AT&T takes action against DDoS botnet that hijacked VoIP servers
AT&T said it's investigating and has "taken steps to mitigate" a botnet that infected more than 5,700 VoIP servers located inside its network, a spokesperson has told The Record earlier today.
All the infected devices were EdgeMarc Enterprise Session Border Controllers, a type of Voice-over-IP server designed to balance and reroute internet telephony traffic from smaller enterprise customers to upstream mobile providers.
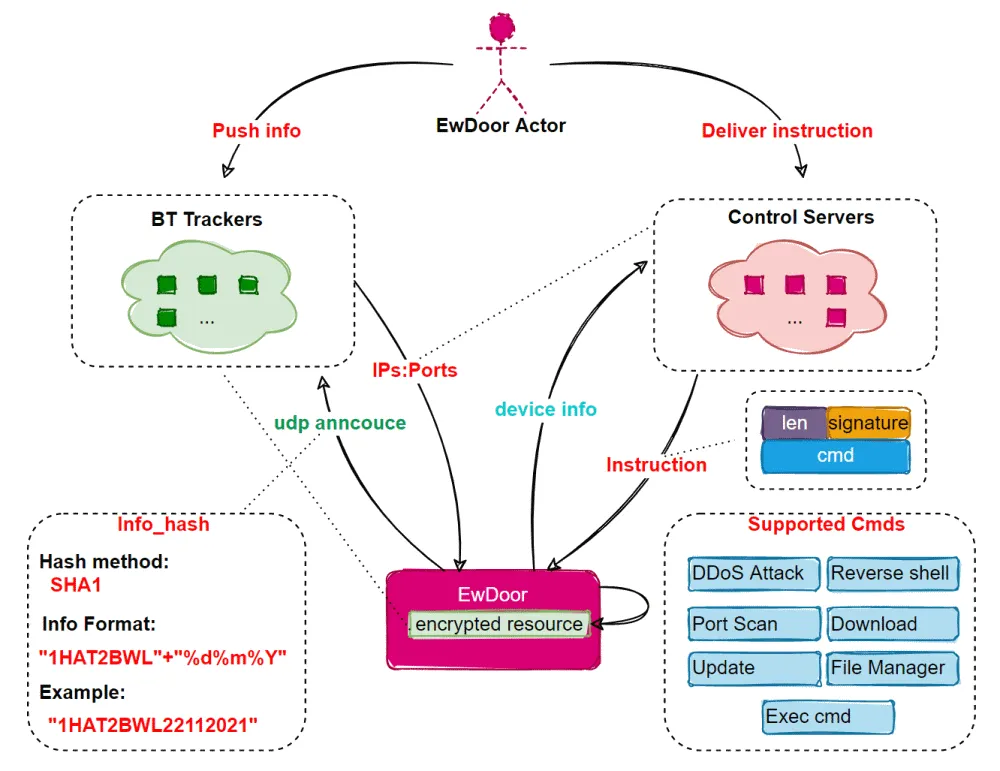
According to Netlab, a network security division of Chinese tech giant Qihoo 360, a threat actor used an old exploit (CVE-2017-6079) to hack into unpatched EdgeMarc servers and install a modular malware strain named EwDoor.
"[W]e confirmed that the attacked devices were EdgeMarc Enterprise Session Border Controller, belonging to the telecom company AT&T, and that all 5.7k active victims that we saw [...] were all geographically located in the US."
Netlab EwDoor report
AT&T says it saw no evidence of data theft
The Chinese security firm said it's been tracking the EwDoor botnet and its attacks since late October 2021, during which time the malware went through at least three versions.
An analysis of the malware revealed extensive backdoor and DDoS capabilities, which Netlab researchers suggested could be used to access devices to gather and steal sensitive information, such as VoIP call logs.
But AT&T says it has not seen any evidence to sustain Netlab's assessment.
"We have no evidence that customer data was accessed," the company said in an email earlier today.
Netlab said that the 5,700 estimate it provided today was gathered following a brief window of visibility into the botnet's operations on November 8.
Internet-wide scans suggest that more than 100,000 devices are using the same SSL certificate used on EdgeMarc VoIP servers, but it's unclear how many of these are vulnerable to CVE-2017-6079 and exposed to attacks.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



