Android users in Middle East, South Asia targeted with spyware posing as fake VPN apps
Android users in the Middle East and South Asia are being targeted by a government-linked group with spyware posing as VPN websites, according to a new report from ESET.
Researchers determined the campaign has been running since January, and attributed it to the notorious Bahamut advanced persistent threat (APT) group. The organization did not respond to requests for comment about which country the APT is believed to be affiliated with.
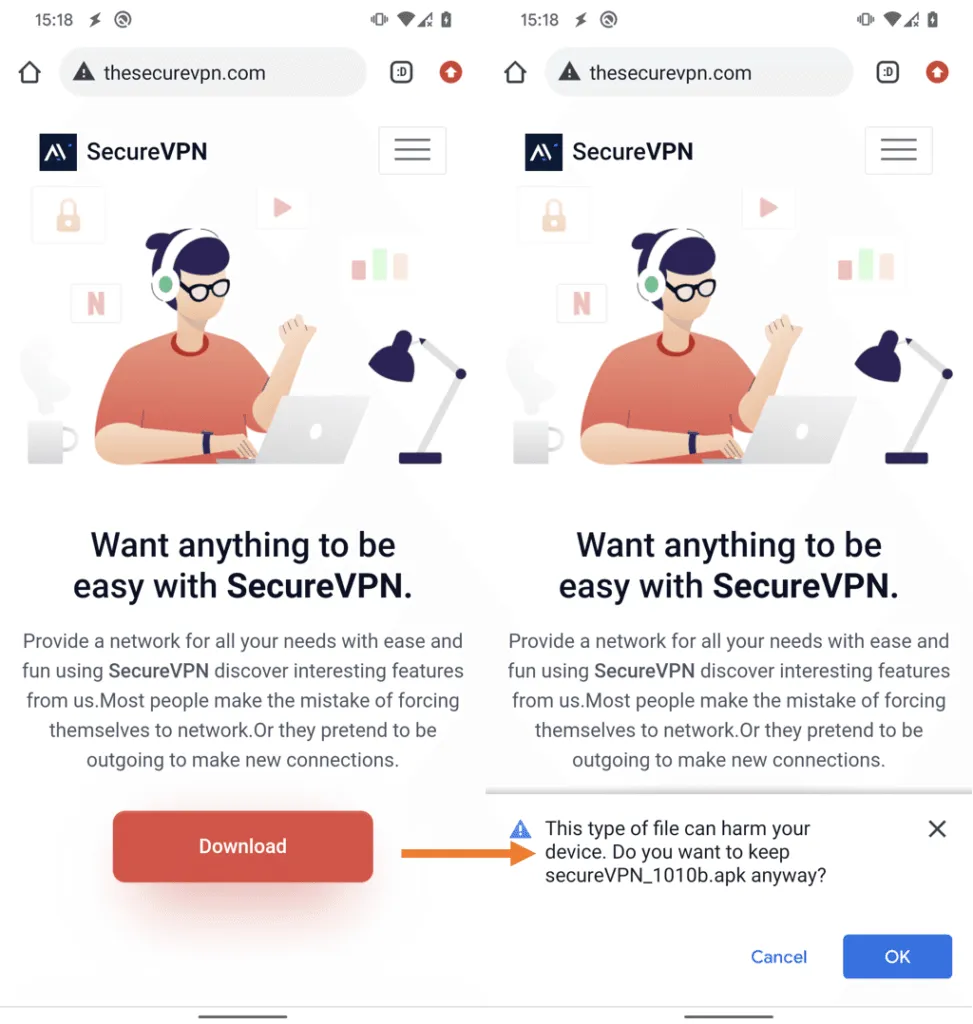
The spyware is being distributed through a fake SecureVPN website with apps for Android. The malware has no association with SecureVPN but is being distributed through two two legitimate VPN apps – SoftVPN or OpenVPN – that are being repackaged with the Bahamut spyware code.
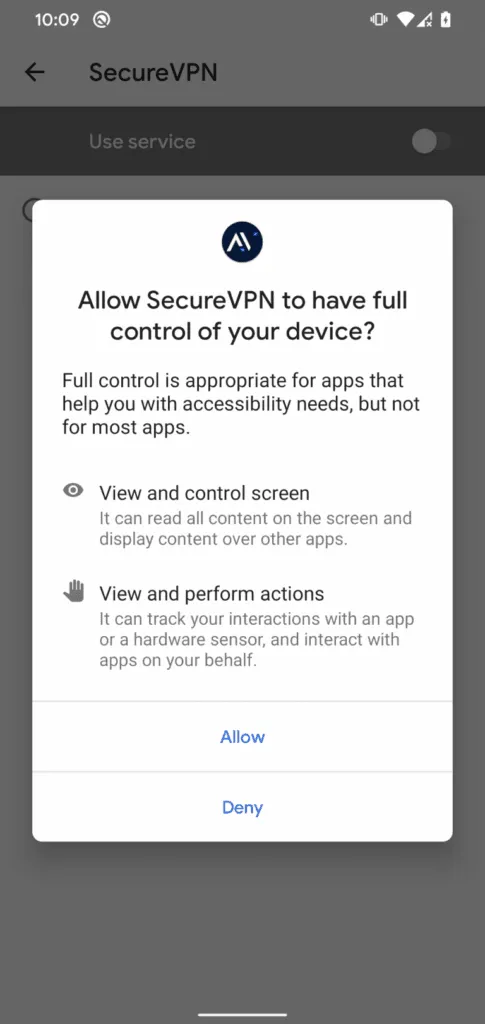
If the spyware is enabled, ESET said it can be controlled remotely by Bahamut operators to exfiltrate any information they want, including a user’s contacts, SMS messages, recorded phone calls, device location and even chat messages from apps like WhatsApp, Facebook Messenger, Signal, Viber, and Telegram.
ESET researcher Lukáš Štefanko said the data exfiltration is done via the keylogging functionality of the malware, which misuses accessibility services.
“The campaign appears to be highly targeted, as we see no instances in our telemetry data. Additionally, the app requests an activation key before the VPN and spyware functionality can be enabled,” he said. “Both the activation key and website link are likely sent to targeted users.”
This function stops the malware from being triggered right after launch on a non-targeted user device or when being analyzed. ESET noted that this is a feature they have seen the Bahamut group use before.
ESET found at least eight versions of these maliciously patched apps with code changes and updates being made available through the distribution website, suggesting the campaign is well maintained.
ESET said the fake SecureVPN website was created based on a free web template that the group made minor changes to in order to make it look legitimate.
“The mobile campaign operated by the Bahamut APT group is still active; it uses the same method of distributing its Android spyware apps via websites that impersonate or masquerade as legitimate services, as has been seen in the past,” Štefanko wrote.
“Further, the spyware code, and hence its functionality, is the same as in previous campaigns, including collecting data to be exfiltrated in a local database before sending it to the operators’ server, a tactic rarely seen in mobile cyberespionage apps.”
The Bahamut APT has long been on the radar of cybersecurity researchers, with dozens of security companies spotlighting their campaigns over the last five years. The group has typically deployed spearphishing messages and fake applications to target organizations and people across the Middle East and South Asia.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



