Anonymous hacks and leaks data from domain registrar Epik
Hacktivist group Anonymous has successfully breached and leaked the database of Epik, a controversial web hosting provider and domain registrar that has given shelter to many right-wing websites over the past few years, such as Gab, Parler, and The Donald.
The hack, which based on timestamps in the leaked data took place on February 28, was announced on Monday via a dedicated website [archived] and posts on internet forum 4chan.
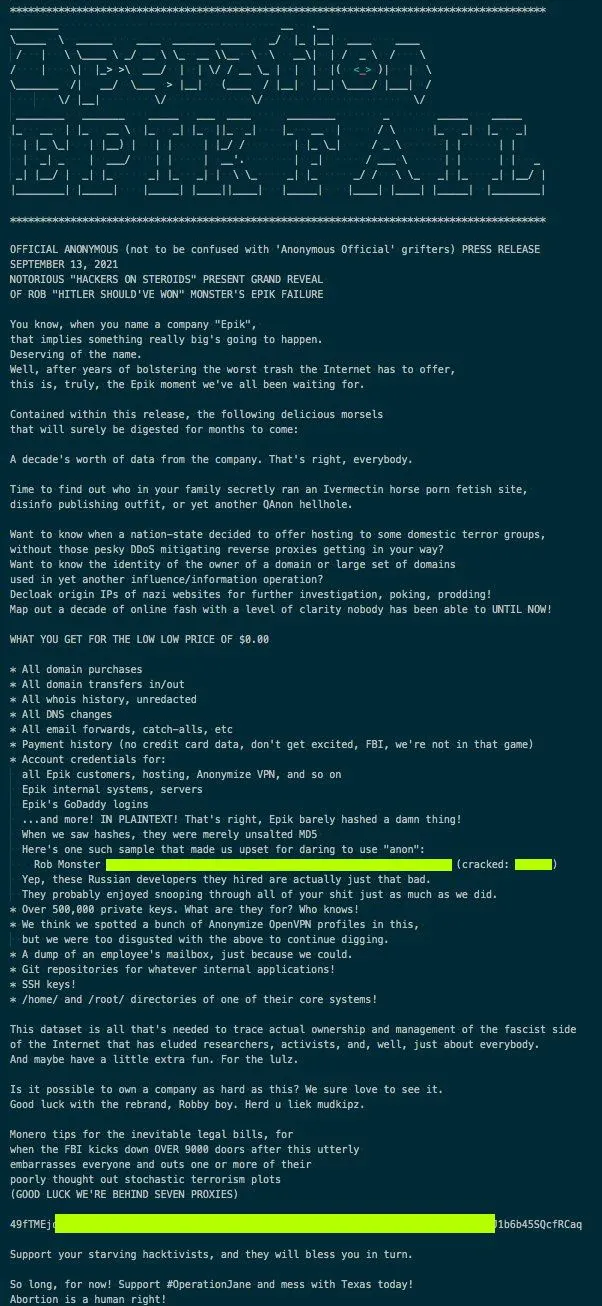
"A decade's worth of data from the company. That's right, everybody," the group touted on Monday on their site.
The Record, which was tipped of the breach on Monday, received a small subset of samples and then a full copy of the entire leak from an individual who claimed to be loosely associated with the Anonymous group.
Reached out for comment on Tuesday, Epik denied the breach and the hackers' claims in an email to The Record.
We are not aware of any breach. We take the security of our clients' data extremely seriously, and we are investigating the allegation.
Epik spokesperson
But the data The Record received in full and reviewed earlier today confirms the hackers' claims.
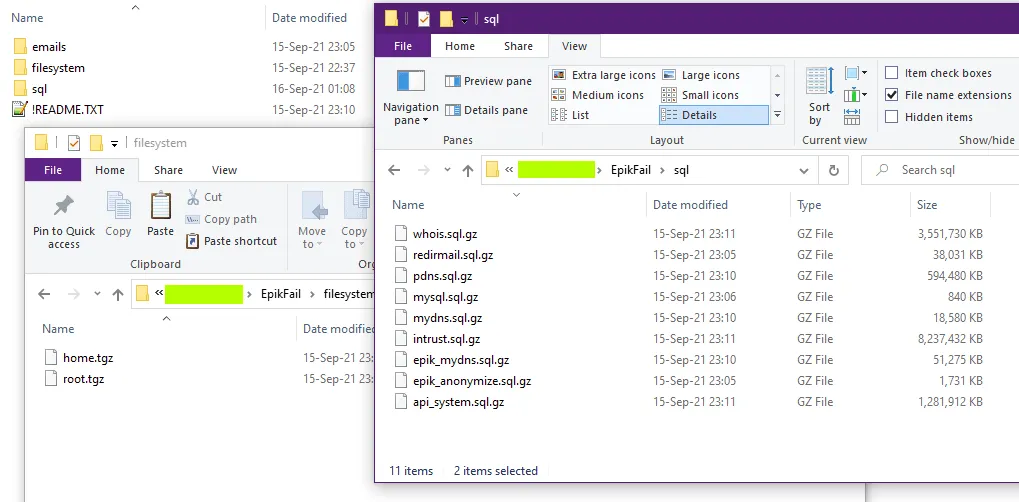
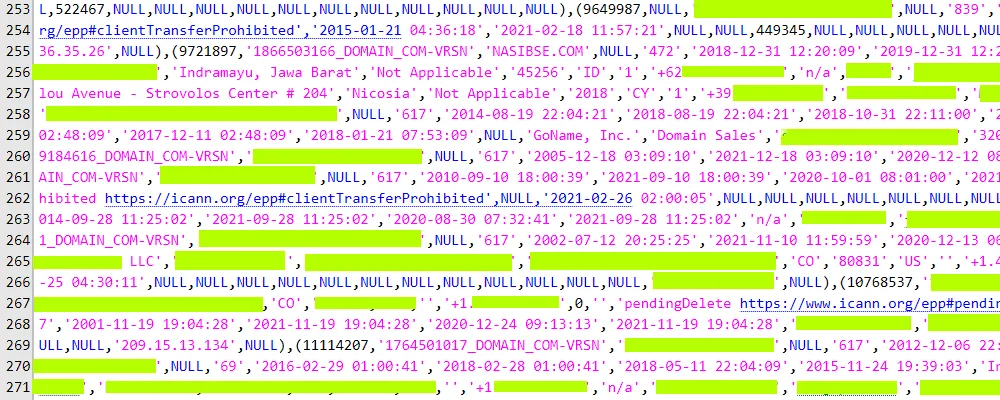
In a 32 GB torrent file hosted through the DDoSecrets portal, the hackers included several SQL database dumps containing gigabytes of sensitive information such as domain ownership details, domain transactions, account details, and troves of personal data points.
