An Interview With Russian Hacker Pavel Sitnikov: ‘There Is No [Hacking] Scene Now, Only Commerce’
Editor’s Note: Hackers often go to great lengths to be discreet. That’s not the case with Pavel Sitnikov.
The long-standing, Russian-speaking hacker until recently posted frequently on Twitter, where he listed his name, his alias (FlatL1ne), and his self-proclaimed connection with the infamous hacking group APT28, or Fancy Bear. In June, he shared a link on Twitter to a sizable archive of leaked data that allegedly consisted of information on hundreds of police departments and fusion centers—his Twitter account is currently suspended.
Sitnikov also manages the Telegram group Freedom F0x, where he shares data leaks, educational materials, and software used for security and penetration testing. Sitnikov, a member of multiple underground communities, also has a history of selling and sharing multiple malware source codes on the dark web, including banking and spam trojans.
Sitnikov talked with Recorded Future expert threat intelligence analyst Dmitry Smilyanets about ransomware, Fancy Bear, and Russian cybercrime. Recorded Future has not uncovered any concrete evidence to confirm Sitnikov’s connection with the Fancy Bear hacking group. The conversation was conducted in Russian via Telegram and was translated to English with the help of a professional translator. The interview below has been lightly edited for clarity.
Dmitry Smilyanets: How did you get into the hacking scene?
Pavel Sitnikov: The same way as everybody else—I registered on the forums. In my case, it was Damagelab (XSS) and Wasm[.]ru. I spent many years reading and chatting there.

DS: Which global cybersecurity threats do you think will be the most dangerous in 2021?
PS: The compromise of government data and even identity theft.
DS: Do you think Western law enforcement might be interested in you? If so, why?
PS: Absolutely, but showing this interest, they give themselves away Why would I be interesting? My extensive business connections, my absolute knowledge of the algorithms of the system in the Russian Federation, etc.
DS: Who added your passport details to the leaked Telegram database? [Editor’s Note: In June, the operator of a public Telegram channel shared that they possessed a database containing sensitive information of 40 million Telegram users, 12 million of which are Russian language accounts.]
PS: Anyone could have added that to the database, you can Google my data with one click. It’s like an Easter egg—just to laugh for those who are even a little bit in the industry.
DS: What’s your beef with Maxim Plakhtiy? Why are you so fiercely against him?
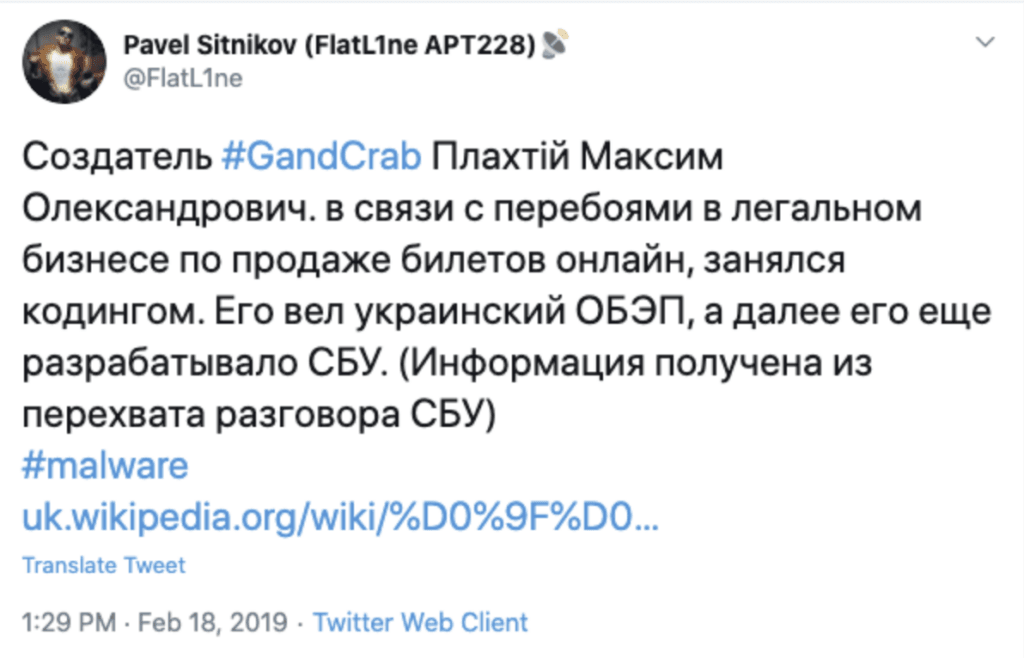
PS: I don’t know Max, nor does he know me. He was mentioned in one of the SBU correspondence, where his life situation was discussed and the reason for the appearance of GrandCrab ransomware was described. Consider these are competitive wars.
