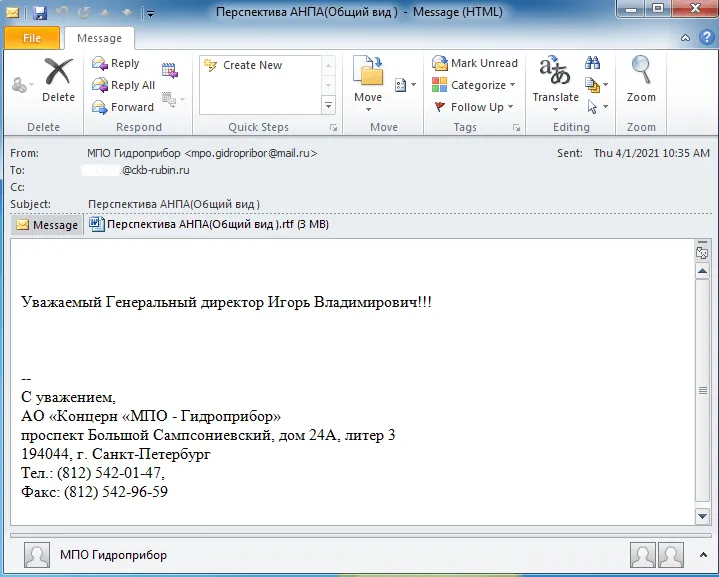
The attack was narrowly-focused, the firm said, and originated with a spear-phishing attempt targeting a general director working at the Rubin Design Bureau, a Saint Petersburg-based shipbuilder that has designed most of Russia’s nuclear submarines. The email attachment included a malicious Rich Text File (RTF) document that included descriptions of an autonomous underwater vehicle.
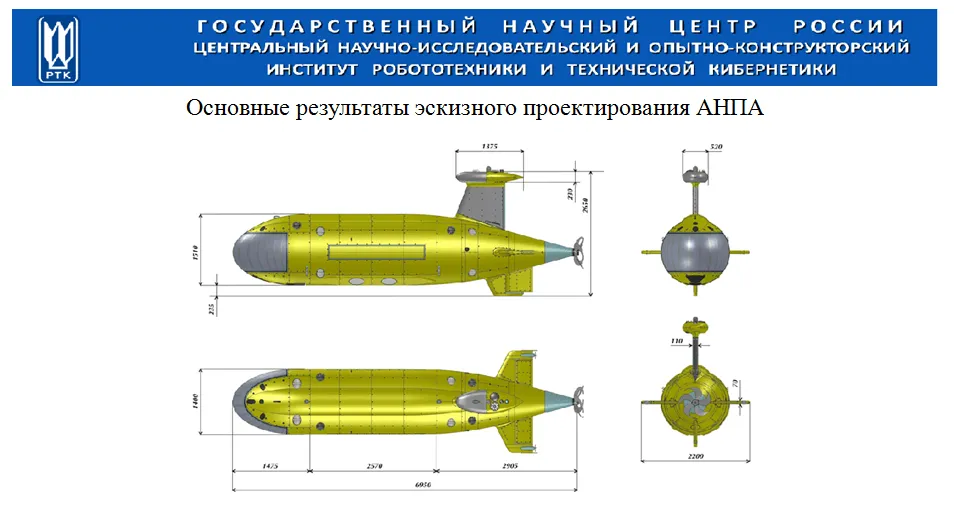
The email attachment was weaponized with a RoyalRoad payload, which has been used by several China-linked threat actors including Tick, Tonto Team, Goblin Panda, Rancor, and TA428. The tool generates weaponized RTF documents that exploit the following vulnerabilities in Microsoft’s Equation Editor: CVE-2017-11882, CVE-2018-0798 and CVE-2018-0802.
Interestingly, the attack group’s RoyalRoad sample exhibited anomalous characteristics and delivered what the company is calling “PortDoor” malware, a previously undocumented backdoor “designed with obfuscation and persistence in mind,” Cybereason said. The malware has multiple functionalities, including reconnaissance, target profiling, delivery of additional payloads, privilege escalation, static detection antivirus evasion, one-byte XOR encryption, AES-encrypted data exfiltration, and more.
Although Cybereason wasn’t able to definitively attribute the attack to a known threat group, it said it shares similarities with a few Chinese APT groups.
Previous research from nao_sec suggests that the malicious RTF document was created with RoyalRoad v7 with a header encoding that was previously observed being used by Tonto Team, TA428, and Rancor.
Two of those groups—Tonto Team and TA428—have been linked to attacks targeting Russian research and defense organizations. Additionally, the spear-phishing emails and lure documents used by those groups exhibit “certain similarities in the linguistic and visual style used by the attackers,” Cybereason said, calling the groups “potential suspects that fit the profile.”
Rubin Design Bureau did not respond to a request for comment.
Adam Janofsky
is the founding editor-in-chief of The Record from Recorded Future News. He previously was the cybersecurity and privacy reporter for Protocol, and prior to that covered cybersecurity, AI, and other emerging technology for The Wall Street Journal.