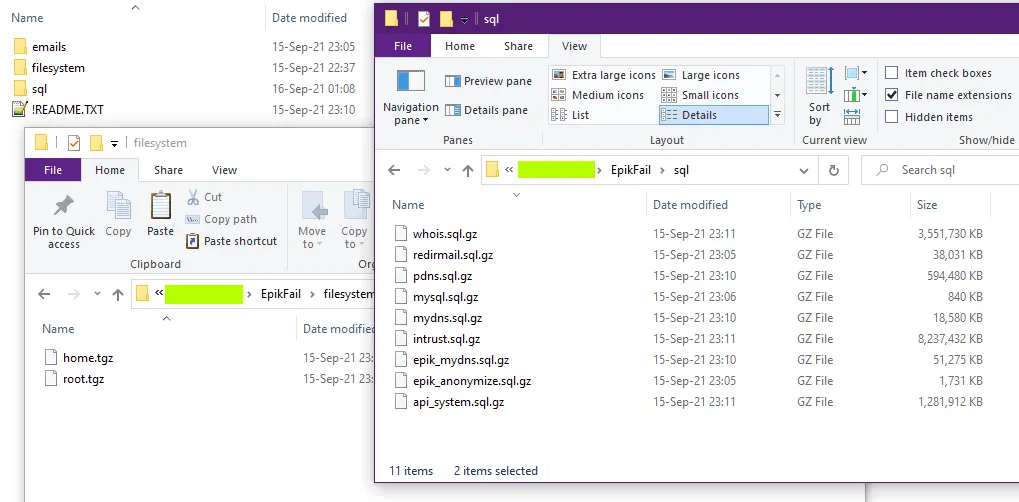
Most of the archived data contained what the hackers claimed, including SSH keys, source code, email inbox contents, and loads of private keys, which neither the hackers nor The Record were able to link to anything.
The Record also called and verified the accuracy of the leaked data with three randomly selected Epik customers whose data was included in the leak. All confirmed details such as real names, emails, and home addresses for domains that previously had their ownership details kept private.
A data trove for activists and security researchers
Anonymous claimed the leak contained the details of every domain that was ever hosted or registered through Epik, a claim that we are technically unable to confirm.
The hacktivist group suggested that the leak could be used for more than just shame Epik, a company the group has a bone to pick because of its support of alt-right and far-right entities.
The group's members encouraged reporters, activists, and security researchers to comb the leak for information on domains associated with nation-state hacking groups, influence operations, terrorist sites, and nazi sites.
Time to find out who in your family secretly ran an Ivermectin horse porn fetish site, disinfo publishing outfit, or yet another QAnon hellhole.
Want to know when a nation-state decided to offer hosting to some domestic terror groups, without those pesky DDoS mitigating reverse proxies getting in your way?
Want to know the identity of the owner of a domain or large set of domains used in yet another influence/information operation?
Decloak origin IPs of nazi websites for further investigation, poking, prodding!
Map out a decade of online fash with a level of clarity nobody has been able to UNTIL NOW!
#OperationJane
A copy of the Epik data is currently distributed via the DDoSecrets independent investigative journalism portal, a project that became famous for hosting BlueLeaks, a collection of 296 GB of internal US law enforcement data obtained and leaked by Anonymous in June 2020 following the Black Lives Matter protests.
This time around, the Epik leak, codenamed EpikFail, is part of the Anonymous group's #OperationJane, a hacktivism campaign aimed to protest the recently approved Texas Senate Bill 8, which severely restricts women's abortion rights.
Before the EpikFail leak, Anonymous previously defaced the website of the Texas GOP, the US political group that helped pass the state's restrictive abortion rights law.
Earlier today, the group also defaced a section of the Epik support portal [archived] after the company refused to acknowledge the breach.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.