DS: Competitive wars? Between different ransomware families, or between special services?
PS: The ransomware and special services are inseparable, like the Hydra marketplace. [Editor’s note: Hydra is a popular Russian darknet marketplace for drugs.]
DS: How do you feel about ransomware attacks?
PS: From a technical point of view, I really like them. It will really force the victims and those who hear about it to think about information security. I am not happy only with the monetization format. It is extortion.
DS: I agree. “Breaking kneecaps” is not very intellectual, but what method of monetization do you like the most?
PS: Ransomware monetization is about changing security policy. Ransomware is an ideal weapon that can be used for peaceful purposes without the consent of those to whom it is directed. For example, in our government, everything is completely fucked up but I’m sure that if someone were to encrypt the infrastructure in one way or another affecting the work of top government officials just twice, the problems would be solved once and for all.
DS: How possible and realistic is it to become a part of the Fancy Bear hacking group, and what would you need to do it?
PS: The “Fancy Bears” group is a general description of attack markers and created by CrowdStrike. Monitor Twitter on the tag “APT” and you’ll get a bit of a surprise.
DS: I know the community is already suffering from the number of APT, or Advanced Persistent Threat, brands. Each cyber threat intelligence company is trying to name the groups in their own way, thereby creating confusion. Why did you call yourself “Fancy Bears” APT228 on Twitter? Article 228 of the Criminal Code of the Russian Federation does not add up to your tactics, techniques, and procedures—it relates to drugs.
PS: As one reputable hacker “090” said: “In Russia, we are all bears, but not everyone is fancy.” APT228 is the way a certain part of the original structure of APT28 was renamed in light of the way some members of the group abused prohibited substances.
DS: In your channel, you offer services for conducting competitive intelligence, information warfare, OSINT, ORM, ORD, etc. Tell me more about this service.
PS: If I provide more details, it will be an advertisement. But I don’t need to advertise. I provide services, both data and a host of other related services.
DS: Why not advertise? You don’t want to work with Western partners?
PS: To be honest, I don’t want to work at all. I have a consulting and training project for the future. And Western “partners”, or rather those who do not speak Russian, are of little interest to me. It’s hard to deal with them.
DS: Who controls the competitive intelligence process so that it does not become industrial espionage?
PS: Espionage is a very serious article. Everyone controls themselves. If you think about it, anyone can be charged with anything. But if you need to support it with tangible evidence, then I always answer like this: “What documents do you need? A pack of paper is 90 rubles.” [Editor’s Note: In other words, everything has a price.]
DS: You leak databases of Russian banks on your channel. How is this even possible?
PS: This data is obtained either from the banks themselves, or fraudulently by various cybercriminal groups or researchers. Either sold or leaked publicly. As long as the knowledge about the leak is hidden and not publicized, people affected by the leak continue to suffer. As soon as it is announced, the most important thing is that at least for the moment those who are mentioned in the leak think about their security.
DS: Who in your opinion is the most prominent Russian hacker, and why?
PS: ms-rem, for his ideological consistency.
DS: Tell me a secret—where did you hide RedBear?
PS: Secretly, nowhere. Super-secret, secret, we don’t really know each other. Well, super-duper secret, he just started drinking.
DS: Why don’t you invite me to your private groups?
PS: Let’s start with the fact that they are paid groups. Second, there is nothing for you specifically to do there.
DS: Why? Do you think I am not qualified enough?
PS: I’m not thinking about the qualification. Actually, there’s nothing for anyone to do in there. Seriously.
DS: What’s the proudest moment in your career?
PS: Honestly, I don’t see it as a career. I just do what I can and what I like to do.
DS: How would you describe the Russian hacking landscape these days? How has it changed over the last five years?
PS: There is no scene now, only commerce. Everything changed in 2000 since everyone became financially motivated.
DS: In the early 2000s, Russian special services didn’t pay attention to the hackers. Has anything changed in 2020? Does the Russian government use freelance hackers to get the necessary jobs done?
PS: They didn’t know about the existence of the internet back in the 2000s. Even now, they don’t really know how to interact with this social group. The approach our special services use to interact with talented guys is like a chapter of the “operational work” book going back to the 1980s.
DS: Do you have anything to say about the recent SolarWinds breach?
PS: It was as beautiful as if it were directed by Stanislavsky.
Dmitry Smilyanets
Mission-driven and Russian-speaking intelligence analyst with type A personality. Dmitry has twenty years of experience and expertise in cybercrime activity that includes being a former member of an elite Russian-based hacking organization.


