Ad-Blocker Company Releases List of 6K Trackers Abusing CNAME Cloaking
Ad-blocker and privacy software maker AdGuard has published today a list of online trackers that abuse the CNAME cloaking technique to bypass browser privacy defenses and track users across the internet.
The list, made available on GitHub, is the largest and most comprehensive of its kind, allowing users to deploy defenses against a technique that has been slowly adopted by an increasing number of web analytics companies to track users as they move across the internet.
What is CNAME cloaking
Named CNAME Cloaking, the technique abuses CNAME. Standing for Canonical Name, CNAMEs are a type of entry inside DNS records that allow a domain to redirect a query to another domain entry.
For example, a CNAME for a.domain.com can be used to redirect DNS queries to b.domain.com. This redirection usually takes place on a DNS server and is invisible to end-users who just receive the IP address of b.domain.com, without knowing that a DNS CNAME-based redirection even took place.
CNAME cloaking became a popular technique with online web analytics and tracking companies in 2020 when browser makers slowly started to deploy built-in ad-blocking and anti-tracking features to their software.
As the number of web users using anti-tracking features increased, online tracking companies adapted by switching to CNAME cloaking. On a website, implementing CNAME cloaking required that website owners create a subdomain such as track.example.org, which silently redirects to the analytics company's main domain (i.e., tracker.com).
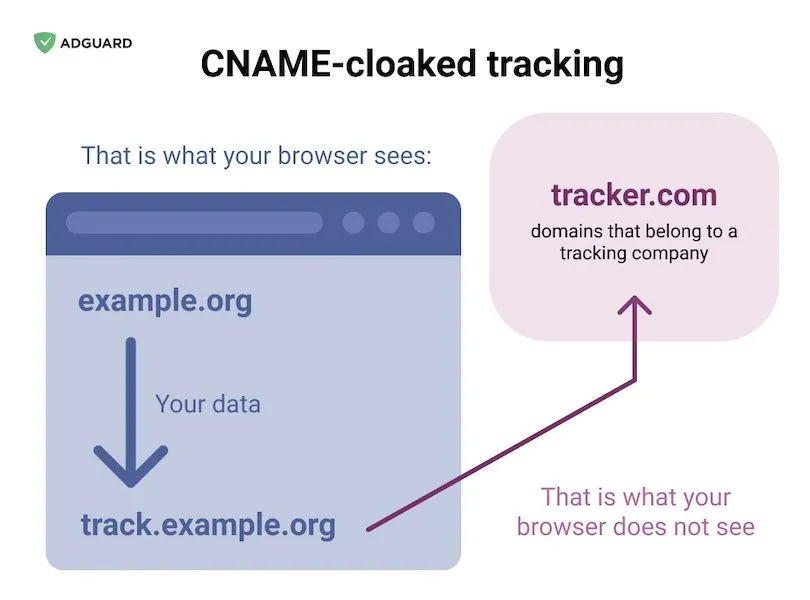
This simple setup allows web analytics firms to load their scripts inside a browser without revealing their real domain to the browser itself, but also to any ad-blocking extension users might be using.
Furthermore, as a side-effect of loading tracking scripts via a subdomain on the main website, the tracking scripts are now also considered first-party content instead of third-parties.
This allows online trackers to bypass even more browser security defenses along the way, such as their ability to create tracking cookies, which are normally third-party content and are to be limited inside major browsers throughout 2020 and 2021.
But even worse, CNAME cloaking doesn't just allow analytics firms to bypass current and upcoming limitations around third-party content but also potentially exposes users to rogue companies that may choose to retrieve first-party cookies from users' browsers in order to bolster their tracking databases, exposing users to even more broad privacy and security issues.
However, even if tracking companies don't intentionally request first-party cookies from the browsers themselves, in most cases, the website will leak cookies on its own, according to a recent study that analyzed CNAME cloaking usage across the web and found that 95% of the websites using CNAME schemes also leaked cookies on their own.
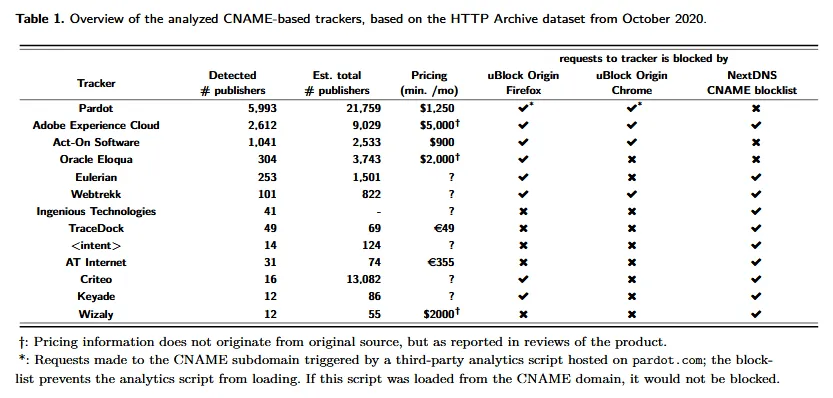
The same study was also able to identify the companies that deploy the most CNAME-based trackers. The list includes names such as Salesforce's Pardot, Adobe's Experience Cloud, and Oracle Eloqua.
List to be updated going forward
To counter the increasing adoption of CNAME cloaking, AdGuard told The Record today that they've used their DNS infrastructure to scan the internet over the past few weeks for websites that abuse CNAME cloaking to disguise ads and tracking scripts.
The results of their findings have been integrated into the company's ad blocker software but have also been made available online, to everyone, as a free download.
The list can be imported into other ad blockers or into privacy software like the Pi-hole to upgrade users' protections against this new rising trend in ad-block skirting.
AdGuard said it also plans to keep the list up to date going forward. The company's commitment is laudable since there's been little movement on the browser vendor part to counter these recent developments in the web analytics market.
Currently, only Firefox and Brave provide tools for detecting and blocking CNAME cloaking, but the vast majority of Chrome and Chromium-based browsers users are still exposed since the Chromium code still lacks an API to scrutinize DNS requests at the same level as Firefox or Brave.
As for Safari users, they are somewhere in the middle, as the WebKit engine only limits the lifespan of cookies created via CNAME abuse but still allows them, even if with a shorter life.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.