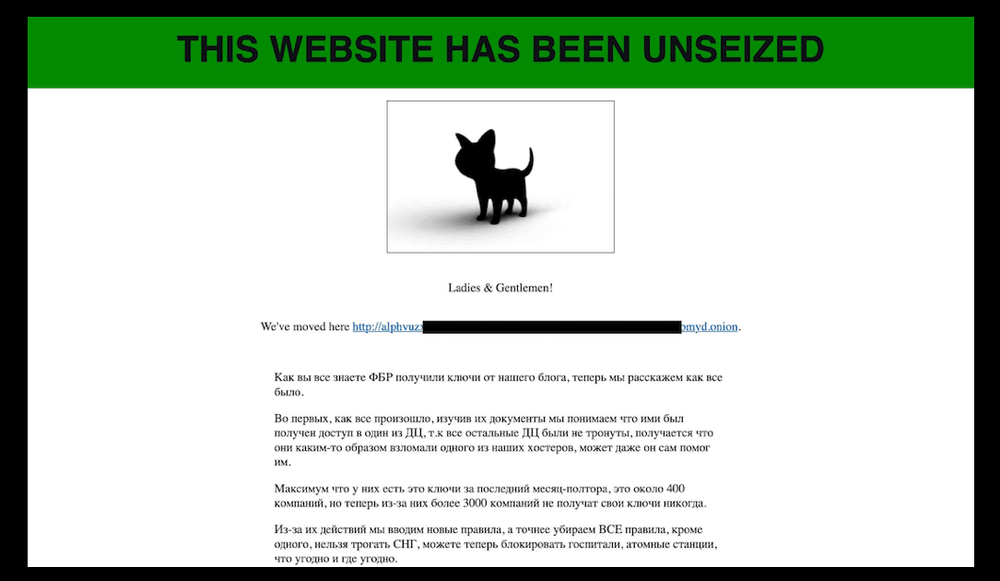
AlphV claims to have ‘unseized’ its darkweb domain from the FBI. What’s happening?
Shortly after the AlphV/Blackcat ransomware gang’s website was replaced on Tuesday by a splashpage announcing it had been seized by the FBI, the law enforcement message was itself replaced by another missive from the criminals claiming to have “unseized” the page and brought it back under their control.
The aggressive message from AlphV said that because of the FBI’s actions it was removing rules it had previously set for affiliates prohibiting them targeting “hospitals, nuclear power plants” and similar institutions, as long as these were located outside of the Commonwealth of Independent States — areas from the former Soviet Union.
At least, that’s what some people observed. Others visiting the website, including Recorded Future News, saw the same FBI splashpage as had been uploaded before and could not see the criminals’ new notice.
So what’s actually happening? Experts who spoke to Recorded Future News suggested that behind the scenes, law enforcement and the ransomware gang may be battling to demonstrate who is really in control of the domain.
The issue is that the website AlphV listed its victims on was run as an onion service, a specialized type of anonymous website that can only be accessed over the Tor network.
Unlike the addresses for normal websites — which are arbitrary and don’t reflect anything about their network location — the address for an onion service is a public key, a string of 56 randomly generated characters.
As Steven Murdoch, a professor of security engineering at University College London and a longstanding member of the Tor Project, explained to Recorded Future News, this means that .onion domains don’t resolve in a similar way to normal websites — where the human-readable address (therecord.media) is linked by the Domain Name System to a machine-readable address (172.64.155.75) that locates the server.
“The way that domain resolution works for onion services is through a distributed hash table (DHT),” explained Professor Murdoch, where the party that can demonstrate their control of the .onion address — the public key — because they own the private key, can submit an entry to the Tor network to send traffic to the address.
But, as the FBI search warrant unsealed on Tuesday reveals, law enforcement was able to identify and collect 946 public/private key pairs from AlphV/Blackcat that the ransomware group used to operate its various onion services, including affiliate panels, leak sites, and sites for victim communications. Affiliates are effectively the clients in the ransomware-as-a-service business model.
“If there are multiple people with the private key corresponding to the domain name, the last one to submit their entry will win. It could be that the ransomware group has set up their Tor server to more aggressively submit their entry into the DHT. However law enforcement has the private key too, so could play their own tricks in response,” explained Murdoch.
These tricks could involve law enforcement pushing its own entry even more aggressively than the ransomware gang, “which could result in a denial of service for the onion service and possibly other onion services,” he explained.
“They could also run a man-in-the-middle attack (since they control the private key). The original address of the site has now been compromised so the safest thing for visitors to the site to do is to never go there again. Encouraging people to continue to use the compromised domain name is a risky suggestion,” the professor added.
‘Tug of Tor’
Rafe Pilling, the director of the Secureworks Counter Threat Unit, wrote on LinkedIn that “a ‘tug of Tor’ is going on for control of the onion sites,” noting that both the ransomware group and FBI were in possession of the private key to control these services.
Allan Liska, a ransomware expert at Recorded Future, said on social media that “it will surprise no one to learn that AlphV are lying pieces of shit. They didn’t ‘unseized’ anything. The way .onion addressing works is that, as long as you have the signing key, if you register a second server with that address the newest server will be believed by default.” The Record is an editorially independent operation of Recorded Future.
Murdoch suggested it could be possible to “probe the servers that are currently looking after the entries for this domain name, and then look for this changing too often (it should be changed every 1 to 2 hours),” as evidence that law enforcement and the ransomware gang were currently battling over whose entry was being prioritized by the Tor network.
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79