APT group targets diplomatic organizations in Africa and the Middle East
Security experts have discovered a new cyber-espionage (APT) group that has spent the past four years targeting diplomatic organizations across Africa and the Middle East.
The attacks have been traced back to at least 2017 and have been attributed to a group that security firm ESET has codenamed BackdoorDiplomacy.
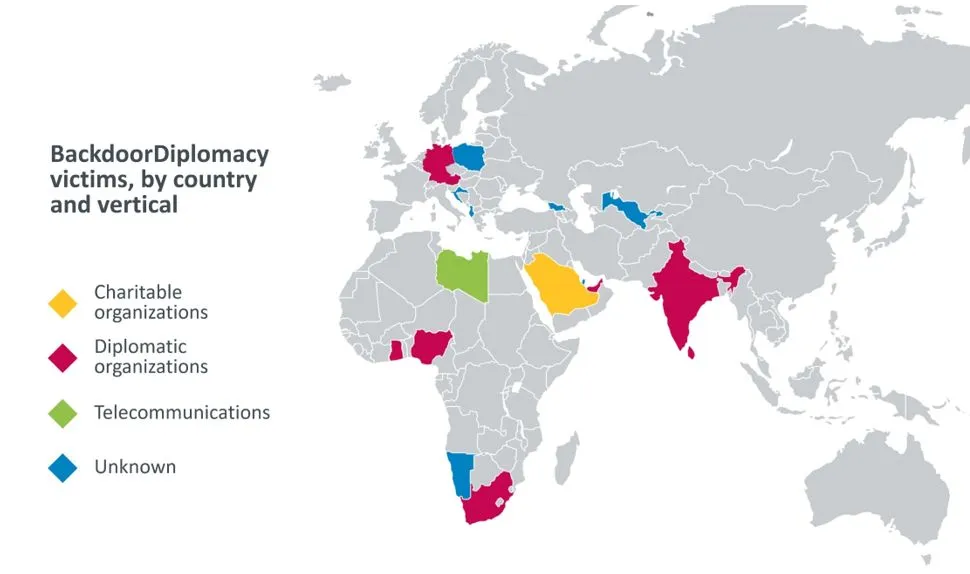
"Victims have been discovered in the Ministries of Foreign Affairs of several African countries, as well as in Europe, the Middle East, and Asia," Adam Burgher, a Senior Threat Intelligence Analyst at Slovak cybersecurity firm ESET, said in a report today.
"Additional targets include telecommunication companies in Africa, and at least one Middle Eastern charity," Burgher added.
The ESET researcher said the group primarily relied on exploiting vulnerabilities in internet-exposed devices such as web servers and management interfaces for networking equipment. Targeted systems included F5 BIG-IP devices, Microsoft Exchange email servers, and Plesk web hosting management panels.
Burgher said that once hackers breached a target's system, they usually downloaded and used open-source scanning tools to move laterally across a network before deploying a custom-built malware strain ESET codenamed Turian.
The trojan, which came in both Windows and Linux versions, acted as a backdoor and allowed the hackers to interact with sensitive targets, search their systems, and exfiltrate data.
On some networks, ESET said it also observed BackdoorDiplomacy operators also deploy a malware strain that infected removable media devices, such as USB drives, in attempts to spread to air-gapped networks.
Multiple links to other Chinese APTs
ESET did not formally link this new APT to a specific country but only described the group as sharing "commonalities with several other Asian groups."
However, the links the company drew connect BackdoorDiplomacy to multiple Chinese-based threat actors, suggesting the group might be one as well.
These links included:
- Several victims were compromised via mechanisms that closely matched the Rehashed Rat and a MirageFox-APT15 campaign documented by Fortinet in 2017 and Intezer in 2018, respectively.
- The Turian backdoor was based on Quarian, a malware strain linked to a Chinese hacking operation against the US State Department.
- Similarities to a Chinese hacking operation tracked as CloudComputating by Kaspersky.
- Turian's network encryption protocol is nearly identical to the network encryption protocol used by Whitebird, a backdoor operated by Calypso, another Asian group.
The Backdoor Diplomacy report comes after a similar finding from Russian security firm Kaspersky, which found another Chinese-suspected APT group targeting African diplomatic organizations last month.
In a January 2021 report, the Africa Center for Strategic Studies said the greatest concerns surrounding cyber espionage in Africa have been linked to China.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



