ALPHV (BlackCat) is the first professional ransomware gang to use Rust
Security researchers have discovered this week the first professional ransomware strain that was coded in the Rust programming language and was deployed against companies in real-world attacks.
Discovered by security researchers from Recorded Future and MalwareHunterTeam, the ransomware is named ALPHV (or BlackCat).
The ransomware is technically the third ransomware strain written in Rust after a proof-of-concept strain was released on GitHub in 2020 and an experimental and now-defunct strain named BadBeeTeam was also seen later in the same year.
But while they were first, ALPHV (BlackCat) is the first one to be created and deployed in the wild by what looks to be a professional cybercrime cartel.
ALPHV (BlackCat) is advertised on underground forums
In a threat actor profile published today, Recorded Future analysts said they believe the ALPHV (BlackCat) author was previously involved with the infamous REvil ransomware cartel in some sort of capacity.
Following REvil's model, since early December, this individual—also going by the name of ALPHV—has been advertising a Ransomware-as-a-Service (RaaS) of the same name on two underground cybercrime forums (XSS and Exploit), inviting others to join and launch attacks against large companies to extract ransom payments they can then divide. Those who apply, known as "affiliates," receive a version of the ALPHV (BlackCat) ransomware they can use in attacks.
Among the features they advertise is the ability to encrypt data on Windows, Linux, and VMWare eSXI systems, and the ability for "affiliates" to earn between 80% and 90% of the final ransom, depending on the total sum they extract from victims.
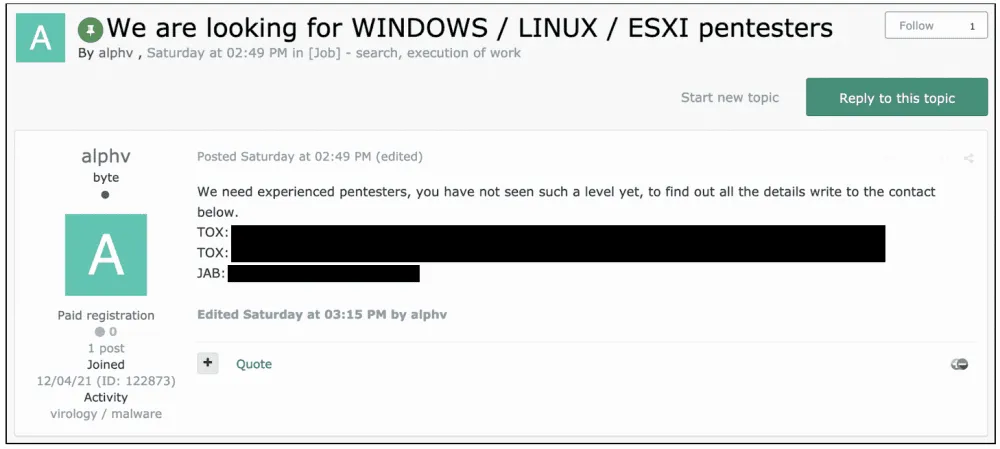
At the time of writing, the ALPHV (BlackCat) gang appears to be in its early stages of operations and MalwareHunterTeam has told The Record that only a handful of victims have been identified so far.
The BlackCat gang's preferred initial entry vector is currently unknown, but once they breach a network, they search and steal sensitive files and then encrypt local systems.
In tune with the tactics of most major ransomware operations today, the group also engages in double-extortion, where they use the stolen data to put pressure on victims to pay, threatening to leak the stolen data if they don't.
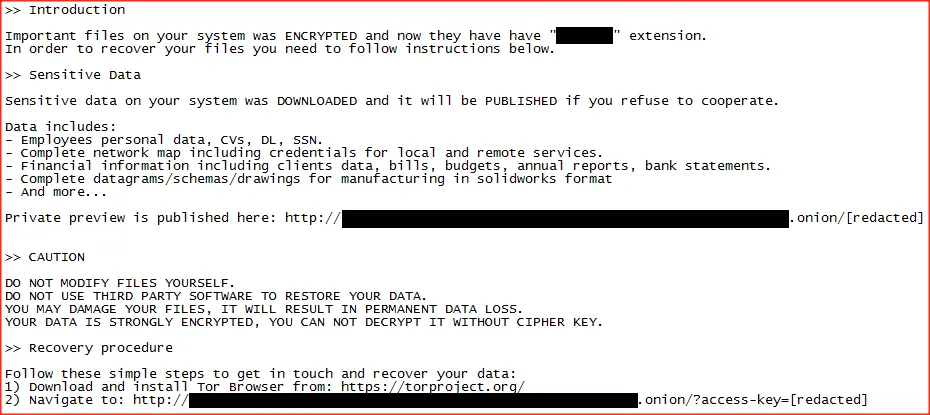
BlackCat/ALPHV ransom note (Image: MalwareHunterTeam)
Right now, the group seems to be operating multiple leak sites, with each of these hosting the data of one or two victims, with ALPHV (BlackCat) creating a new one to use in new attacks. A screenshot of one of these sites is below.
A theory is that these leak sites are currently being hosted by the ALPHV (BlackCat) affiliates themselves, which explains the different leak URLs.
BlackCat (ALPHV) leak site (Image: The Record)
Malware world slowly moving to Rust
While there have been some other tentative attempts at creating ransomware in Rust last year, BlackCat is the first one that is an actual threat and which companies need to be wary of.
In a tweet yesterday, Michael Gillespie, a malware analyst at Emsisoft and the author of tens of ransomware decryption utilities, has described BlackCat as "very sophisticated."
However, BlackCat is not the only professional malware operation to move to Rust, considered a much secure programming language compared to C and C++.
Other cybercrime groups, such as the operators of BuerLoader and FickerStealer, have also made the first steps in 2021 towards deploying Rust versions of their tools.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.


