Babuk gang says it will stop ransomware attacks after DC Police incident
The operators of the Babuk Locker ransomware have announced plans to stop carrying out ransomware intrusions and focus on data theft and extortion instead.
The announcement comes days after the Babuk Locker gang tried to extort the DC Police Department in one of the most brazen extortion attempts in recent years.
The move also comes after the Babuk gang flip-flopped on Thursday, giving an interview to a Polish news site, and then fleetingly posting a message on their dark web portal announcing plans to shut down and open-source their ransomware code.
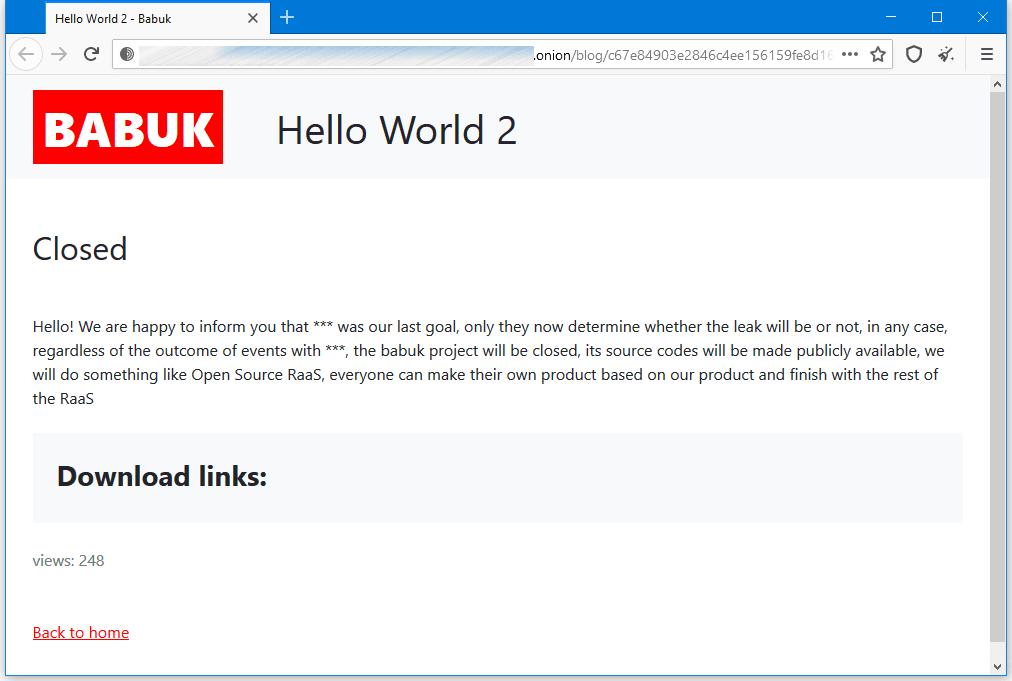
But while the original post was only live for two hours, today, the group posted a new announcement, but with a total different message. Instead of shutting down their operation, the group now says it will just stop orchestrating ransomware attacks.
Babuk operators said they plan to continue breaching companies but instead of stealing sensitive files and encrypting local data, the group plans only to steal it. If companies don't want to pay to have their data returned, the group says it will list it on their site, just like it did until now, exposing the victim's sensitive documents.
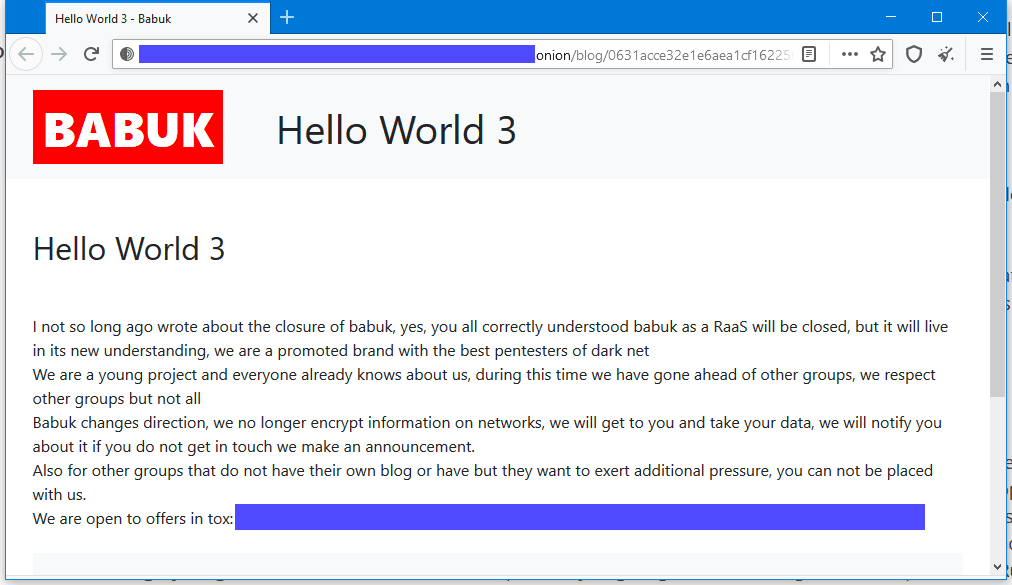
Furthermore, the group has also offered to list other group's files on their site, if they lack a "data leak" portal, a tactic also used by the Maze ransomware gang last year.
However, several security researchers have pointed out on Twitter this week that the group made a very big operational mistake when it aggressively tried to extort one of the biggest police departments in the US, its officers, and by putting the lives of its informant sources at risk.
The gang might now be looking for an exit strategy following their attack on DC Police, which they are now most likely regretting. However, shutting down their ransomware platform and switching to an extortion cartel won't stop any existing FBI investigation.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



