Akira ransomware compromised at least 63 victims since March, report says
The recently discovered Akira ransomware is actively targeting small and medium-sized businesses around the world, with the main focus on the U.S. and Canada, researchers say.
Akira was discovered in March 2023 and has since compromised at least 63 victims, according to a report published Wednesday by the U.S. cybersecurity company Arctic Wolf.
The researchers also found more evidence linking the Akira group to threat actors affiliated with the notorious ransomware Conti operation.
Arctic Wolf analyzed cryptocurrency transactions related to Akira and Conti, and found that in “at least three separate transactions, Akira threat actors sent the full amount of their ransom payment to Conti-affiliated addresses.”
When cryptocurrency wallets overlap like that, it’s a sign that “the individual controlling the address or wallet has either splintered off from the original group or is working with another group at the same time,” Arctic Wolf said.
The researchers noted that Akira is offered as ransomware-as-a-service, meaning that the group maintaining the code might not be responsible for every attack.
How it works
Akira commonly infiltrates targeted Windows and Linux systems through VPN services, especially where users haven't enabled multi-factor authentication.
To gain access to victims’ devices, attackers use compromised credentials, which they most likely acquire on the dark web.
Once a system is infected with Akira, the malware attempts to delete backup folders that could be used to restore lost data. Then, the ransomware encrypts files with certain extensions and adds the “.akira” extension to each of them.
The hackers’ ransom note is written in English but contains many mistakes. The group claims that it doesn’t want to cause severe financial harm and will determine ransoms based on a victim's income and savings. The hackers also offer guidance on using cyber insurance for those who have it.
The group’s ransom demands range from $200,000 to over $4 million.
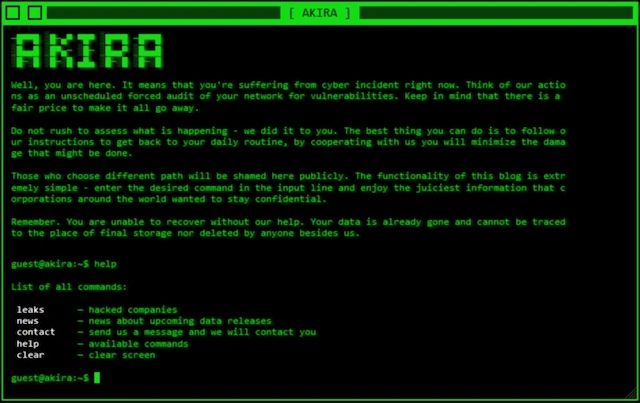 Akira's homepage on the dark web. Image: Arctic Wolf
Akira's homepage on the dark web. Image: Arctic Wolf
According to a BleepingComputer report published in May, each Akira victim has a unique negotiation password that is entered into the threat actor's site on the dark web. Akira offers victims the opportunity to pick and choose what they would like to pay for, according to Arctic Wolf.
The group promises to restore access to victims' data within 24 hours after receiving the ransom payment. “If we fail to agree, we will try to sell personal information/trade secrets/databases/source codes to multiple threat actors at once,” the ransom note says.
Conti links
Since the Conti ransomware source was leaked last year, attribution back to the group via code overlap has become more difficult. For now, Akira ransomware is similar to Conti’s ransomware in many ways, researchers say. It ignores the same file types and directories and uses a similar encryption algorithm.
Back in June, researchers from Avast Threat Labs revealed similar findings concerning Akira's connections to Conti, stating that the creators of the malware “were at least inspired by the leaked Conti sources.” The cybersecurity company released a decryptor for the ransomware earlier this month.
Arctic Wolf focused on blockchain analysis, finding that in the three suspicious transactions it observed, Akira ransomware users paid over $600,000 in total to Conti-affiliated addresses.
Two of the Conti-affiliated wallets were associated with Conti's leadership team, with one receiving payments from multiple ransomware families, Arctic Wolf said.
Akira continues to evolve and grow by changing its tactics to evade detection.
The group has taken credit for several high-profile incidents — including attacks on the government of Nassau Bay in Texas, Bluefield University, a state-owned bank in South Africa and major foreign exchange broker London Capital Group. Last week, the group added Yamaha’s Canadian music division to the list of its alleged victims.
Earlier in July, India's computer emergency response team (CERT-In) issued a security alert cautioning internet users about Akira.
Daryna Antoniuk
is a reporter for Recorded Future News based in Ukraine. She writes about cybersecurity startups, cyberattacks in Eastern Europe and the state of the cyberwar between Ukraine and Russia. She previously was a tech reporter for Forbes Ukraine. Her work has also been published at Sifted, The Kyiv Independent and The Kyiv Post.