APT group targeting military in India, Pakistan through malicious Android messaging apps
A group of suspected government-backed hackers is targeting Indian and Pakistani citizens through malicious Android messaging apps in a campaign designed to steal sensitive information.
Researchers from cybersecurity firm ESET said the attacks – run by an APT group they call “Transparent Tribe” – involved purportedly secure messaging and calling apps that contained a backdoor called CapraRAT.
The backdoor allowed the hackers to exfiltrate sensitive information from victim devices. The campaign, which began last July and is still active, targeted people with a military or political background.
The hackers used “honey-trap baits” to lure their targets into downloading the apps, which were called MeetsApp and MeetUp.
“Finding a mobile number or an email address they can use to make first contact is usually not difficult,” explained ESET researcher Lukáš Štefanko, who discovered the campaign while analyzing a different malware sample posted on Twitter.
ESET researchers believe victims were initially directed to the websites through romance scams in which targets were urged to move to allegedly more secure platforms that the hackers controlled.
The backdoor in the apps can record phone calls and surrounding audio, take screenshots and photos, and receive commands to download files, make calls, and send SMS messages.
The campaign appears to be highly targeted, with neither app available on Google Play.
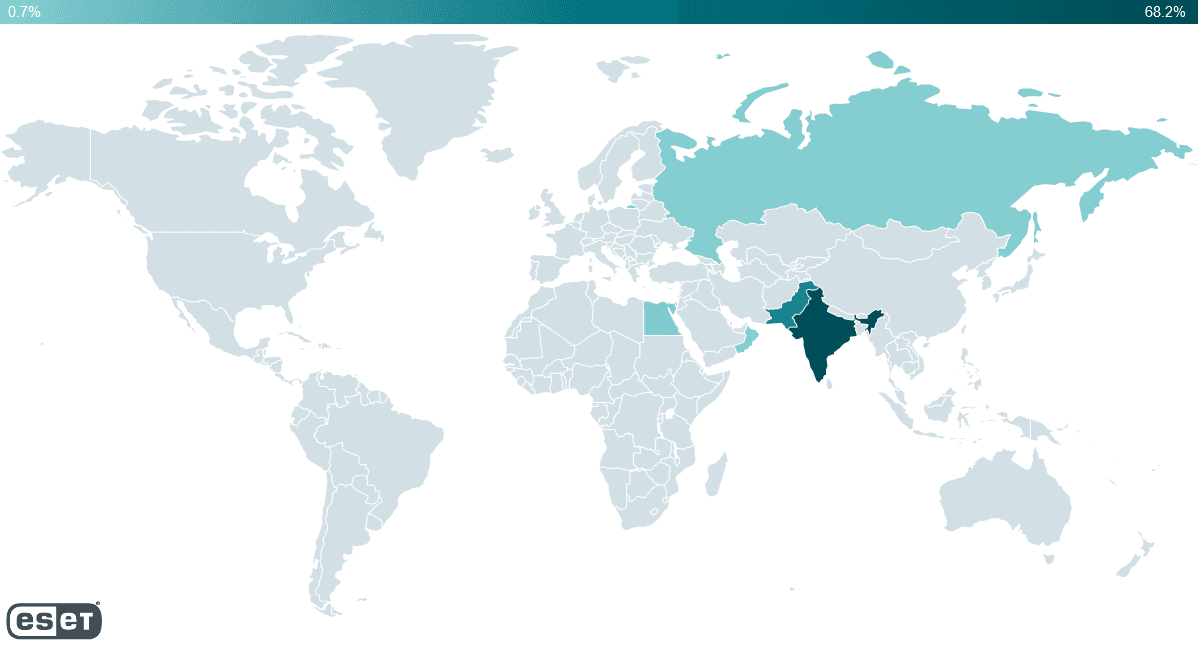
ESET researchers were able to take advantage of the apps’ poor security and found the personal information of 150 of the victims – with most from India and Pakistan but several from Russia, Oman, and Egypt.
Cybersecurity experts from MITRE said Transparent Tribe, also known as APT36, is suspected of being based in Pakistan and has been active since at least 2013. They primarily target “diplomatic, defense, and research organizations in India and Afghanistan.”
IP addresses used by the hackers in this latest campaign tie the apps and their websites to Transparent Tribe, researchers said. Both domains were registered in July 2022.
According to ESET, the group began targeting Android users in 2021 using several different strains of malware.
“Both apps are based on the same legitimate code trojanized with CapraRAT backdoor code. Messaging functionality seems either to be developed by the threat actor or found (maybe purchased) online, since we couldn’t identify its origin,” Eset said.
The Record has previously reported on two separate campaigns alleged to be connected to Transparent Tribe. In July 2021, a cyber-espionage group was observed targeting Indian citizens with government and military-related lures in a broad campaign to infect victims with malware.
While that campaign was attributed to a group named “SideCopy,” researchers said many of its operations bore a close resemblance to past campaigns carried out by APT36 or Transparent Tribe.
In another 2021 campaign attributed to the same group, threat actors created and operated a fake Android app store in order to target and infect individuals connected to the former Afghanistan government prior to and during its fall to the new Taliban regime.
Facebook security researchers said the hackers created fake profiles on its platform, typically posing as young women, and approached targets with the goal of getting them to click on malicious links. These links redirected victims to phishing sites that collected login credentials or, in some cases, to fake app stores hosting malware-infected Android apps.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



