Apple fixes macOS zero-day abused by XCSSET malware
Apple has released today security updates for several of its products, including a patch for its macOS desktop operating system that includes a fix for a zero-day vulnerability that has been abused in the wild for almost a year by the XCSSET malware gang.
Tracked as CVE-2021-30713, the zero-day was discovered by researchers at security firm Jamf during an analysis of XCSSET, a malware strain that was spotted in the wild in August 2020, hidden inside malicious Xcode projects hosted on GitHub.
"Upon initial discovery, one of the most notable features of the XCSSET malware was that it reportedly utilized two zero-day exploits," Jamf said in a blog post today.
"[The] first was used to steal the Safari browser cookies [...]; while the second was used to bypass prompts in order to install a developer version of the Safari application."
Third XCSSET zero-day was used to bypass macOS TCC
But Jamf researchers said they found a third zero-day in the XCSSET malware source code during an analysis of this older threat, which has been recently updated to attack M1-based macOS systems.
Packed as an AppleScript, this zero-day allowed the malware to bypass Transparency Consent and Control, which is the macOS service that shows permissions popups every time an app wants to perform an intrusive action, such as using the camera, the microphone, or recording the user's screen and key presses.
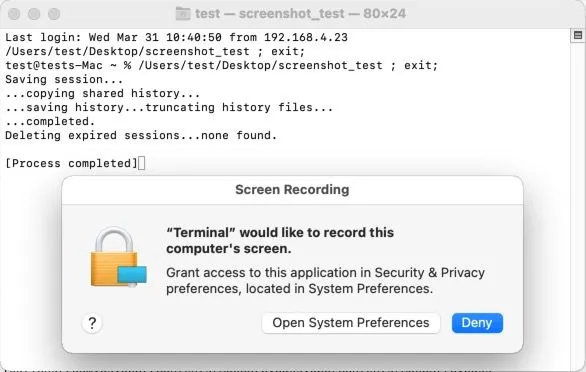
According to the Jamf crew, the XCSSET malware gang abused CVE-2021-30713 in order to search macOS for the IDs of other apps that received a dangerous permission and would later plant a malicious applet inside one of these legitimate apps to perform malicious actions, such as taking a screenshot of the victim's desktop.
Following Jamf's report, Apple has patched TCC today in a security update for macOS Big Sur 11.4.
Apple users still running older versions of macOS are vulnerable to attacks and are advised to update their systems.
While the XCSSET malware and its distribution campaign is generally a very niche attack targeted mainly at developers, there is also the danger that other malware gangs will utilize the information shared by Jamf today to update their code and abuse CVE-2021-30713 for their attacks as well—hence why macOS users are advised to update to the latest macOS Big Sur 11.4.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



