Android malware will factory-reset a phone after stealing a user's funds
An Android banking malware strain has recently received a new feature that allows its operators to reset a device to factory settings after they have stolen money from a victim's bank account as a way to distract the owner from the recent theft and prevent them from taking any preventive measures.
The new feature was discovered by researchers from security firm Cleafy in new samples of the BRATA malware spotted in the wild last month, in December 2021.
Also known as "Brazilian Remote Access Tool Android," the BRATA malware has been around since late 2018 and is one of the many Android banking trojans that has been active over the past few years.
Usually distributed via shady apps offered on equally shady websites, the BRATA gang's tactics are focused on tricking non-technical users into installing these apps and then granting them overly-intrusive permissions over their devices.
Since 2018, the BRATA gang has used this tactic to gain a foothold on Android smartphones, search for e-banking apps, show fake login screens, and then collect the user's banking credentials.
Features added in subsequent versions have also allowed the malware to initiate financial transactions from the compromised devices and steal user funds, and some BRATA-infested apps have also managed to slip into the official Play Store in early 2021.
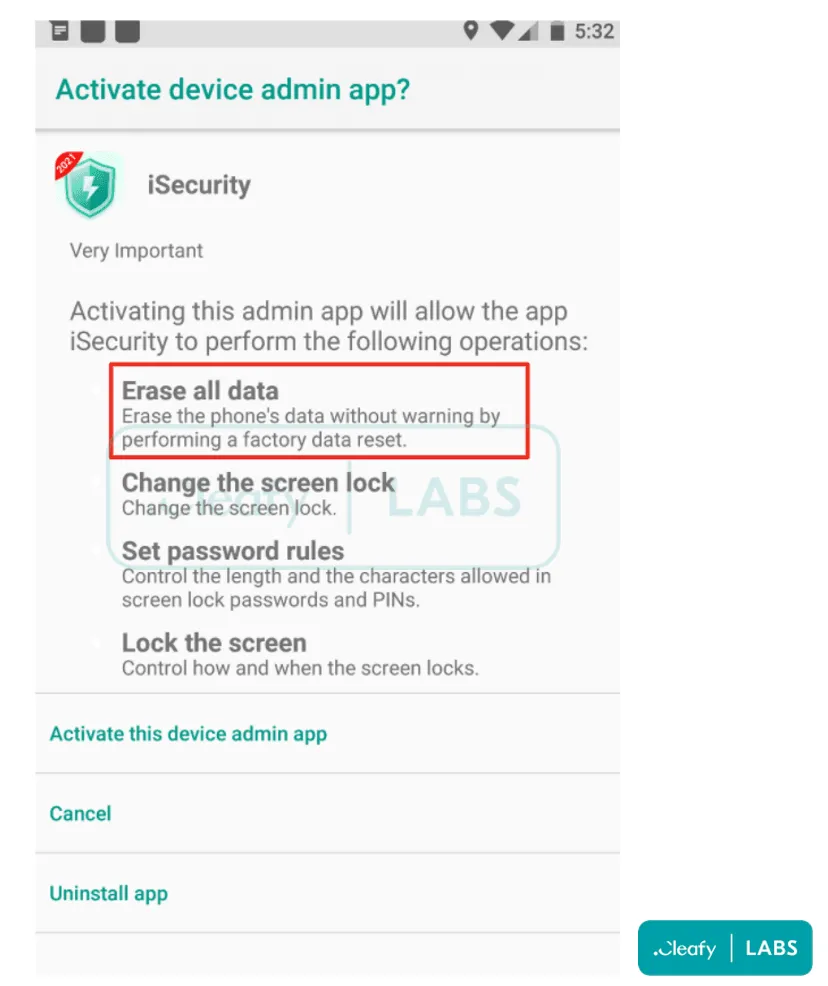
The addition of the forced factory reset feature to new BRATA versions represents a clever addition to prevent victims from getting timely alerts about any suspicious transfer of funds, as the e-banking app would be removed from the device during the factory reset operation.
As device owners would be looking to investigate why their devices lost all their installed apps, many would not think to check the status of their bank account and might not find out about the malicious transfer until days after it happened, giving the BRATA gang time to launder the stolen money.
In addition, the factory reset also removes the malicious app that contained the BRATA trojan, effectively removing any forensic evidence of where the attack might have come from.
But Cleafy researchers said that the factory reset operation could also be triggered automatically during another scenario beyond a successful bank transfer. This includes attempts to run the BRATA trojan in a virtual environment, typically used by security researchers and mobile security tools. In this case, BRATA uses a factory reset to protect itself from a security scan or an attempt to reverse-engineer its code.
Other defensive measures previously used by Android malware
BRATA's factory reset is a unique method used by the malware to protect itself, but it is not the first time that Android malware has done so.
For example, in 2016, an Android banker named Android.SmsSpy would also lock devices by simulating a ransomware-like attack in order to distract users from the fact that their banking credentials were also stolen during the infection.
The same technique was copied weeks later by another Android banked known as the Fanta SDK.
In recent years, Anubis, another Android banking trojan, has also used something similar to BRATA's technique.
"It is not a factory reset but a wipe of user data which has the same impact for users," Cengiz Han Sahin, founder and CEO of ThreatFabric, told The Record today about Anubis' technique.
BRATA also comes with a GPS data collector
But Cleafy said that besides the new forced factory reset feature, recent BRATA samples also included a second new feature, one to collect GPS geo-location data from infected devices.
This, however, appeared to be still in development, according to the Cleafy team.
"As far as we know, this feature is actually requested at installation; however, no evidence in the code is actually used," researchers said. "For this reason, we could just guess that malware developers are requesting this permission for future development, most likely to target people that belong to specific countries or to enable other cash-out mechanisms (e.g. cardless ATMs)."
Cleafy said they spotted these new BRATA malware samples in malicious apps distributed at audiences located in Latin America, Italy, Poland, and the UK.
Sahin, who has also been tracking the same campaign, said the distribution efforts have been small in scale compared to other more active malware threats.
None of the BRATA apps were spotted on the official Google Play Store.
To avoid getting their devices infected by any of the BRATA apps spotted in the wild, Cleafy researchers recommended that users pay attention to what permissions Android apps request during installation and not install apps that request access to the "Erase all data" one.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



