ALTDOS hacking group wreaks havoc across Southeast Asia
For the past eight months, a cybercrime group calling itself ALTDOS has been wreaking havoc across Southeast Asia, hacking companies left and right, in order to pilfer their data and ransom it back or sell it on underground forums.
First spotted in December 2020, the group has been linked to intrusions at companies in Bangladesh, Singapore, and Thailand.
According to a series of government cybersecurity alerts and reporting done by DataBreaches.net, which has had extensive direct contact and conversations with the group, ALTDOS' modus operandi can only be described as chaotic.
In some past instances, the group has been seen deploying ransomware to encrypt a victim's data, while in others, they only resorted to stealing sensitive information.
Additionally, in some cases, the group engaged with victims and demanded ransom payments, while in others, the group did not bother and simply auctioned or released the victim's data for free online.
The size of the ransoms has also been smaller when compared to the Russian-speaking ransomware gangs that sometimes extracted multi-million-dollar payments from their victims.
"In the past, they have not asked for the kind of exorbitant ransoms other threat actors have demanded, and in some cases, as we see above, they wind up not making any financial demands at all and just leak the data or advertise it as being for sale," Dissent, a reporter for DataBreaches.net, described the group's operations in a June 2021 blog post.
These smaller ransoms appear to have allowed more victims to pay. ALTDOS told DataBreaches.net that around 70% of their victims pay the ransom demand, and the hack is never made public.
ALTDOS targets outdated Apache web servers
With the group continuing to make new victims as recently as this month, Singapore officials have released an advisory today detailing the group's most common tactics.
Per this extensive report, ALTDOS intrusions typically occur after the group exploits a vulnerability in a public-facing web service, with their most common target being Apache web servers.
Once they gain an initial foothold, the group deploys backdoors to establish persistence and then deploys the Cobalt Strike penetration-testing framework to expand their access to other systems.
After the group exfiltrates a victim's data, ALTDOS has also been seen wiping disks in order to remove forensic evidence.
Once the intrusion has reached its final phase, if the group has not deployed the ransomware, they often use emails to contact victims and demand a ransom payment.
If victims don't pay, the data is often leaked online. In the case of larger companies, the ALTDOS group also utilizes DDoS attacks in order to put additional pressure and remind the victim to pay the ransom.
While the true extent of its operations is still a mystery, some of the group's largest intrusions that have been documented online include the likes of:
- Country Group Securities (CGSEC) - a Thai financial and stock market company (Dec 2020).
- Mono Next Public Company Limited - a Thai mass media company (Jan 2021).
- Bangladesh Export Import Company Limited (BEXIMCO) - a multinational conglomerate (Jan 2021).
- 3BB - an internet service provider in Thailand (Jan 2021).
- Vhive - a popular retail furniture chain in Singapore (Mar 2021).
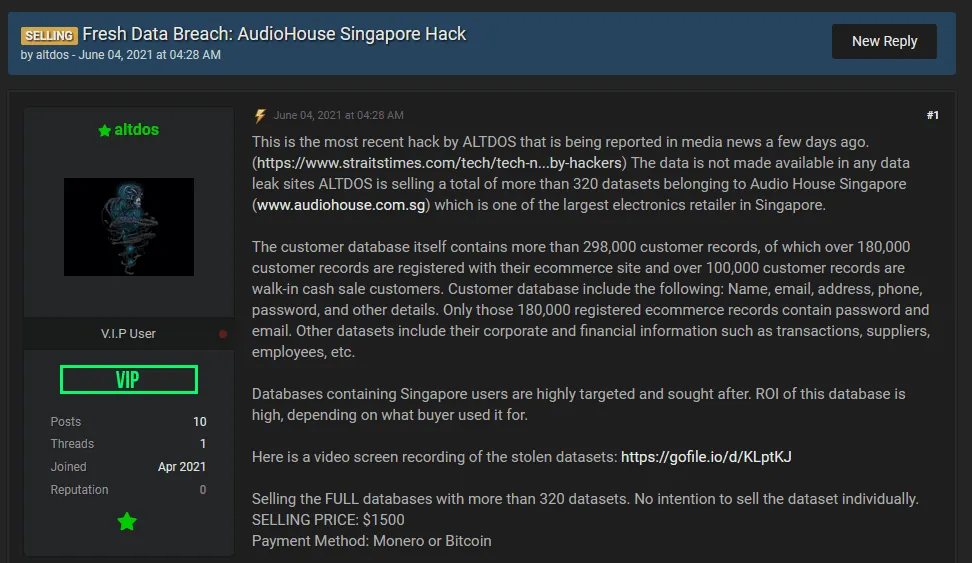
- Audio House - a consumer electronics retailer in Singapore (June 2021).
- Unispec Group Singapore - a company operating in the marine industry, based in Singapore (June 2021).
- OrangeTee - a Singapore-based real estate firm (Aug 2021).
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



