Android smartphones infected with rare rooting malware
Security researchers at Lookout have discovered a new Android malware strain that contains the ability to root smartphones, a feature that has become quite rare in Android malware strains in recent years.
Named AbstractEmu, the malware and its distribution campaign have been detailed in a report published today, summarized below:
- The AbstractEmu malware was distributed hidden inside 19 Android applications that were uploaded on Google Play, the Amazon Appstore, the Samsung Galaxy Store, and other unofficial third-party app stores.
- Only one of the 19 apps, called Lite Launcher, reached the Google Play Store, where it was downloaded by only 10,000 users.
- Once on a device, the AbstractEmu malware would download and execute one of five exploits for older Android security flaws that would allow it to root and take over the device.
- The rooting package contained exploits for the following five vulnerabilities: CVE-2020-0041, CVE-2020-0069, CVE-2019-2215, CVE-2015-3636, and CVE-2015, 1805.
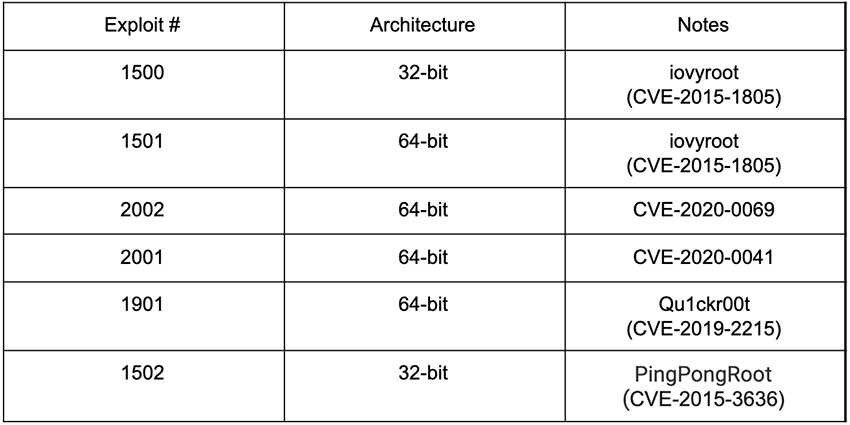
- Once the AbstractEmu malware gains elevated privileges following the rooting exploit, it would give itself access to dangerous permissions, and then access additional malware components on the devices.
- After a device is infected, the following data is collected and sent to a remote server.
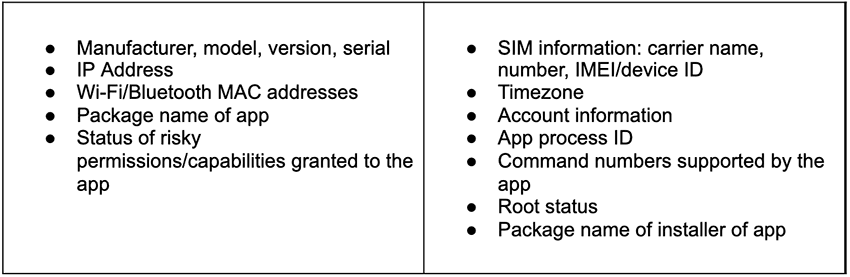
- Lookout said it was unable to determine what malicious operations this malware would carry out but said that based on the permissions the malware assigned itself, there were similarities with banking trojans and spyware-focused threats such Anatsa, Vultur, and Mandrake.
- The company described the malware's creators as a "well-resourced group with financial motivation."
- Lookout said it named the malware AbstractEmu because of its use of code abstraction and anti-emulation checks to avoid running while under analysis and sandboxes.
The names of some of the apps and their installation packages –discovered to contain the AbstractEmu malware– are below:
| Title | Package name |
|---|---|
| All Passwords | com.mobilesoft.security.password |
| Anti-ads Browser | com.zooitlab.antiadsbrowser |
| Data Saver | com.smarttool.backup.smscontacts |
| Lite Launcher | com.st.launcher.lite |
| My Phone | com.dentonix.myphone |
| Night Light | com.nightlight.app |
| Phone Plus | com.phoneplusapp |
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.


